New Cuttlefish Malware Evades Detection, Targets SOHO Routers

Security researchers at Lumen Technologies’ Black Lotus Labs have uncovered a sophisticated new malware campaign targeting enterprise-grade small office/home office (SOHO) routers. Dubbed “Cuttlefish,” the malware is designed to remain undetected while stealing sensitive data and hijacking network traffic.

Flow diagram for packet filter and hijacking parameters
Cuttlefish is designed as a modular malware, primarily focusing on intercepting authentication data from web requests transiting through the infected routers. However, its functionality does not stop there; it also has capabilities for DNS and HTTP hijacking, particularly targeting connections to private IP addresses within an internal network. This allows the malware not only to steal data but also to reroute traffic to malicious servers, potentially leading to further exploitation.
One of the more insidious features of Cuttlefish is its ability to operate under the radar. The malware passively sniffs packets, activating only when specific conditions are met, based on a predefined set of rules. This behavior minimizes its detectability while maximizing the potential for data interception. The packet sniffer component is finely tuned to capture authentication materials, with a heavy emphasis on public cloud-based services, which are increasingly used by enterprises for critical operations.
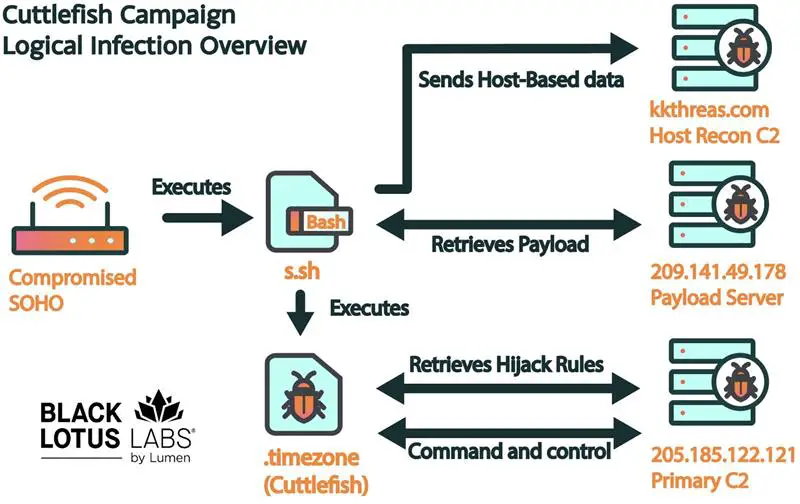
Depicting the network connections associated with Cuttlefish activity
The initial infection vector of Cuttlefish remains unclear, highlighting the stealth and careful planning of its operators. Upon successful exploitation, the malware deploys a bash script that gathers critical data from the host device, setting the stage for further malicious activities. The impact of this malware is significant, with the majority of detected infections traced back to Turkey, implicating local telecommunications providers as the primary channels of distribution.
Interestingly, there is a noted overlap between Cuttlefish and a previously identified malware cluster known as HiatusRat. Both malware families share similar code elements and operational tactics, suggesting a possible link between the groups behind them. HiatusRat malware has been associated with interests aligning with the People’s Republic of China.
In response to the threats posed by Cuttlefish, cybersecurity teams are urged to enhance their defensive strategies, particularly around network equipment that might traditionally be less monitored. Regular updates, stringent monitoring of network traffic, and advanced intrusion detection systems are recommended to identify and mitigate threats posed by such sophisticated malware.
The emergence of Cuttlefish underscores the evolving and increasingly sophisticated nature of cyber threats targeting critical network infrastructure. As attackers pivot to exploiting foundational network equipment, the need for comprehensive security measures and proactive threat detection has never been more critical. For organizations across the globe, particularly those utilizing SOHO environments, the discovery of Cuttlefish serves as a stark reminder of the importance of robust cybersecurity practices and collaborative efforts to safeguard digital assets and network integrity.





