Misconfigured NAS Server, Lots of Insurance Customers’ Sensitive Data was Leaked
The loss of customer privacy reminds us of previous information breaches in the credit repair and marketing industry, and the UpGuard cyber risk team now wants to talk about MDJIA’s disclosure case. Is a Maryland state-owned private property insurance company that leaks thousands of customers’ information online due to misconfiguration of storage devices. The data exposure again warns us that highly sensitive personally identifiable information could leak to the web, in which case the data was leaked through the open ports of a networked device.
Exposure to the compromised data store is a backup of the JIA client files and statements, including customer names, addresses, phone numbers, birthdays, social security numbers, checks, bank accounts, and policy numbers. In addition to this important customer information, this leak exposes a series of internal access credentials that were originally used to manage and control the MDJIA association’s operations, including remote desktops, email, third-party usernames, and passwords.
Due to misconfiguration, enterprises are bound to invest enough resources to protect the data. The exposure of the external platform access credentials once again highlights the potential threat of third-party vendors and business partners sharing information.
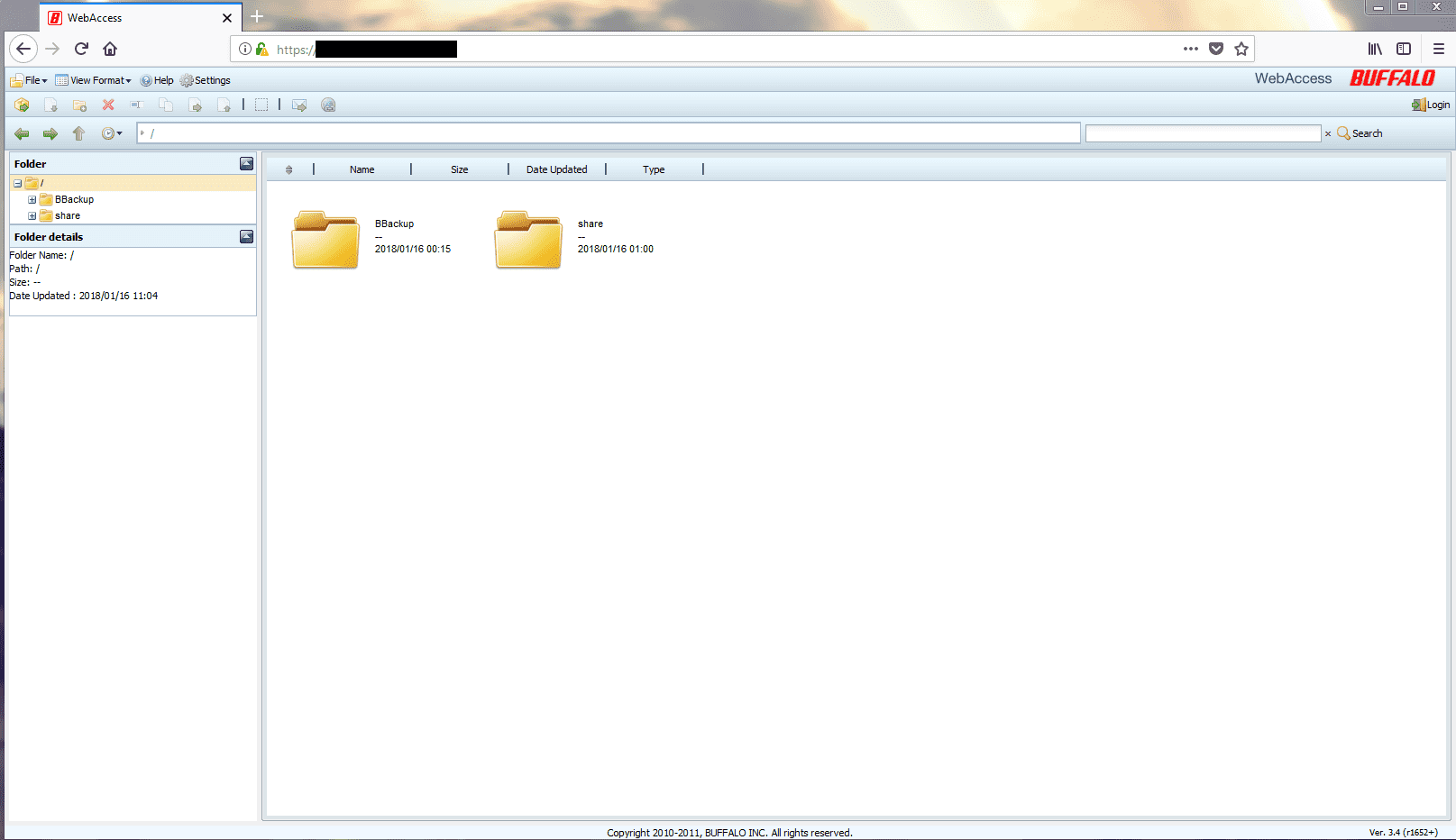
On January 19, 2018, Chris Vickery, director of online risk research at UpGuard, noticed MDJIA because he discovered a networked storage (NAS) device belonging to the insurance association. The device is connected to the Internet through an open port that contains key and sensitive data related to the IT operations of the Association. The data is split into two parts – Backup (the environment with a large number of insurance clients and claimant data) and Share (including vouchers and more A folder of internal administrator data).

The BBackup and Share folders.
An in-depth understanding of the Association’s operations is based on the data exposed, which is part of Maryland and, like similar organizations in other states was formed through the federal FAIR (Fair Assurance Requirements) program.
What is FAIR’s property insurance policy? How do organizations like MDJIA meet their needs? The purpose of the FAIR policy is to protect the owner of the property with claims from policyholders, or those who live in areas prone to natural disasters. Many of these property owners are considered by the insurer to be unqualified applicants because they do not meet the requirements of a policy and are over-insured. Thus, the FAIR policy provides an acceptable basic category of insurance for those who are easily rejected by insurance companies. Although a statewide insurance association like MDJIA is not a public agency, the state government has covered the coverage of the FAIR’s Market Share Program, a private equity fund, and its revenue must be returned to the project. The association is voluntarily formed by insurers in all markets, all licensed and also involved in writing Maryland’s basic, homeowner and multi-risk property risk provisions.
In Maryland, this means that all state insurers in the state have to contribute to the JIA association, which in turn helps property owners who are vulnerable to denial. Unfortunately, after the exposure of a backup subfolder called Live, thousands of such vulnerable customers are also exposed from this unprotected storage device.
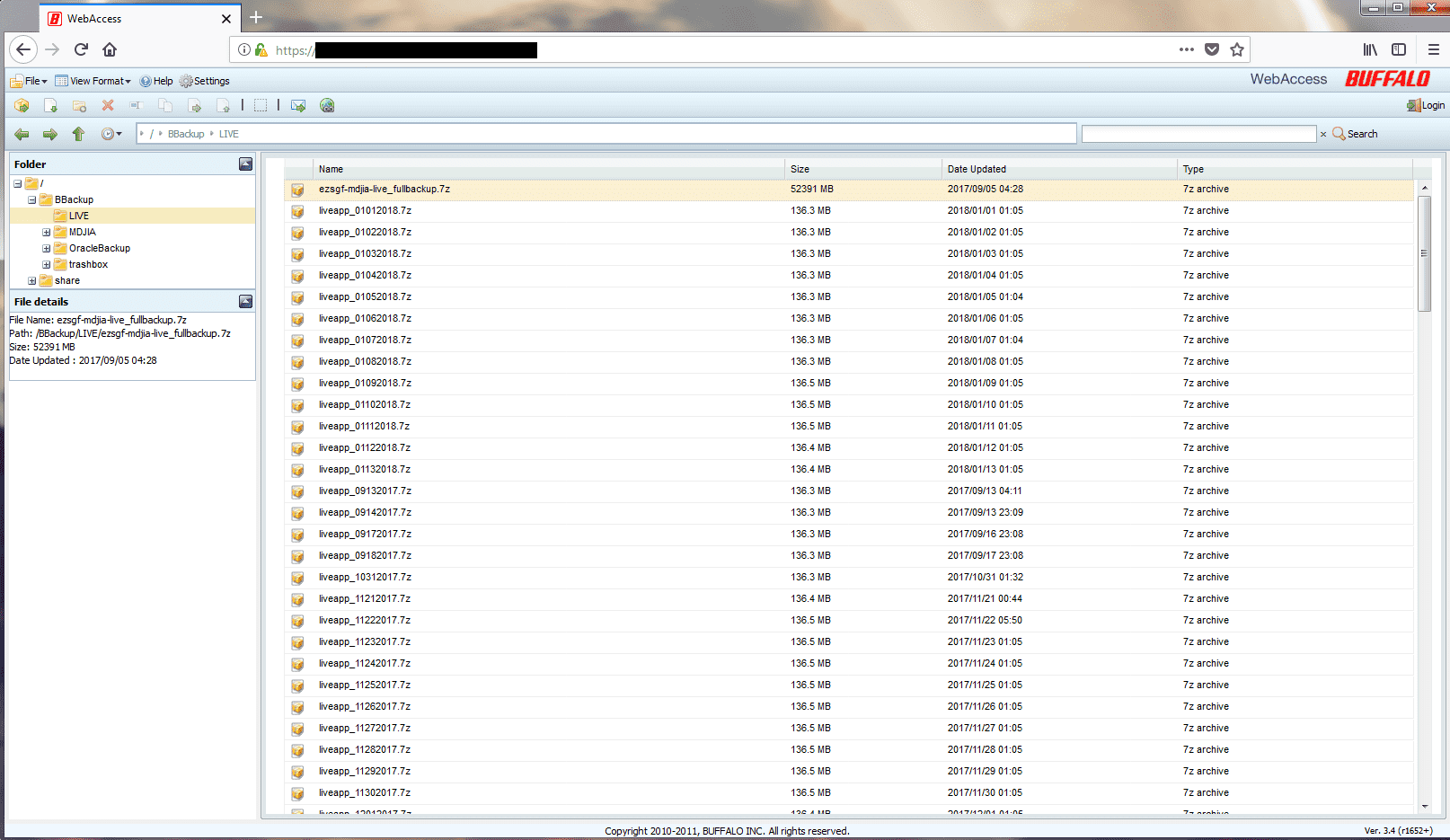
The interior of the “Live” subfolder.
BBackup contains a large number of files, all of which are customer-oriented JIA association IT operations documents, from the application for insurance to the claim for compensation. These data contain a large number of personal identification information. A 60GB folder called “appgen” contains a subfolder with more than 175,000 files saved from 2012 to the present. A similar sub-folder called “DU” contains 149,000 files, all of which are the applicant’s name, address, and phone number.
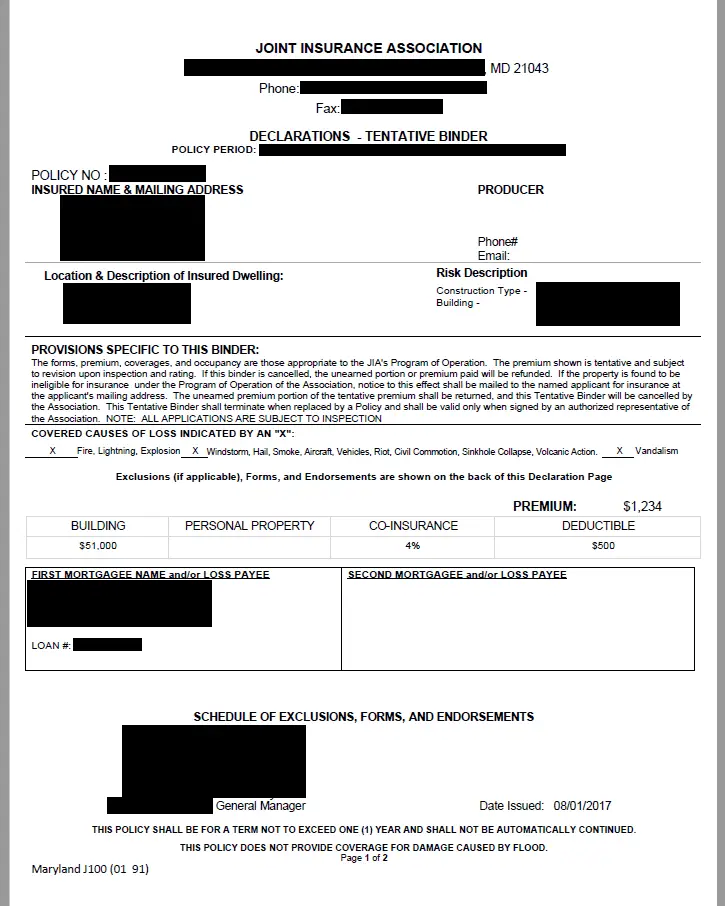
Property inspection reports and claims submissions, such as property damage reports, provide more customer details. However, the most troublesome is the social security number in the “appgen” folder, as well as the policy number information, as well as a check image showing the full bank card number.
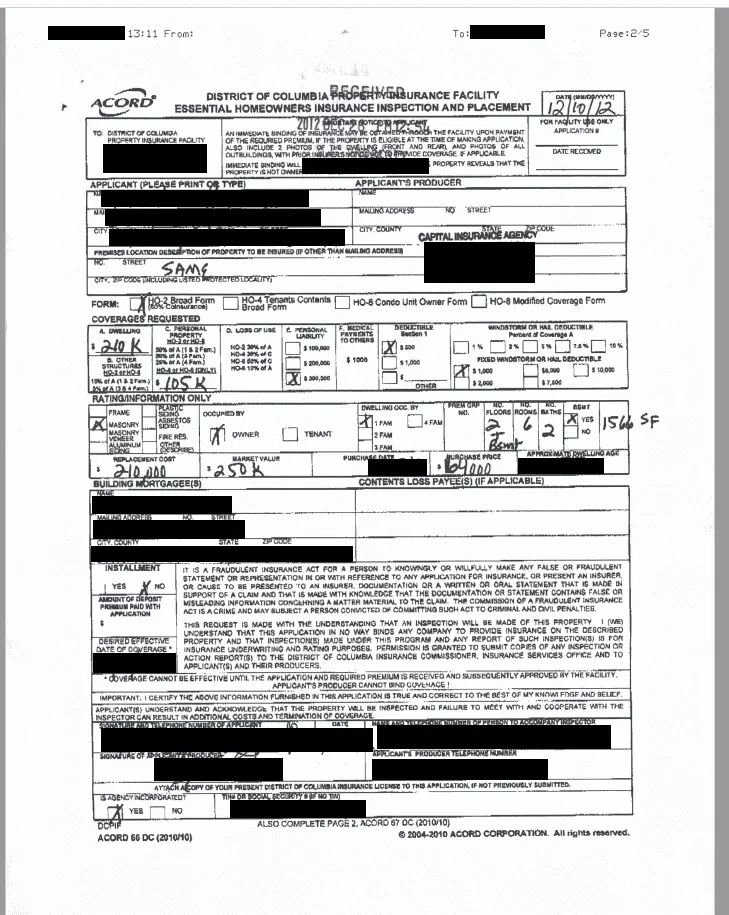
The “Share” folder contains sensitive information about MDJIA’s IT assets. Internal password list, including passwords for JIA email addresses saved as plain text, and screenshots of TeamViewer remote desktop access credentials.
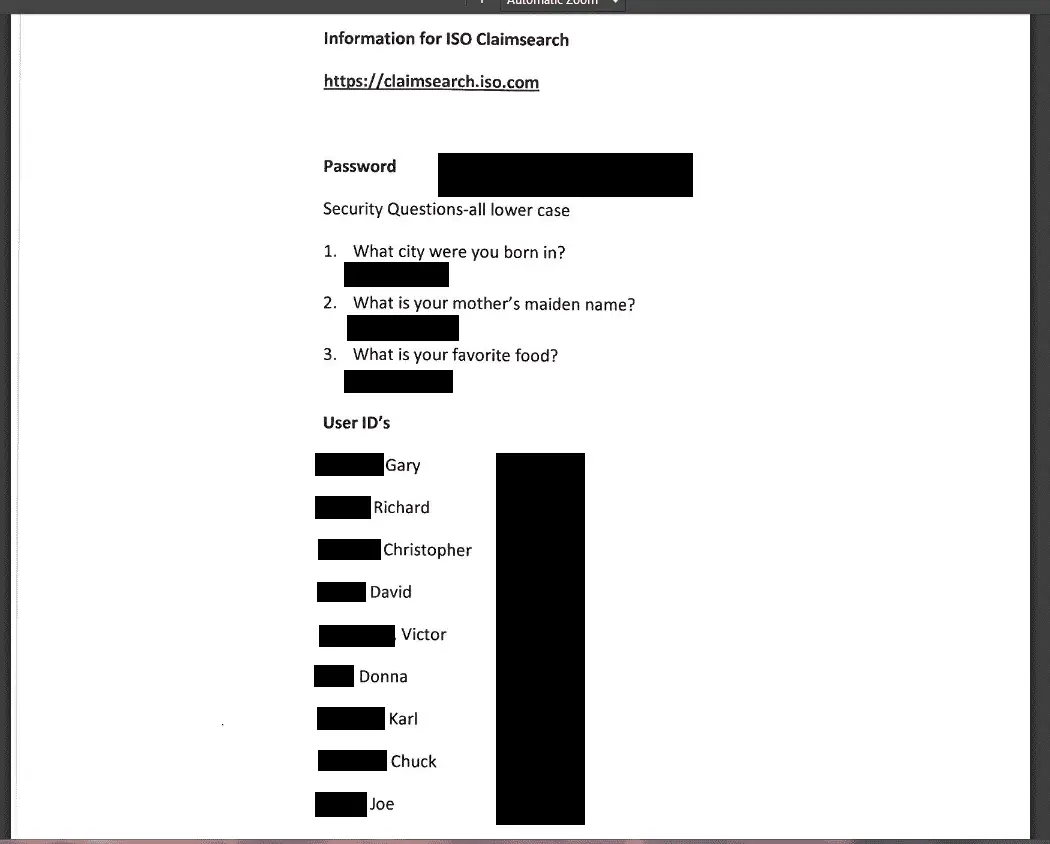
The exposure to MDJIA ISO ClaimSearch access credentials is even more devastating, a third-party insurance database provided by Verisk Analytics that contains millions of individual claims reports that industry experts refer to – in the unlikely event of a malicious visit, It is a tremendous treasure trove of identification information.
Source: upguard





