metahub v2.5 releases: open-source security tool for context-based security vulnerability management
MetaHub
MetaHub is an open-source security tool for context-based security vulnerability management. It can automate the process of contextualizing and prioritizing security findings based on your environment and your needs, YOUR context. It focuses on understanding context, ownership, and defining an impact for every security finding. You can use it with AWS Security Hub or any ASFF security scanners (like Prowler).
MetaHub describes your context by connecting to your affected resources in your affected accounts and fetching your AWS account configuration, the affected resources tags, your CloudTrail events, your affected resource configurations, but also all their associations: If you are contextualizing a security finding affecting an EC2 Instance, MetaHub will not only connect to that instance itself but also its IAM Roles; from there, it will connect to the IAM Policies associated with those roles. It will connect to the Security Groups and analyze all their rules, the VPC and the Subnets where the instance is running, the Volumes, the Auto Scaling Groups, and more. MetaHub will also connect to the affected account and fetch information like the AWS organization’s policies, security contacts, etc.
After fetching all the information from your context, MetaHub will evaluate certain important conditions for all your resources: exposure, access, encryption, status, age, and environment. Based on those calculations and in addition to the information from the security findings affecting the resource all together, MetaHub will generate a Scoring for each finding.
Check the following dashboard generated by MetaHub. You have the affected resources, grouping all the security findings affecting them together and the original severity of the finding. After that, you have the Impact Score and all the criteria MetaHub evaluated to generate that score. All this information is filterable, sortable, groupable, downloadable, and customizable.

Use Cases
Some use cases for MetaHub include:
- MetaHub integration with Prowler as a local scanner for context enrichment
- Automating Security Hub findings suppression based on Tagging
- Integrate MetaHub directly as Security Hub custom action to use it directly from the AWS Console
- Created enriched HTML reports for your findings that you can filter, sort, group, and download
- Create Security Hub Insights based on MetaHub context
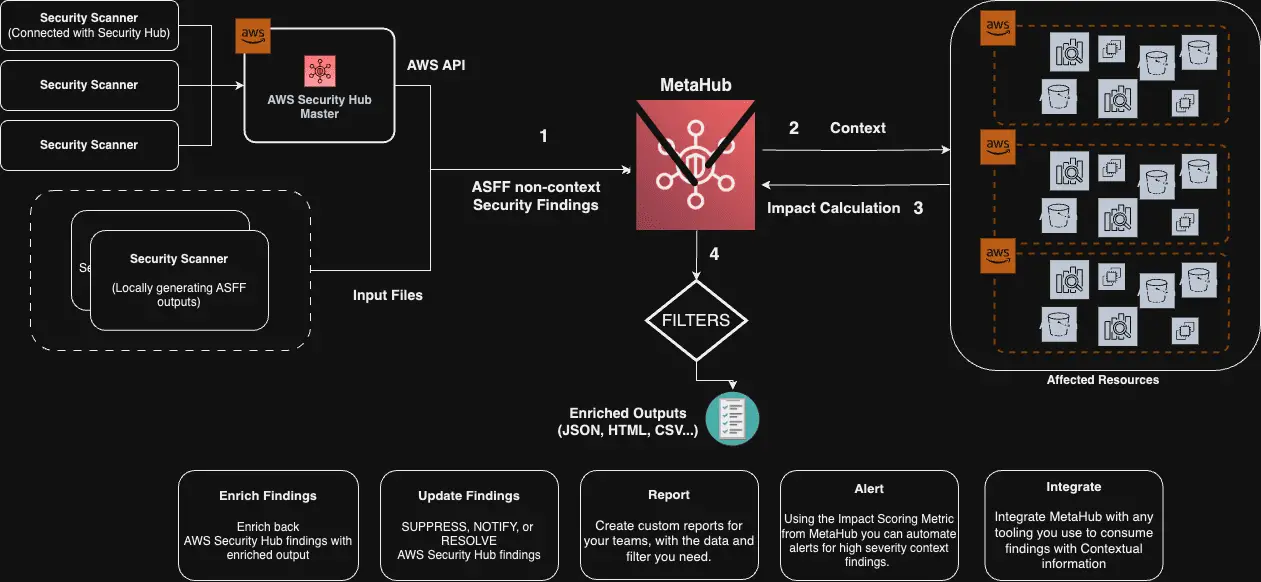
Architecture
MetaHub reads your security findings from AWS Security Hub or any ASFF-compatible security scanner. It then queries the affected resources directly in the affected account to provide additional context. Based on that context, it calculates it’s impact. Finally, it generates different outputs based on your needs.

Changelog v2.5
- improve-elastic-cachche by @gabrielsoltz in #96
- Bump boto3 from 1.34.65 to 1.34.70 by @dependabot in #95
- Bump aws-arn from 0.0.16 to 0.0.17 by @dependabot in #94
- dont-exit-on-errors by @gabrielsoltz in #97
- associations-cache_clusters by @gabrielsoltz in #98
- New SQLite Output and Powerpipe Mod! by @gabrielsoltz in #101
- Bump safety from 3.0.1 to 3.1.0 by @dependabot in #100
- Bump boto3 from 1.34.70 to 1.34.75 by @dependabot in #99
Install & Use
Copyright (C) 2023 gabrielsoltz





