New Android Banker “SoumniBot” Employs Clever Tricks to Evade Detection

Researchers at Kaspersky Labs have detailed a sophisticated new Android banking trojan, dubbed “SoumniBot,” that targets Korean users. The malware is notable for its employment of unconventional obfuscation techniques centered on manipulating the Android manifest file, making detection and analysis more challenging.

The Android manifest file in any APK (Android Application Package) is crucial as it contains vital information about the app’s components and permissions. It is typically the starting point for any analysis by security software. However, SoumniBot’s creators have cleverly manipulated this entry point in several ways:
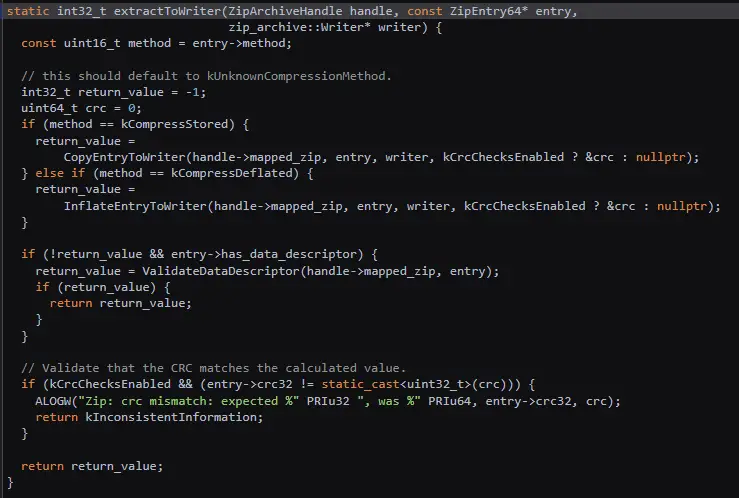
libziparchive unarchiving algorithm
- Invalid Compression Method Value
The first technique involves exploiting the libziparchive library’s compression method validation. By inserting a non-standard value in the Compression method field of the AndroidManifest.xml entry, SoumniBot tricks the Android APK parser into treating the manifest as uncompressed data. This discrepancy allows the malware to slip past initial checks during installation.
- Invalid Manifest Size
Another method employed by SoumniBot is declaring an incorrect size for the AndroidManifest.xml file. If the size declared is larger than the actual file, the parser ends up reading additional, irrelevant data appended to the manifest. This manipulation leads to an overlay of extra data, which most stringent parsers would reject, but the Android system erroneously accepts.
- Long Namespace Names
Furthermore, SoumniBot uses excessively long strings as XML namespace names within the manifest. This results in the file becoming cumbersome to read, potentially exceeding memory limits for some parsers, yet the Android system’s parser bypasses this without issue due to its design to ignore namespaces.
Beyond Obfuscation: SoumniBot’s Malicious Activities
Once installed, SoumniBot begins a series of covert operations. It first attempts to retrieve two critical server addresses from its command and control server: one for data collection and the other for receiving commands via MQTT messaging. In cases where it cannot reach its designated server, it defaults to pre-stored addresses embedded within its code.
The malware conceals its presence by hiding the app icon, complicating its removal. It then starts transmitting detailed personal data from the device to its server at frequent intervals. This includes the user’s IP address, contact lists, text messages, and a unique ID generated by the malware.
One of its more sinister functionalities involves scanning for and extracting digital certificates used by Korean banking apps, stored in files with .key and .der extensions. These certificates are critical for online banking and transaction verification, making their theft particularly damaging.
SoumniBot represents a significant advancement in Android malware, demonstrating that malicious actors are continually refining their methods to outsmart current security technologies. Its ability to steal banking credentials and evade detection through innovative manipulation of Android’s manifest parsing highlights the need for continuous updates to security protocols and software.





