NetKiller & Condi Botnets Exploit Uniview ISC Cameras CVE-2024-0778 Flaw
Security researchers have sounded the alarm on a critical vulnerability (CVE-2024-0778) affecting outdated Zhejiang Uniview ISC cameras. This flaw left unpatched in end-of-life devices, is a gateway for attackers to inject malicious code and potentially take control of vulnerable cameras.

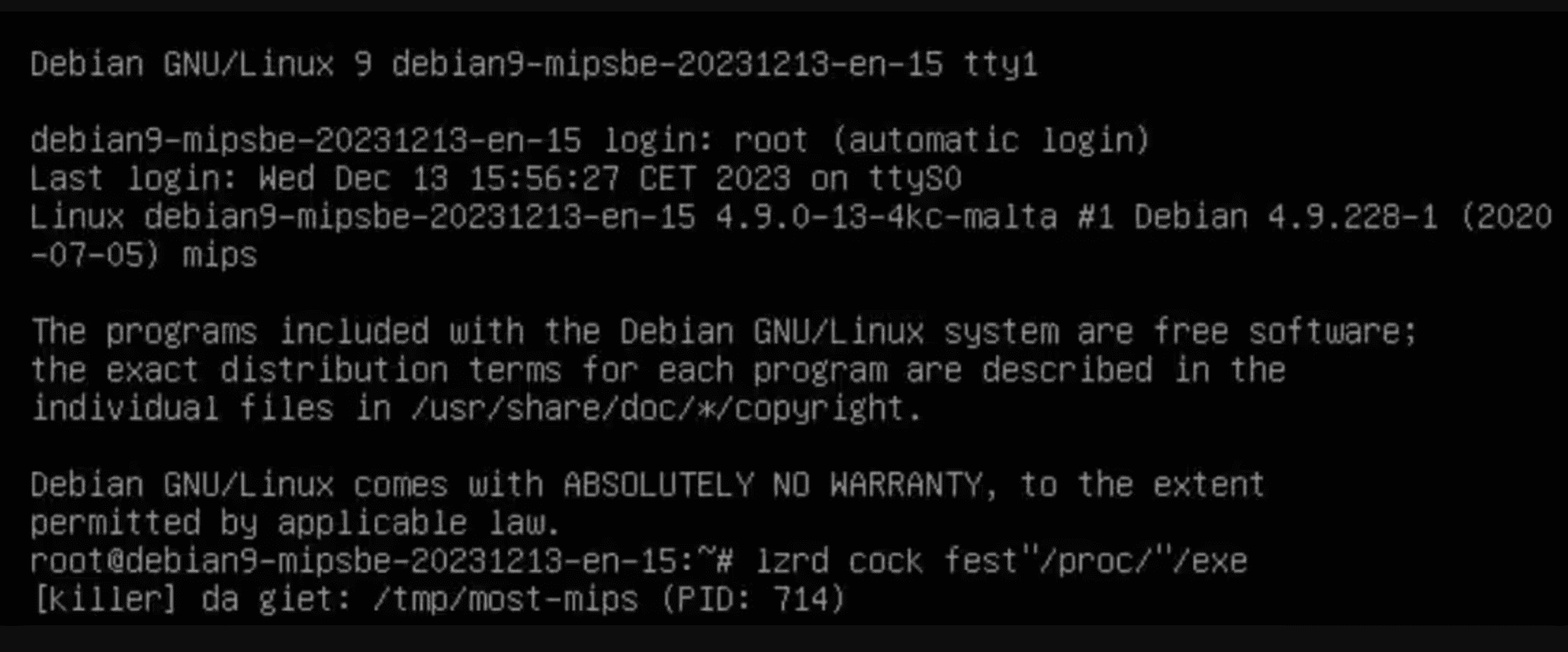
The console string is shown on the malware execution | Image: Akamai SIRT
At the heart of CVE-2024-0778 lies the exploitation of a function known as setNatConfig within the /Interface/DevManage/VM.php file. By manipulating request arguments such as natAddress, natPort, and natServerPort, attackers can inject and execute arbitrary OS commands with root privileges.
The Growing Threat
Akamai SIRT has documented active attempts to weaponize this vulnerability. Attackers are linking the exploit to the notorious Mirai botnet, notable for harnessing armies of compromised devices to launch devastating attacks.
-
Mirai & The Malware Variant: Execution of a downloaded malware sample reveals a unique identifier: “lzrd.” This places the exploit tool within the Lizard variant of the Mirai botnet family.
-
Connection to the ‘Condi’ Botnet: Further analysis links these attacks to a network of command and control servers associated with the Condi botnet. Since Condi’s source code went public in 2023, it’s likely multiple threat actors are now abusing this botnet framework.
The C2: Vietnam Connection
Akamai’s investigations reveal that the command and control (C2) infrastructure for this campaign is primarily based in Vietnam. The threat actors behind it appear to be actively reusing domain names and IP addresses.
Exploit Evolution & Tactics
The attackers aren’t just focusing on the Uniview camera vulnerability. Akamai honeypots have observed attempts to exploit other flaws (both older and more recent) to deploy Mirai malware variants. The attacker’s code shows a crude but effective attempt to download the malware, launch it, and then clean up traces of their activity.
The Bigger Picture – NetKiller
This campaign appears linked to a wider pattern of attacks dubbed “NetKiller.” Since mid-2023, this group has been primarily employing Mirai variants (SORA and LZRD). Their infrastructure frequently utilizes Vietnamese servers and a distinctive domain naming pattern.
What to Do
-
End-of-Life Devices Are a Liability: The crucial takeaway is that the targeted Uniview cameras are no longer supported by the manufacturer. If you use these cameras, the only true solution is replacement – patches won’t be coming.
-
Beyond Cameras: This incident spotlights the dangers of outdated, unpatched devices. Take inventory across your home or business network. If a device no longer receives vendor updates, it’s time to upgrade or isolate it from the internet.





