New Necro Trojan Targets Over 11 Million Android Devices Through Google Play and Unofficial Apps
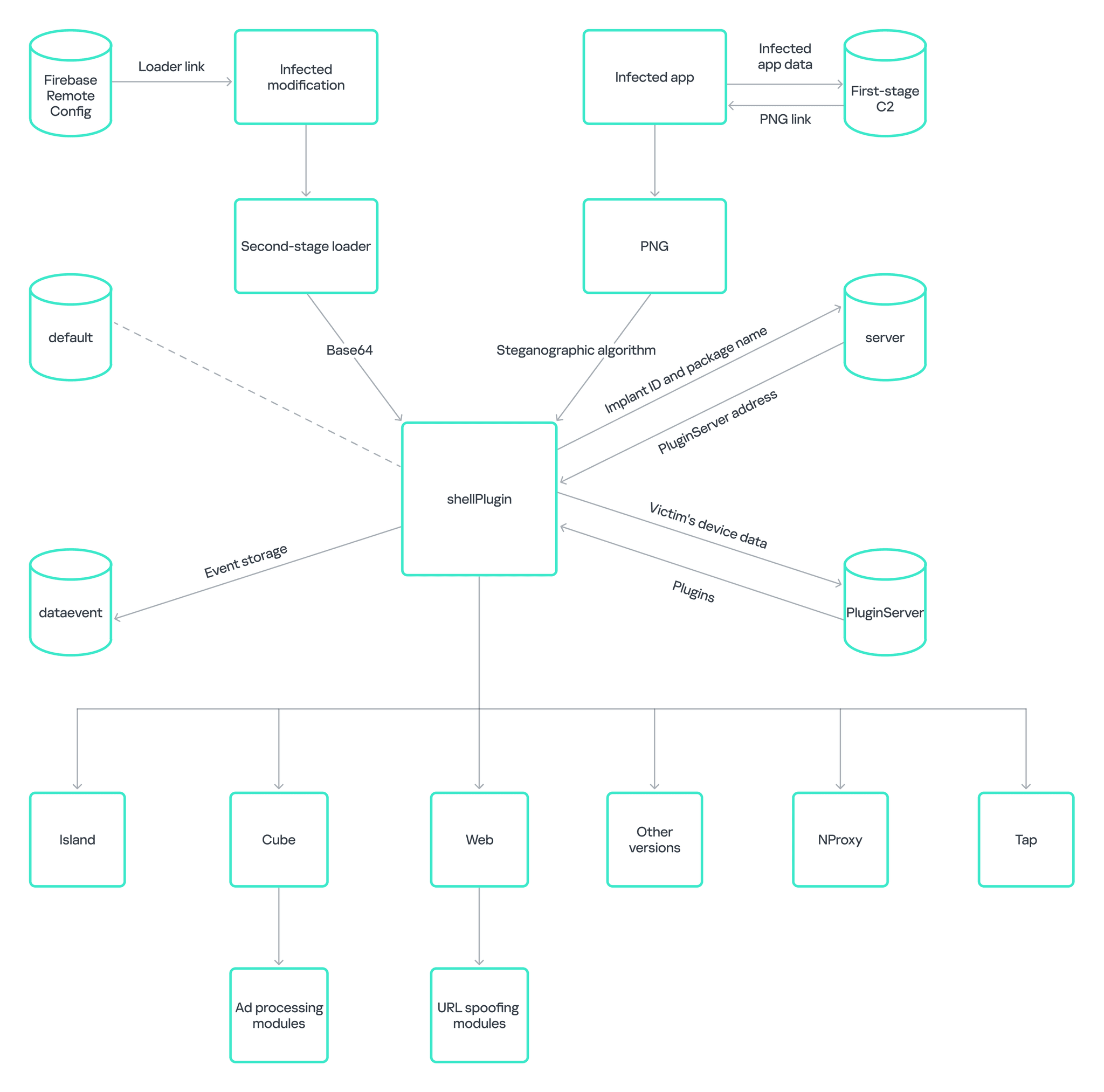
In a concerning development for Android users, Kaspersky Labs has uncovered a new version of the Necro Trojan, a multi-stage malware loader capable of infecting millions of devices. This latest variant has been found lurking within both modified versions of popular apps and official applications available on Google Play, including widely used apps such as Wuta Camera and Max Browser. The total number of infected Android devices is estimated to exceed 11 million.
Originally discovered in the CamScanner app in 2019, the Necro Trojan has resurfaced, exploiting both legitimate platforms like Google Play and unofficial sources. This time, it has compromised not only niche modifications but also well-known apps such as Spotify, WhatsApp mods, Minecraft, and others. Disturbingly, these infected versions have found their way onto user devices through unofficial websites and even the official app store, intensifying the risk.
Site containing the Spotify mod | Image: Kaspersky Labs
Kaspersky’s report indicates that the Trojan’s creators used a mix of obfuscation and steganography techniques to evade detection. Steganography, a rare method in mobile malware, was used to hide payloads inside image files, making it difficult for standard security systems to detect and block.
Wuta Camera app in Google Play | Image: Kaspersky Labs
The infection begins with the installation of a malicious loader, often embedded within a modified app like Spotify Plus, which falsely claims to provide additional features. Once installed, the loader establishes communication with a remote command-and-control (C2) server. This server delivers an encrypted response, which includes a hidden payload disguised in the ARGB channels of a PNG image file. The loader then extracts the payload and executes it, giving the attackers control over the infected device.
Necro’s capabilities extend beyond merely displaying ads. It can also:
- Download and execute arbitrary code (DEX files).
- Install additional malicious applications.
- Open hidden web windows to run JavaScript, potentially subscribing users to paid services without their knowledge.
- Create a tunnel through the victim’s device, granting attackers further access to sensitive data.
According to Kaspersky’s telemetry, Necro has been particularly active in Russia, Brazil, and Vietnam, but its global reach is expanding. Between late August and mid-September 2024, the security firm blocked over 10,000 Necro attacks worldwide. However, this number likely represents only a fraction of the total infections, given the Trojan’s ability to infiltrate both official and unofficial app distribution channels.
If you have downloaded any of the infected applications, it is vital to take immediate action. Kaspersky recommends the following steps to protect your device:
- Update or Delete Infected Apps: Ensure that your apps, particularly those from Google Play, are up to date. Infected versions of Wuta Camera and Max Browser have been removed from the store, and updated versions without malicious code are available.
- Stick to Official Sources: Avoid downloading apps from unofficial websites, as these often harbor malware.
- Use a Reliable Security Solution: Install a trusted mobile security solution that can detect and block threats like Necro before they infect your device.




