New Cybercrime Wave: UNC3944 Exploits SaaS Vulnerabilities
Mandiant, a renowned cybersecurity firm, has issued a warning about the evolving tactics of the financially motivated threat group UNC3944. This group, previously associated with ransomware attacks, has shifted its focus to data theft and extortion from Software-as-a-Service (SaaS) applications.
UNC3944, also identified in public reports as “0ktapus,” “Octo Tempest,” “Scatter Swine,” and “Scattered Spider,” has been active since at least May 2022. Initially focusing on credential harvesting and SIM swapping attacks, the group has evolved its tactics to include data theft extortion. This shift has seen a broader range of targeted industries and organizations.
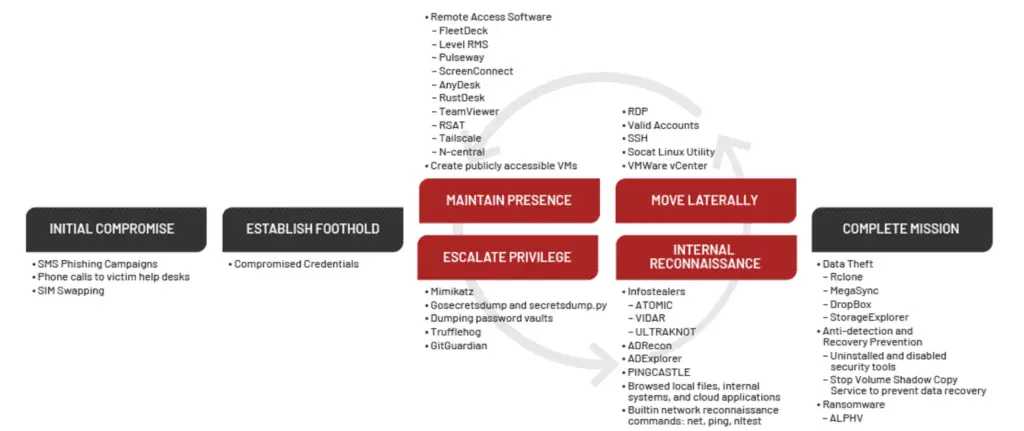
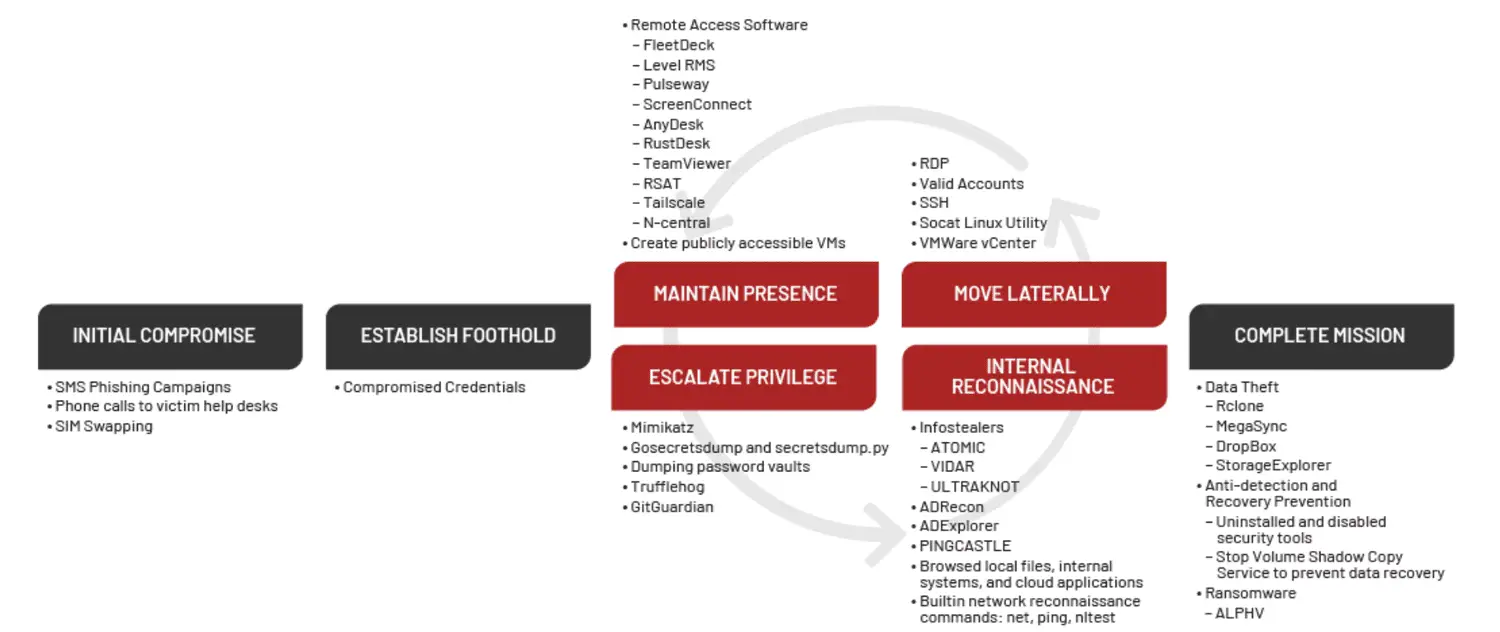
UNC3944 attack lifecycle | Image: Mandiant
Mandiant’s analysis reveals that UNC3944 employs a range of sophisticated TTPs:
- Social Engineering Attacks: UNC3944 uses social engineering techniques to gain initial access to privileged accounts. They target corporate help desks, posing as employees needing multi-factor authentication (MFA) resets. By exploiting personally identifiable information (PII) such as Social Security numbers and job titles, they bypass user identity verification and reset passwords for high-privilege accounts.
- Lateral Movement via SaaS Permissions Abuse: Once inside, UNC3944 abuses Okta permissions, assigning compromised accounts to every application within an Okta instance. This allows them to conduct internal reconnaissance and escalate privileges across multiple SaaS applications.
- Virtual Machine Compromise: The group creates new virtual machines using administrative permissions tied to single sign-on (SSO) applications. They employ tools like MAS_AIO and privacy-script.bat to deactivate security policies and download additional tools such as Mimikatz and NGROK. This method enables persistent access and evasion of traditional detection mechanisms.
- Data Exfiltration: UNC3944 uses cloud synchronization utilities like Airbyte and Fivetran to move data from cloud-hosted sources to attacker-owned storage. This allows for seamless exfiltration of sensitive data with minimal detection risk.
Specific Techniques and Tools
- PCUnlocker: Used to bypass authentication controls by resetting local administrator passwords on virtual machines.
- MAS_AIO and privacy-script.bat: Utilities to reconfigure virtual machines and disable security policies.
- Cloud Synchronization Tools: Airbyte and Fivetran enable data synchronization from SaaS applications to external storage.
Mandiant’s recent investigations highlight several key activities by UNC3944:
- Reconnaissance of Microsoft Applications: The group targets internal documentation on SharePoint to identify remote connection requirements for VPNs and other telework utilities.
- Okta Web Portal Exploitation: By assigning compromised accounts to various applications, they conduct extensive internal reconnaissance.
- Persistent and Sophisticated Access: Utilizing tools like PCUnlocker and virtual machine creation, UNC3944 maintains persistent access to compromised environments.
Mandiant recommends a multi-pronged approach to mitigate the risks posed by UNC3944 and similar threats. This includes:
- Heightened monitoring of SaaS applications: Centralize logs, monitor MFA re-registrations, and track virtual machine activity for anomalies.
- Robust logging capabilities: Ensure sufficient logging granularity in SaaS applications for effective security analysis.
- Stricter conditional access policies: Limit the visibility and access within cloud tenants to minimize the potential impact of a breach.





