Mint Sandstorm Campaign’s Targeted Cyber Attacks on Middle Eastern Experts
In a recent revelation, Microsoft has uncovered a concerning cyber-espionage campaign conducted by Mint Sandstorm, a notorious threat actor group with links to the Islamic Revolutionary Guard Corps (IRGC) of Iran’s military. Since November 2023, Mint Sandstorm has been meticulously targeting high-profile individuals involved in Middle Eastern affairs, primarily in academic and research circles. Their extensive reach spans across Belgium, France, Gaza, Israel, the United Kingdom, and the United States.
Mint Sandstorm’s modus operandi in this campaign involves highly personalized phishing attempts. The group uses bespoke phishing lures tailored to each target, making it exceptionally challenging for victims to identify malicious emails. Moreover, the threat actors demonstrate remarkable patience and social engineering skills, employing tactics to build trust with their targets.
One standout technique used is the impersonation of high-profile individuals, including journalists, within the target’s network. Mint Sandstorm sends benign emails, sometimes spoofed to appear as personal accounts of the individuals they are impersonating, to engage their targets in discussions related to sensitive topics, such as the Israel-Hamas conflict. This approach aims to establish a rapport with the victims before delivering malicious content, increasing the likelihood of success.

Intrusion chain leading to backdoors observed in the ongoing Mint Sandstorm campaign
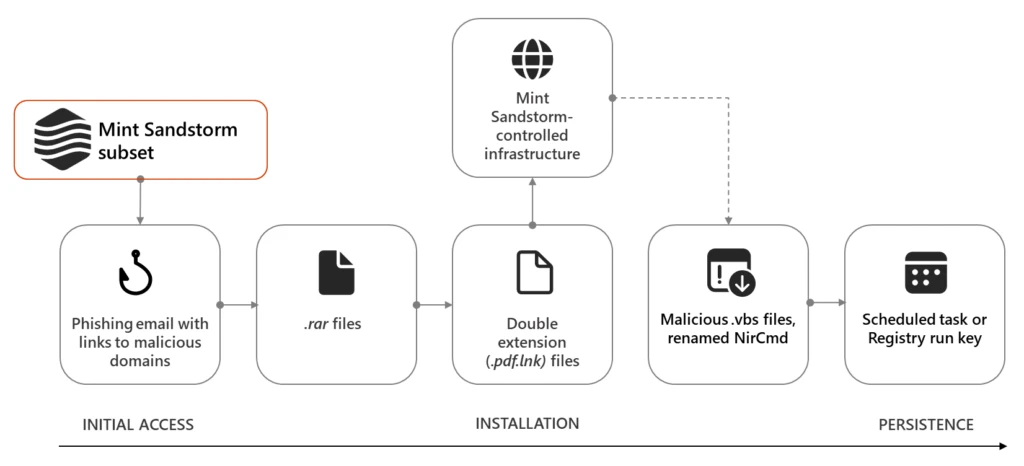
Upon gaining the target’s trust, Mint Sandstorm proceeds to the next phase, delivering malicious content. Victims are directed to seemingly innocuous domains hosting RAR archives. When opened, these archives decompress into files with double extensions, launching a series of malicious downloads from attacker-controlled subdomains.
To maintain persistence within compromised environments, Mint Sandstorm deploys various techniques. They use a custom backdoor named “MediaPl,” masquerading as Windows Media Player. This backdoor is adept at sending encrypted communications to the command-and-control server. Additionally, it can terminate itself, pause and retry communications, and execute commands received from the server, demonstrating a high level of sophistication.
In some instances, Mint Sandstorm deploys a malicious file named “Persistence.vbs” to ensure they remain in the target’s environment. This file adds a registry entry or creates scheduled tasks, ensuring their continued access.
Mint Sandstorm’s primary objective is to gather sensitive information from its targets. They capture activity on the victim’s device, storing it in text files for later analysis. Furthermore, the group deploys custom backdoors like “MischiefTut,” implemented in PowerShell, to execute reconnaissance commands, record outputs, and download additional tools, expanding their control over compromised systems.
The implications of Mint Sandstorm’s activities are significant. The ability to obtain and maintain remote access to targeted systems can result in the compromise of confidential information, creating legal and reputational risks for affected organizations.
Microsoft is actively working to enhance its detection capabilities to protect customers from this persistent threat. They recommend organizations take proactive measures to defend against Mint Sandstorm and similar threats. These include robust email security, training to recognize phishing attempts, and regular updates of security measures.





