Microsoft Alerts of Novel SQL Server-Based Lateral Cloud Movement
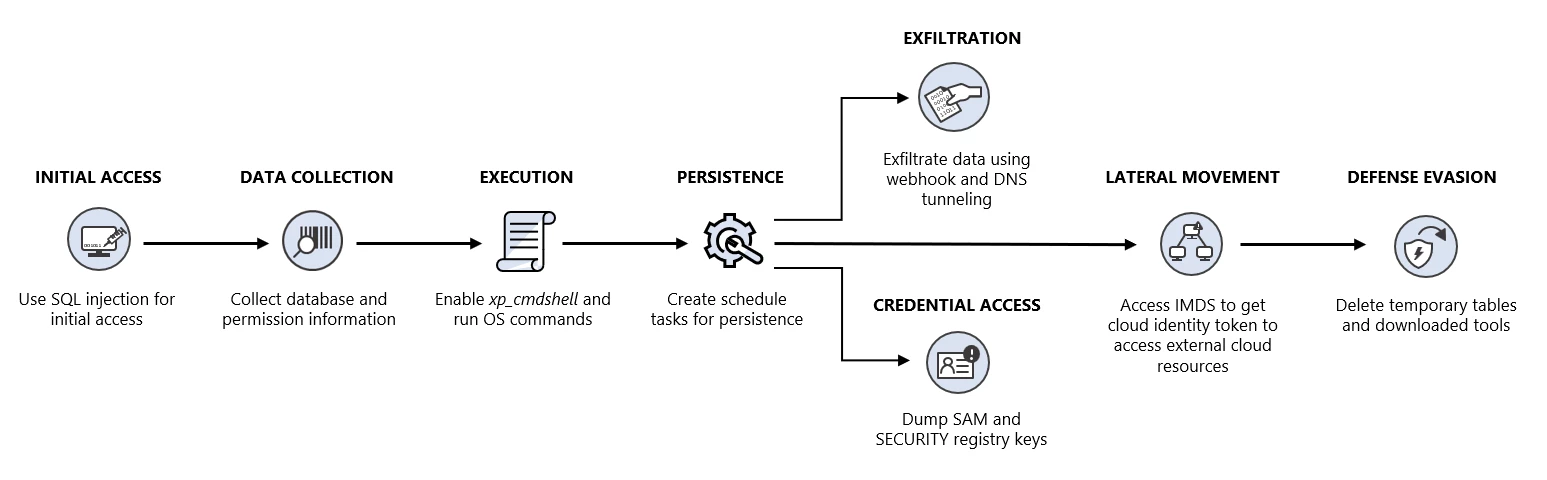
Microsoft’s security team recently uncovered a unique attack technique, demonstrating a new approach for lateral movement from an SQL Server instance to cloud environments. The security landscape is constantly evolving, and this latest discovery serves as a warning to organizations about the sophisticated ways attackers can exploit known vulnerabilities in newer environments.
The attackers began their campaign by exploiting an SQL injection vulnerability in an application, granting them access and elevated permissions on a Microsoft SQL Server instance housed in an Azure Virtual Machine. While SQL injections aren’t new, the subsequent attempt to move laterally through the server’s cloud identity is. Cloud identities, usually integral to cloud services like SQL Server, may hold elevated permissions for actions within the cloud. Thus, the security implications of such an attack cannot be understated.

The vigilant Microsoft Defender for SQL issued multiple alerts, allowing Microsoft to delve deeper into the cloud lateral movement technique. While it seems the attackers did not achieve their end goals, it’s paramount for IT professionals to recognize the novel nature of this threat.
The security team described this campaign as a shift in cloud-based attack strategies, different from conventional on-premises techniques. In the cloud, lateral movement often involves exploiting cloud identities associated with resources. Azure and other cloud services employ managed identities for this purpose. However, these managed identities, despite their convenience and efficiency, can also become avenues for attacks if not properly secured.
In the highlighted attack, upon gaining access through SQL injection, the attackers executed several SQL statements to gather in-depth data about the server’s environment. Capitalizing on what appeared to be elevated permissions, the attackers activated the ‘xp_cmdshell’ command, typically disabled due to its exploitative potential. With it enabled, the attackers were able to execute operating system commands, essentially granting them a shell on the host.
Using simple techniques, the attackers retrieved directories, processes, and network shares, and even downloaded encoded and compressed PowerShell scripts. For persistence, they set up a scheduled task launching a backdoor script, and attempted to harvest credentials.
Interestingly, the data exfiltration method was both novel and discreet. The attackers leveraged “webhook.site,” a public service designed for inspecting and debugging incoming HTTP requests. This approach veiled their actions, making the outgoing traffic appear legitimate.
The most intriguing part of their modus operandi was attempting to harness the cloud identity of the SQL Server instance. By accessing the Instance Metadata Service (IMDS) – a service providing information about a VM – they aimed to procure the cloud identity access key. Though their efforts were stymied due to an error, this tactic underlines the importance of securing cloud identities.
In conclusion, as organizations increasingly migrate to the cloud, understanding the evolving tactics employed by malicious actors is crucial. While the concept of lateral movement isn’t new, its application in cloud environments like SQL Server instances is. These attacks underscore the need for stringent security measures, especially around cloud identities, to safeguard both on-premises and cloud assets. Adhering to the principle of least privilege is imperative, ensuring that applications and resources are equipped only with necessary permissions, thereby shielding them from potential threats.





