mobsfscan v0.3.4 releases: find insecure code patterns in your Android and iOS source code
mobsfscan
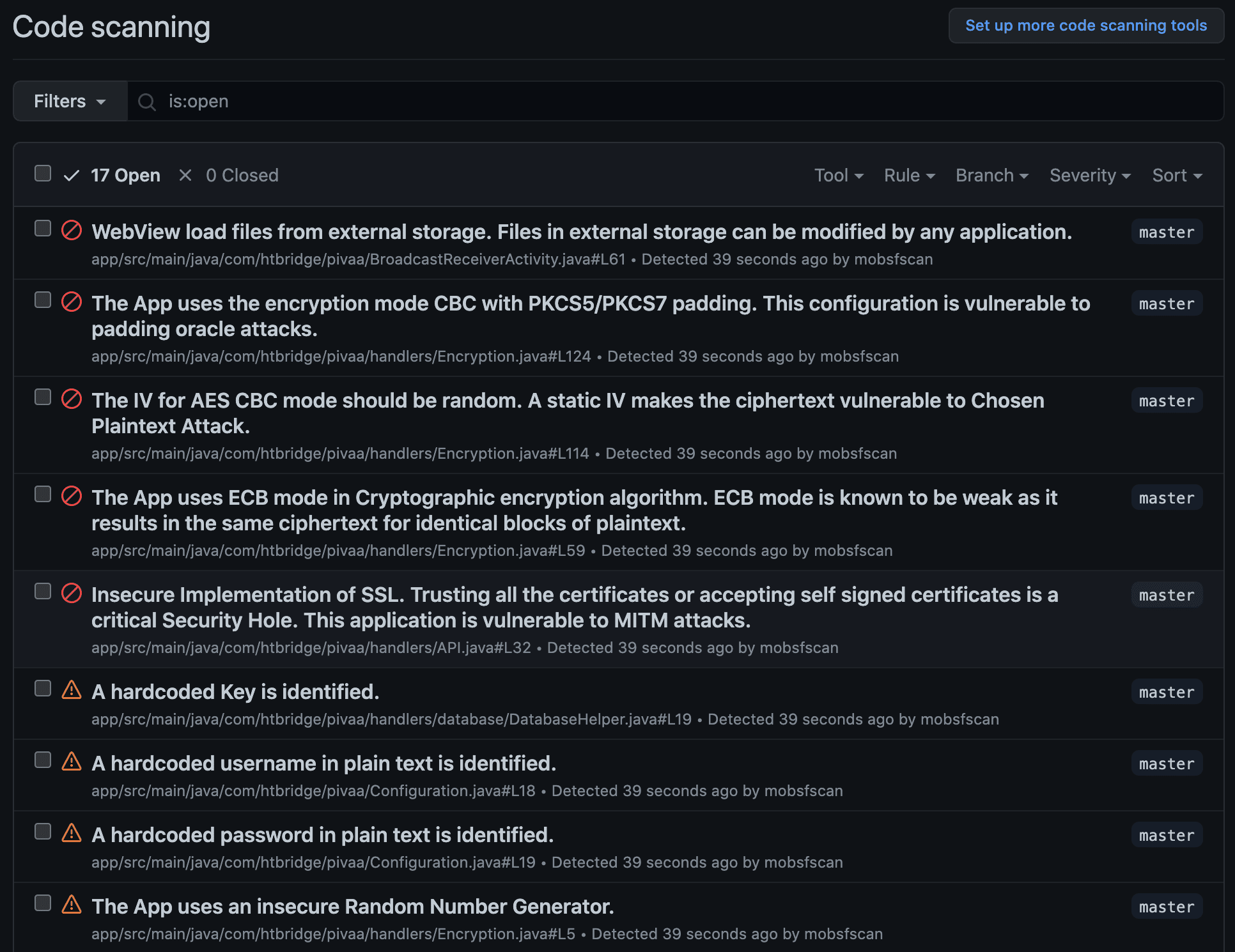
mobsfscan is a static analysis tool that can find insecure code patterns in your Android and iOS source code. Supports Java, Kotlin, Swift, and Objective C Code. mobsfscan uses MobSF static analysis rules and is powered by semgrep and libsast pattern matcher.
Changelog v0.3.4
- Huge Performance Improvement from libsast bump
Install
pip install mobsfscan
Use
Configure
A .mobsf file in the root of the source code directory allows you to configure mobsfscan. You can also use a custom .mobsf file using –config argument.
Command-line option
$ mobsfscan
usage: mobsfscan [-h] [–json] [–sarif] [–sonarqube] [–html] [-o OUTPUT] [-c CONFIG] [-w] [-v] [path [path …]]positional arguments:
path Path can be file(s) or directories with source codeoptional arguments:
-h, –help show this help message and exit
–json set output format as JSON
–sarif set output format as SARIF 2.1.0
–sonarqube set output format compatible with SonarQube
–html set output format as HTML
-o OUTPUT, –output OUTPUT
output filename to save the result
-c CONFIG, –config CONFIG
Location to .mobsf config file
-w, –exit-warning non zero exit code on warning
-v, –version show mobsfscan version





