New Infostealer “Ailurophile” Discovered, Poses Significant Risk to User Privacy
A new information-stealing malware dubbed “Ailurophile” has been discovered by cybersecurity researchers at G DATA. This PHP-based stealer, suspected to have Vietnamese origins, is being sold on a subscription basis with a web panel that enables buyers to customize and generate malware stubs.
The Ailurophile web panel offers a wide array of options for malware customization, including the ability to name the malware, select an icon, and configure Telegram notifications upon successful data exfiltration. Additionally, subscribers can opt to make the malware stub more difficult to detect, disable Windows Defender, and even deploy additional malicious payloads from a specified URL. The web panel also provides a summary of infected hosts and the extent of data stolen.

The Web Panel | Image: G DATA
The malware’s data theft capabilities are extensive, targeting popular browsers like Chrome, Edge, Brave, and others. Ailurophile can exfiltrate sensitive information, including autofill data, cookies, stored passwords, browsing history, credit card details, and even wallet data from browser extensions. Furthermore, the malware is designed to search for and steal specific files based on keywords and extensions within designated directories, broadening its information-gathering scope.
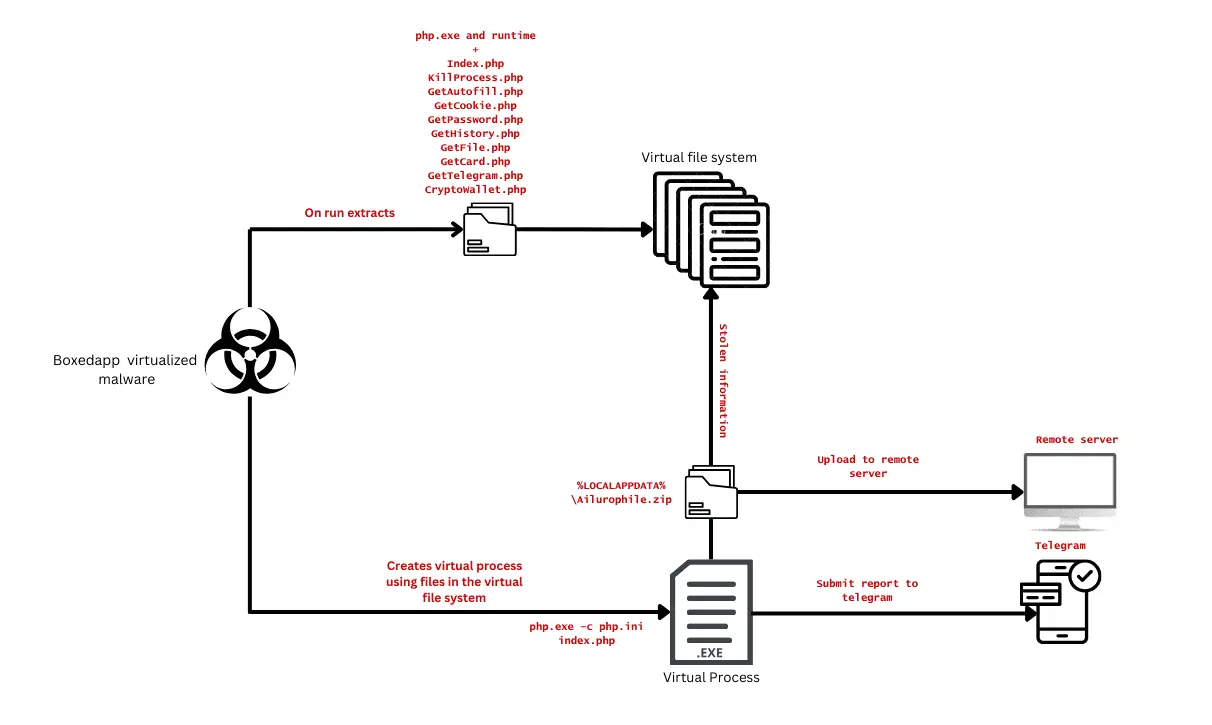
Ailurophile utilizes “ExeOutput” and “BoxedApp” for packaging and virtualization, respectively, to enhance its stealth and evasion capabilities.
When executed, the malware uses the BoxedApp environment to extract and run its PHP interpreter and components from a virtual file system, remaining memory-resident and difficult to detect. The stealer’s configuration is managed via a JSON file, which houses settings defined through the web panel. This file is read at runtime, enabling the malware to initiate its data theft operations.
Ailurophile’s functionality is divided across multiple PHP scripts, each tasked with a specific role:
- index.php: The core module that gathers system information, defines target directories, and initiates data theft.
- KillProcess.php: Terminates processes like Chrome, Edge, Discord, and Telegram to ensure unimpeded operation.
- GetAutoFill.php, GetCookie.php, GetPassword.php, GetHistory.php: These modules harvest auto-fill data, cookies, passwords, and browsing history, respectively.
- GetFile.php: Targets files with specific extensions and keywords, archiving and uploading them for exfiltration.
- GetCard.php: Focuses on extracting stored credit card details from browser databases.
- GetTelegram.php: Pilfers Telegram data, particularly session files, for potential account takeover.
- CryptoWallet.php: Steals cryptocurrency wallet data from browser extensions, jeopardizing users’ digital assets.
- Delivery.php: Handles the disabling of Windows Defender and the execution of additional payloads, further complicating detection and removal.
G DATA’s analysis revealed that Ailurophile is still under active development. Variations in the malware’s components and configuration files suggest that it is being refined, with new features and improvements being introduced regularly. The malware is primarily distributed through malicious software cracks, a common strategy to lure victims.





