Minerva Labs found the first fileless cryptomining malware, GhostMiner
Security researchers from Minerva Labs have discovered a new type of cryptocurrency mining malware that uses PowerShell code to obtain fileless execution capabilities and is able to scan and stop potentially running on the same compromised device. Other miners process.
The so-called “fileless malware” means that the attacker does not need to save the attack tool on the local hard disk of the infected device, but directly stores the attack code in the memory of the infected device to achieve the purpose of the attack. The most common ways for an attacker to achieve this goal are:
- First, download the malicious software to the local hard disk of the infected device, then load it into memory and delete the file from the disk;
- Inject the attack code directly into the memory of the existing process.
The researchers said that although the fileless cryptocurrency mining malware known as “GhostMiner” uses all of these advanced technologies, it has not been able to earn substantial revenue for its developers.
GhostMiner’s mining activities can be described as “failed.” According to the researcher’s description, this mining activity has been carried out for about three weeks, and currently, only 1.03 Monero coins have been earned, valued at around $200.
As mentioned before, GhostMiner may be the first fileless encrypted currency mining malware detected. Not only that, it can also get rid of its competitors – and finally the process of mining other malware.
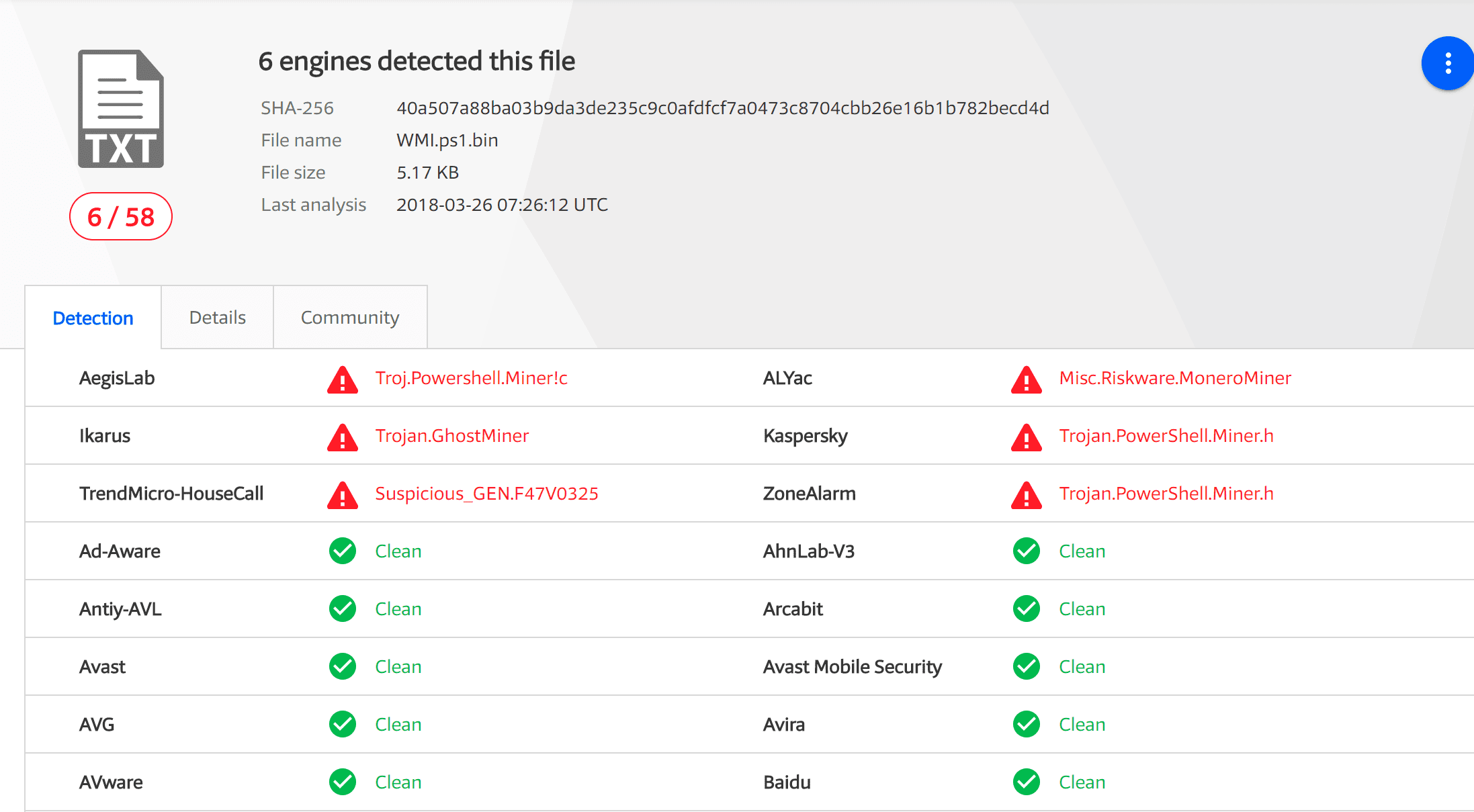
The core activity of the GhostMiner component is performed by the compiled malicious Windows executable. This executable relies on two PowerShell frameworks – Out-CompressedDll and Invoke-ReflectivePEInjection to directly extract the mining program (WMI.ps1) into memory. And will not be found by security products.
It turns out that this technique of evading security detection is very effective. When using this fileless technology, WMI.ps1 doesn’t almost detect by the security product:

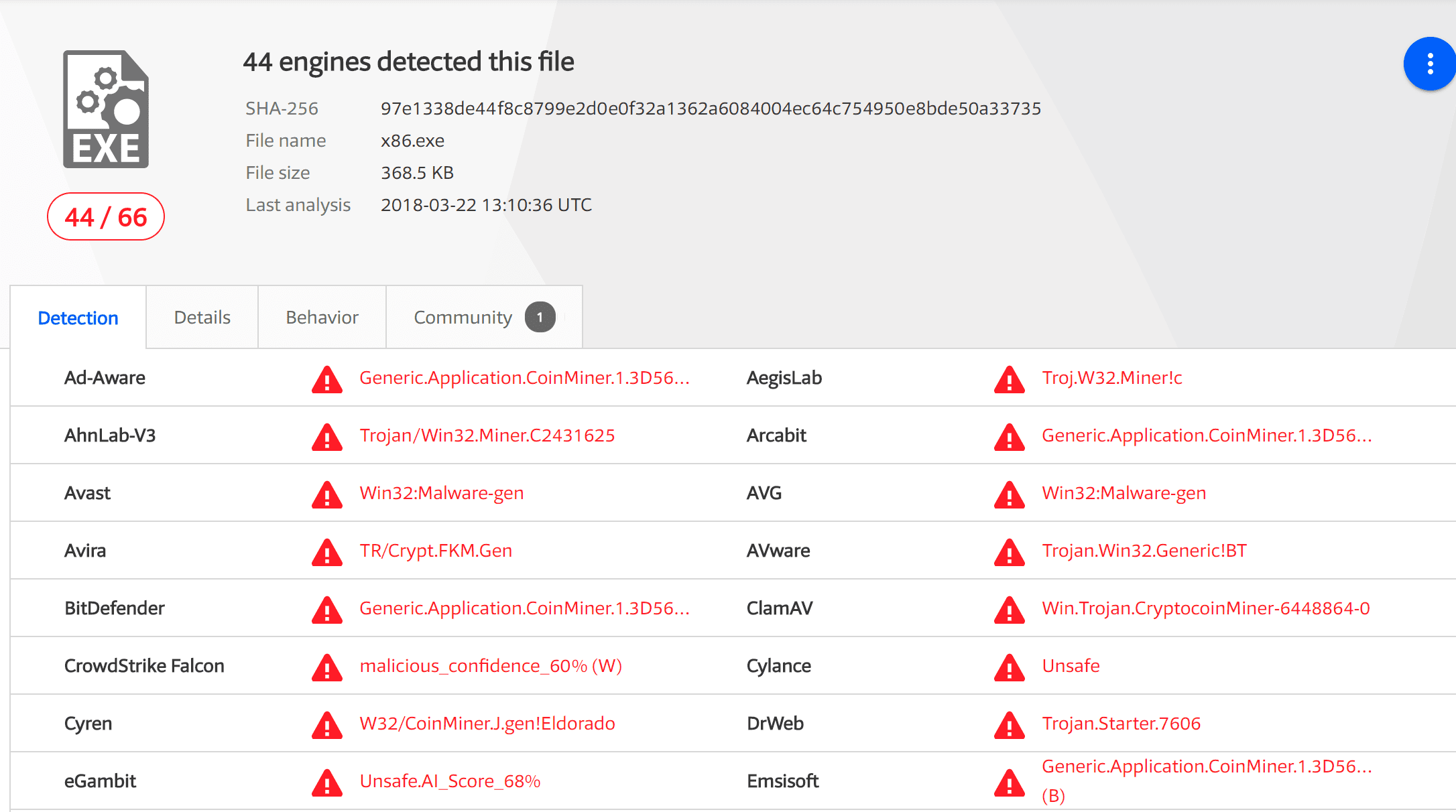
Once this fileless technology is not used, WMI.ps1 is immediately detected by 44 security products:
In addition, although in recent activities, GhostMiner only targets servers running Oracle WebLogic services. But researchers say it can also infect servers running MSSQL and phpMyAdmin.
In an attack against a WebLogic server, GhostMiner randomly scans the IP address, creates a large number of new TCP connections per second, and finally finds a vulnerable target device. After determining the target device, it uses the WebLogic WLS component vulnerability CVE-2017-10271 to establish a foothold on the target device, followed by the use of fileless technology based on the PowerShell framework and the injection of a mining program.
Let’s take a look at how GhostMiner got rid of its competitors. In GhostMiner’s coding, there is a hard-coded blacklist, which no doubt contains some other mining malware known to GhostMiner developers. Once discovered, GhostMiner will use PowerShell’s “Stop-Process -force” command to terminate the running mining process.





