
Photo by John Schnobrich on Unsplash

The term ‘software license compliance’ refers to the use of lawful software. This is something for which both software suppliers and corporate software users must accept responsibility. Otherwise, both suffer the consequences. Fortunately, a little forethought and a few powerful technologies can assist both software firms and their consumers with compliance.
Before we talk about software license compliance, we need to understand software composition analysis.
Software composition analysis (SCA) is a market sector of application security testing (AST) tools that deal with controlling the usage of open source components. SCA tools do automated scans of an application’s codebase, including associated artifacts, like containers and registries, to detect all open source components, license compliance data, and security vulnerabilities.
The process of ensuring that your firm only uses software it is permitted to use is known as software licensing compliance. The essential aspect of this procedure is comparing how a company uses software to the software licenses that have been acquired. This entails keeping detailed records, tracking installations and usage, and comprehending the conditions of software licensing.
SCA tools offer information on each open source component when all open source components have been discovered. This contains information regarding an open source component’s license, attribution requirements, and whether or not the license is compliant with your organization’s rules.
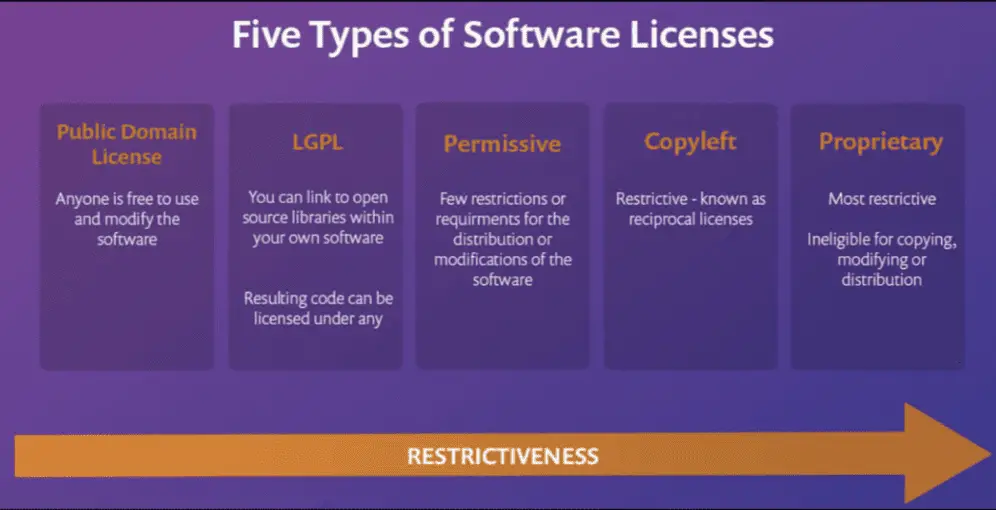
License Types
Public Domain
This is available free of charge to anyone who wants to use it for any purpose. It is available for free study, modification, and repurposing.
Permissive
This software is freely available to the public with just a few limits on how it may be used or certain laws aimed at protecting copyrights and trademarks.
Copyleft
This license type, often known as restricted licensing, specifies how the software can be utilized in new applications. Specifically, any program that contains code from copyleft software must adhere to the same license limitations. For example, if the original program cannot be used commercially, the software that uses it cannot either.
GNU Lesser General Public License
This license enables you to use source code freely. There are certain conditions, though. The program must ensure that the source code has been updated, that it is protected by this license type, and that any software that uses the new code uses LGPL.
Proprietary software
Also known as non-free software or closed-source software, proprietary software is computer software for which the publisher or another individual retains certain rights from licensing to use, modify, share modifications, or distribute the software.
Ways to Ensure Software License Compliance
Make sure you understand the contract’s terms and penalties and understand the definitions of user licenses. It’s important to maintain compliant software usage policies and procedures. As needed, bring in specialists. Keep detailed, up-to-date records of software licensing and usage.
Additionally, create a single point of contact for software license compliance and calculate your actual software discovery coverage. Streamline your software purchase sourcing channels. Perform internal compliance audits on a regular basis. Finally, use a good software composition analysis (SCA) tool.
Enabling SCA is a vital step in ensuring that every one of your applications’ components is safe and compliant. Undiscovered open source use may involve security vulnerabilities waiting to be exploited by malicious actors, as well as licensing compliance issues that may have legal ramifications for your IP, reputation, and bottom line.
SCA tools automatically and continuously detect open source components, identify security and license compliance issues, prioritize risk, and provide development and security teams with the information needed to remediate problems.
Summary
SCA empowers developers by providing them with ownership and visibility into any security flaws concealed in the open source components they use. Given the increased usage of open source in all sectors, scanning for security risks early and frequently in the SDLC helps enhance software engineering productivity, address issues faster, limit interruptions, and better manage people and costs. Software vendors profit from the extra benefit of supplying secure, safe software to their consumers.