New Phishing Campaign Targets US Government Organizations
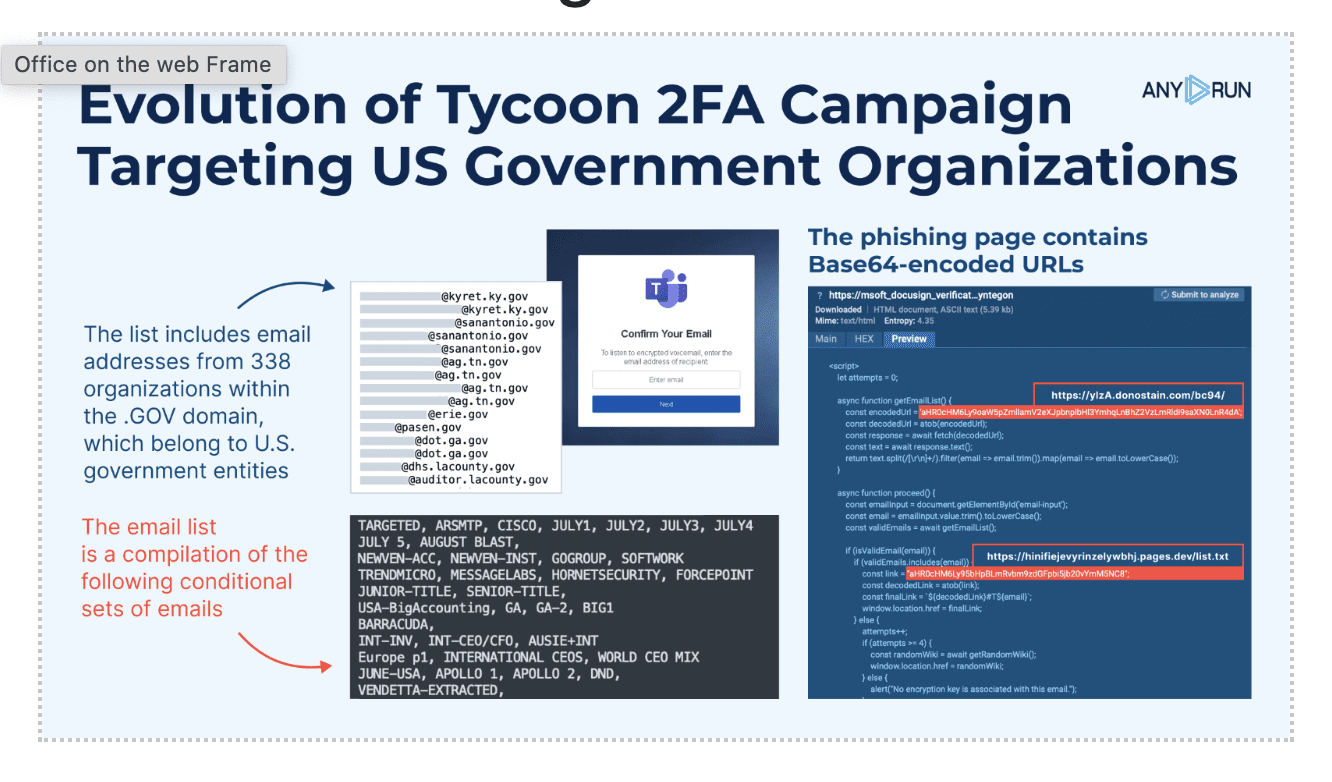
Researchers at ANY.RUN have identified a new campaign using Tycoon 2FA phish-kit. This time, attackers are targeting US government organizations with fake Microsoft pages.
Tycoon 2FA and Its Latest Activity
Tycoon 2FA is a malicious toolkit that has been employed by cybercriminals since 2023 to carry out phishing campaigns targeting victims’ credentials. Known for its versatility, Tycoon 2FA has been observed using tactics such as QR codes embedded in fraudulent emails and complex redirect chains to mislead victims.
In late July 2024, the threat was used in a campaign leveraging compromised Amazon Simple Email Service (SES) accounts.
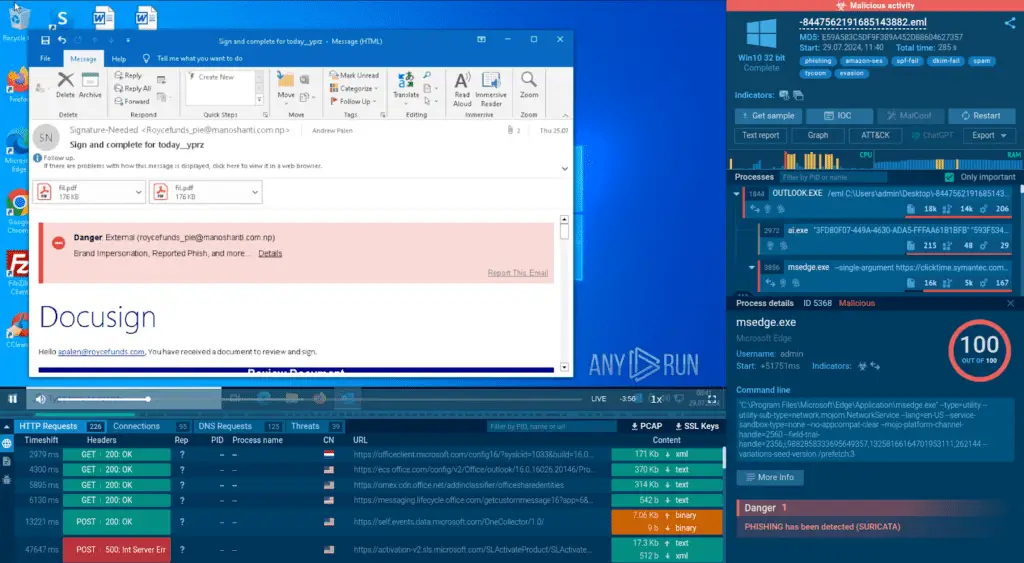
The entire attack chain, starting from the email, can be analyzed in ANY.RUN sandbox
See analysis in the ANY.RUN sandbox to safely follow the entire chain of the attack.
The initial email, pretending to be from Docusign, prompted the recipient to review and sign a document. Clicking the “Review Document” link initiated a series of redirects designed to conceal the final phishing domain, requesting victims to enter their credentials.
| Create a free ANY.RUN sandbox account to analyze phishing and malware threats |
New Campaign Targeting US Government Email Addresses
Now, the phishing campaign has become more selective in its approach, targeting a list of email addresses from 338 organizations within the .gov domain, which indicates that the attackers are specifically focusing on US government entities.
The list of targeted email addresses is stored on Cloudflare Pages at the following URL: hinifiejevyrinzelywbhj[.]pages[.]dev/list.txt.
When a potential victim clicks on a phishing link, they are redirected to a fake Microsoft Teams login page.
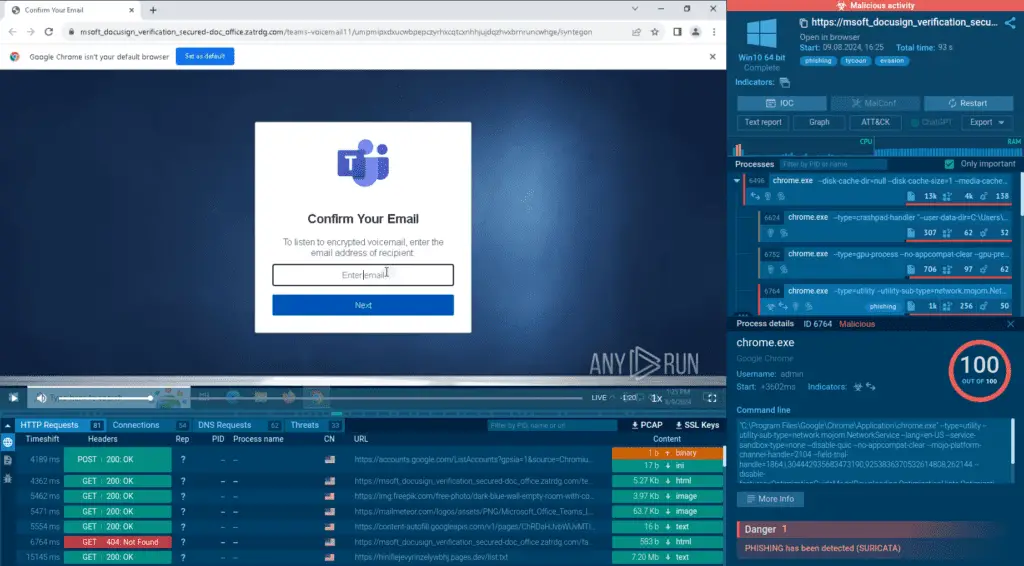
We can enter fake credentials to see how the attack unfolds further in ANY.RUN sandbox
ANY.RUN sandbox lets us see that the primary phishing domain used in this campaign is: MSOFT_DOCUSIGN_VERIFICATION_SECURED-DOC_OFFICE[.]zatrdg[.]com
Here, victims are prompted to enter their email address. If the email address entered is on the attacker’s list, the victim is then redirected to an obfuscated phishing domain donostain[.]com.
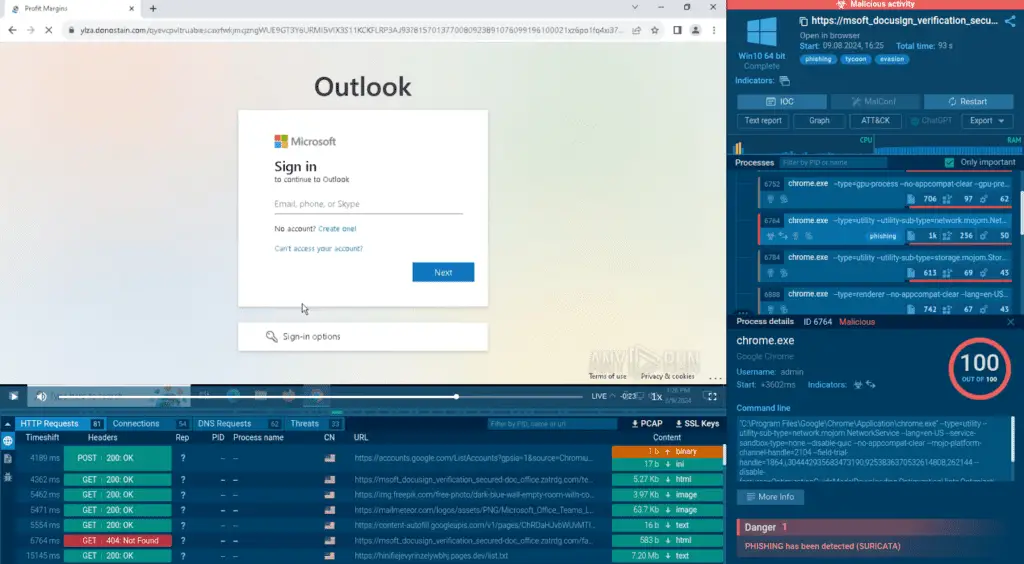
Fake Microsoft page hosted on donostain[.]com displayed in ANY.RUN
The communication with donostain[.]com is conducted via a multipart POST request and encrypted using AES in CBC mode.
Another domain, vereares[.]ru, is consistently used by the attacker across multiple campaigns. This domain helps the attacker decide where to redirect the victim, showing the adaptability of the phishing scheme.
Legitimate Services Used
Interestingly, the attackers leverage legitimate services to enhance the credibility of their phishing attempts. Logos and backgrounds for the fake Microsoft Teams pages are stored on mailmeteor[.]com, while external IP checks and IP information are retrieved via jsonip[.]com.
Conclusion
Given the evolving nature of Tycoon 2FA phishing campaigns, we can expect a new iteration of the attack soon. To expose phishing attempts and malware, use ANY.RUN sandbox.
The service lets you safely and quickly study suspicious links and files right in your browser. You can use private mode and work with your entire team in a shared space.
Get a 14-day free trial of ANY.RUN to try all features of the sandbox.





