MemDive’s Innovative AI Fights Evasive Malware with Dynamic Memory Extraction
In the ever-evolving landscape of cybersecurity, malicious actors continuously innovate to bypass detection. Encrypted malicious payloads remain a preferred method, often rendering traditional security measures ineffective. Enter MemDive, a revolutionary solution using AI algorithms, set to significantly enhance our defense mechanisms against these elusive threats. Security researchers from CheckPoint highlighted this new technique in its blog.
Encrypted malicious payloads have become a sophisticated weapon in a cybercriminal’s arsenal. These payloads are often encrypted to dodge detection tools like antivirus software and firewalls. The aim is simple: remain undetected during static scans. But cybercriminals don’t stop there. To further escape dynamic detection methods, they frequently embed malicious code within genuine processes, ensuring it remains hidden from most antivirus solutions. Another devious technique includes decrypting a small shellcode segment directly into memory, facilitating a covert system backdoor.
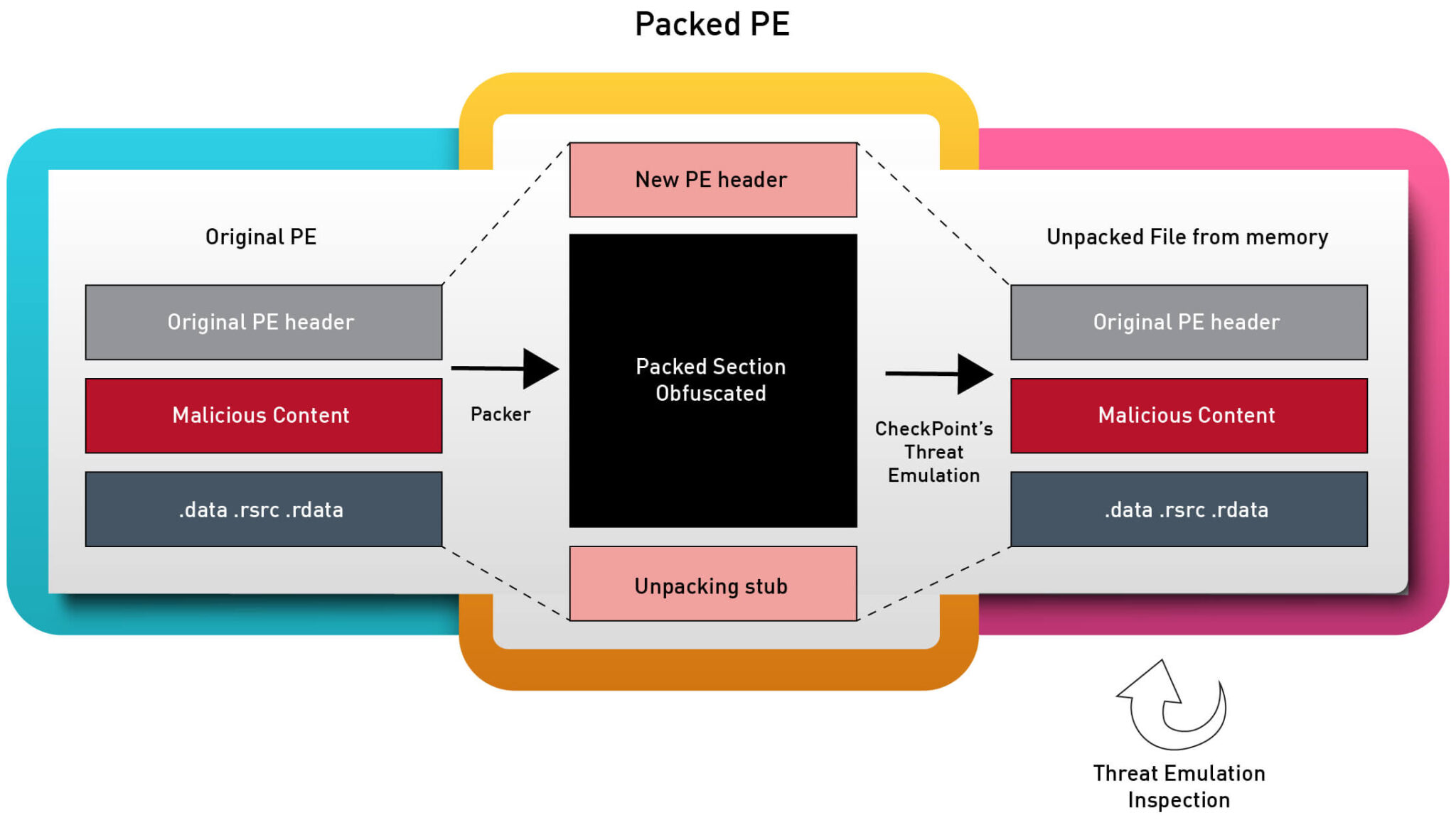
Historically, the Threat Emulation Engine relied on analyzing file structures and behavioral patterns. With MemDive, this has undergone a transformative shift. Using its dynamic memory extraction technique, MemDive intercepts the payload even before its execution. This proactive approach also proves effective against attacks that attempt to erase their traces from memory.
MemDive’s methodology involves constant system memory scans, identifying any alterations or manipulations. Any modifications, including decrypted payloads, are promptly extracted for an in-depth analysis. What sets MemDive apart is its capability to present the status of a file’s running process memory. Moreover, it can rebuild and mend files utilizing the Portable Executable format.

memory extraction process | Image: Checkpoint
A real-world case illustrates MemDive’s prowess. Dynamic memory extraction not only identifies relevant memory sections during runtime but also nearly replicates the original binary the attacker intended to execute. This fine-tuned detection allows for more efficient malicious content identification.
Between June and July 2023, MemDive empowered the Threat Emulation engine to thwart multiple exploits orchestrated using AceCryptor. These attacks involved a complex process of memory manipulation and dynamic decryption to release the final harmful payload.
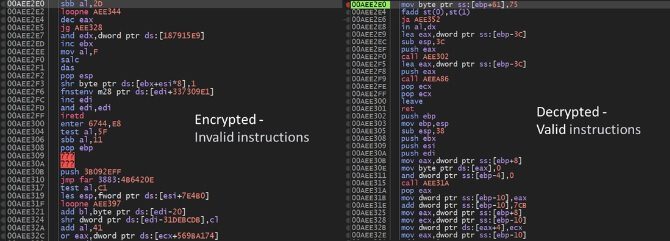
before and after memory extraction | Image: Checkpoint
The payloads detected were recognized as STOP ransomware (alternatively known as KeyPass or Djvu) and the RedLine Stealer. Notably, the cunning evasion tactics employed by these malwares could have rendered them invisible to many behavior-based detection tools.
One particular case highlighted AceCryptor’s shellcode behavior in memory both pre and post-decryption. The left snippet, in its encrypted state, showcased invalid instructions. However, upon decryption during runtime, the malicious code was unveiled on the right, a stark contrast to its original form. This deciphered shellcode was extracted adeptly using MemDive, emphasizing its unmatched efficiency.
In this dynamic battleground of cyber threats, MemDive’s innovative approach provides a promising solution. By harnessing the power of AI and focusing on dynamic memory extraction, it addresses the contemporary challenges presented by encrypted malicious payloads, reaffirming the importance of continuous advancement in cybersecurity.





