New DarkGate Malware Campaign Exploits 0-day CVE-2024-21412 Flaw

Recently, researchers at the Zero Day Initiative (ZDI) have dissected a complex DarkGate malware campaign targeting users through a zero-day flaw in Microsoft Windows SmartScreen (CVE-2024-21412). The attackers, associated with the notorious DarkGate group, are meticulously weaponizing trusted technologies and exploiting human vulnerabilities to spread their malicious payload.
The Attack Unfolds

The infection chain | Image: ZDI
-
Social Engineering Lure: The initial infection vector isn’t a run-of-the-mill phishing email. Instead, attackers are misusing Google’s DoubleClick Digital Marketing (DDM) platform. Victims receive malicious PDFs containing open redirects – seemingly innocuous links that exploit hidden flaws in how web traffic is routed. These redirects lead users to compromised websites ready to exploit the SmartScreen vulnerability.
-
SmartScreen Deception: CVE-2024-21412 allows attackers to bypass a critical security function. Microsoft SmartScreen is designed to warn users when downloading potentially dangerous files from the internet. By exploiting this flaw, attackers can deliver malware without triggering these familiar warning prompts, greatly increasing the chances of a successful infection.
-
The Wolf in Sheep’s Clothing: The compromised websites deliver seemingly legitimate software installers (disguised as Apple iTunes, NVIDIA software, etc.). However, these installers contain a cleverly hidden malicious sideloaded DLL file. This DLL acts as a trojan horse, initiating a multi-stage process that ultimately deploys the DarkGate malware.
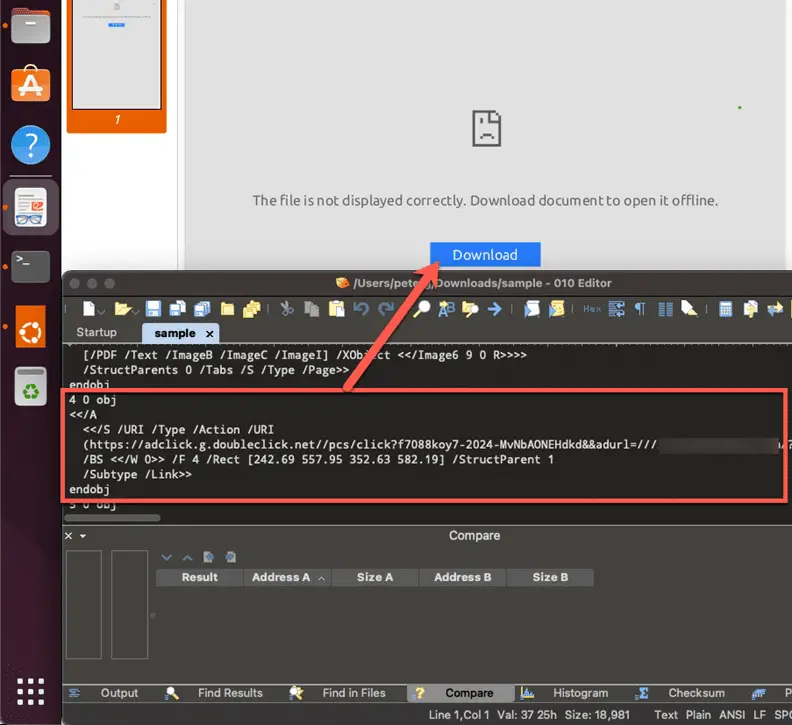
Open redirect inside phishing PDF | Image: ZDI
In mid-January 2024, ZDI uncovered the DarkGate campaign, a nefarious operation that leveraged fake software installers to deploy malware on unsuspecting victims’ machines. The campaign ingeniously utilized PDF documents containing Google DoubleClick Digital Marketing (DDM) open redirects, guiding victims to compromised sites. These sites hosted malicious Microsoft (.MSI) installers, cleverly designed to masquerade as legitimate software from reputable companies like Apple iTunes, Notion, and NVIDIA, among others.
A cornerstone of this campaign’s strategy involved the abuse of open redirects within the Google Ads ecosystem. By embedding an open redirect from the doubleclick[.]net domain inside a phishing PDF, the attackers orchestrated a seamless transition for the victim from a seemingly benign advertisement to a compromised web server. This transition was critical for the exploitation of CVE-2024-21412 and the subsequent infection with DarkGate malware.
Open redirects exploit the inherent trust users place in major web services, turning this trust against them to facilitate malware delivery. The Google Ads platform, designed to show relevant ads based on user queries, became an unwitting accomplice in the campaign, highlighting the sophisticated manipulation of advertising technologies by cybercriminals.
DarkGate: A Formidable Threat
The DarkGate campaign’s infection chain is complex and stealthy. Beginning with the exploitation of CVE-2024-21412 to bypass Windows Defender SmartScreen, the attackers laid a breadcrumb trail of internet shortcut files leading to the ultimate payload delivery. The stages involved sideloading a malicious DLL, decrypting an AutoIt script to deploy the DarkGate payload, and finally, executing the malware to seize control of the victim’s machine.
This meticulously crafted attack chain underscores the lengths to which threat actors will go to ensure the success of their malicious endeavors. The use of legitimate-looking installers and the abuse of trusted domains like Google’s ad services exemplify the evolving threat landscape and the sophistication of modern cyber-attacks.
DarkGate is a sophisticated malware-as-a-service (MaaS) platform notorious for its use by financially motivated cybercriminals. Organizations across the globe are common targets, and typical repercussions of a DarkGate attack include:
- Extensive Data Theft: Stealing sensitive information, intellectual property, and credentials.
- System Takeover: Compromising systems for further attacks or as part of botnets.
- Ransomware and Extortion: Encrypting files and demanding payment for their release.
Protect Yourself – Critical Actions
This attack proves how dangerous zero-day vulnerabilities can be, especially when paired with deceptive techniques like open redirect abuse. Microsoft addressed CVE-2024-21412 in their February 2024 security patch, but the campaign highlights the speed with which threat actors capitalize on unpatched systems.
-
Patching is Paramount: Immediately apply all available software updates, especially security patches.
-
Stay Vigilant: Open redirects can be subtle. Educate users to avoid clicking links in unfamiliar emails, verify downloads from official sources, and always treat unsolicited software with suspicion.
-
Defense in Depth: Don’t rely on a single security layer. Implement firewalls, intrusion detection and prevention systems, endpoint protection software, and regular system backups to create a robust defense.




