New PyRoMine malware exploits NSA vulnerabilities to mine Monero
The security company Fortinet posted in its blog post on Tuesday that their FortiGuard laboratory research team recently discovered a very destructive new type of malware. It will not only deploy the Monero Miner (XMRig) on infected Windows devices, but it will also disable the security features on Windows systems, which will undoubtedly cause infected devices to be exposed to other network threats. The reason why these malicious functions can be realized comes from the fact that it uses a security hole leaked by the National Security Agency (NSA)—Eternal Romance.
In 2016, a Shadow Brokers hacking group claimed to have succeeded in hacking another hacking organization associated with the US National Security Agency, the Equation Group, and leaking it from the organization. Some hacking tools and zero-day exploits.
On April 14, 2017, Shadow Brokers again released a series of “attack weapons” that included the EternalRomance vulnerability. Essentially, this is a Remote Code Execution (RCE) vulnerability that abuses the legacy SMBv1 file-sharing protocol and affects almost all versions of Windows systems, including Windows XP/Vista/8.1/7/10 and Windows Server 2003. /2008/2012/2016.
Having said this, we have to mention another NSA vulnerability, Eternal Blue, which is similar to EternalRomance and is also based on the Windows Network Sharing Protocol SMB. In general, file sharing on SMB is only used on the local network. Unfortunately, many organizations have exposed SMBv1 to the Internet, which is why WannaCry and NotPetya ransomware attacks based on these two loopholes can cause major economic losses to global companies.
We want to emphasize that whether it is EternalBlue or EternalRomance, Microsoft has released a fix for such vulnerabilities on March 14, 2017, through Security Bulletin MS17-010. In order to avoid becoming a victim of our own, it seems that we need to maintain timely security updates.
The malware discovered by FortiGuard Labs research team was named “PyRoMine”, a cryptocurrency mining malware developed based on the Python language.
This malware is considered extremely destructive because it has the ability to disable the system’s security features to bypass security detection and spread itself without the victim’s knowledge. Worse, it can also use Remote Desktop Protocol (RDP) on infected systems to open the door for further attacks.
Researchers said that they discovered PyRoMine through a malicious URL that can be downloaded as a zip file. This file contains an executable file compiled with PyInstaller. PyInstaller is a program that packages programs written in Python as separate executables, which means that you can execute Python programs without installing a Python environment on the affected device.
The EternalRomance exploit code used by the attacker came from the Exploit database site and they only partially modified it. But this is enough to enable them to complete PyRoMine’s self-propagation and gain SYSTEM authority.
The payload of the attack is downloaded from another malicious URL. This is a malicious VBScript script file named “agent.vbs” which downloads and starts the mining program (xmrigMiner32.zip or xmrigMiner64.zip) and the infected system. Make some settings.

Fortinet wrote in the blog post: “The malicious VBS file sets a default account with a password of ‘P@ssw0rdf0rme’ and adds this account to local groups ‘Administrators’, ‘Remote Desktop Users’ ‘and ‘Users’, then enable RDP and add firewall rules to allow traffic on RDP port 3389. In addition, it also disables the Windows Update service and starts the Remote Access Connection Manager service. Finally, it configures Windows Remote Manage services to enable basic authentication and allow the transmission of unencrypted data, which will undoubtedly cause infected devices to be exposed to other network threats.”
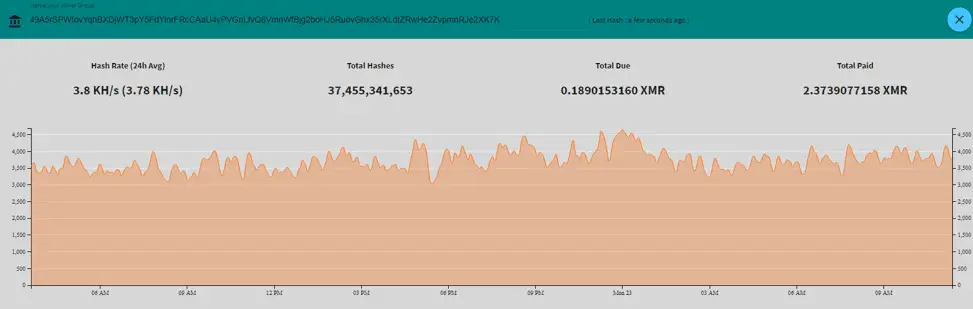
Researchers said they tracked the Monero coin wallet address used by the attacker. The attacker has collected about 2.4 Monero coins, worth about $650.
However, the researchers believe that this is only one of the addresses and there may be many other addresses. Therefore, at present, we cannot know how much profit the attacker has made so far.
In addition, the attacker is still improving PyRoMine, which may be to make more profits.





