New RomCom Variant “SnipBot” Unveiled: A Sophisticated Malware Targeting Enterprise Networks
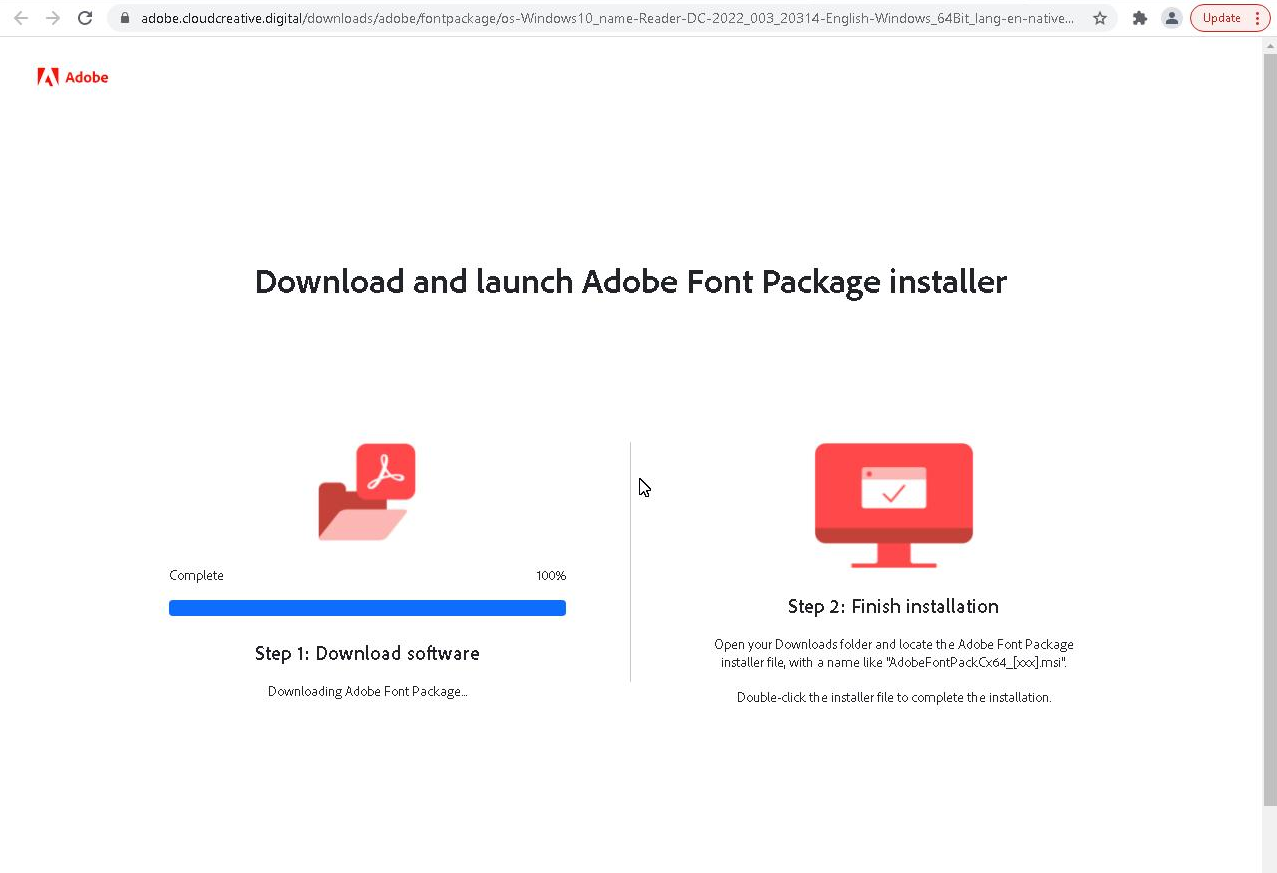
Unit 42 has revealed a new variant of the notorious RomCom malware family, known as “SnipBot.” This sophisticated malware, first discovered in early 2024, is designed to infiltrate enterprise networks, execute remote commands, and download additional malicious payloads. SnipBot represents the latest iteration of RomCom, incorporating novel code obfuscation techniques and advanced anti-detection strategies. It is believed to be part of a broader campaign targeting sectors such as IT services, legal entities, and agriculture.
In April 2024, Unit 42 detected an unusual DLL module, which was later identified as part of the SnipBot malware toolkit. Researchers reconstructed the infection chain and post-infection activities. SnipBot operates through several stages, with the initial infection typically delivered via phishing emails containing a disguised executable file, often masked as a legitimate PDF.
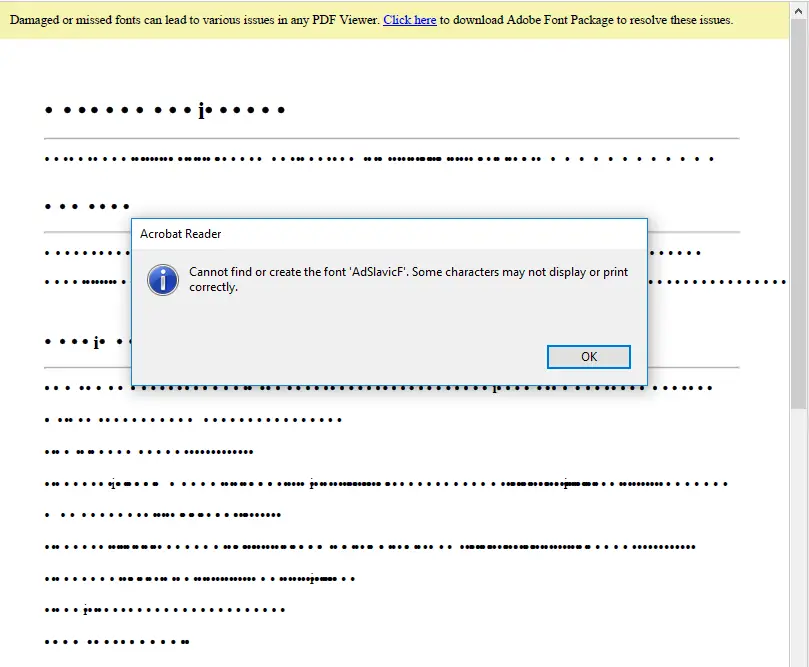
PDF lure document leading to the SnipBot downloader | Image: Unit 42
SnipBot takes advantage of stolen or fraudulent code-signing certificates, ensuring that the initial payload appears legitimate. However, subsequent modules remain unsigned, making detection more challenging. The malware also employs several anti-sandbox techniques, such as process name validation and registry key checks, further complicating analysis.
Once inside a victim’s system, SnipBot grants attackers extensive control, enabling them to execute commands, gather system information, and exfiltrate data. The malware also can download additional malicious payloads, including modules like SnippingTool.dll and svcnet.exe, which provide further functionality for the attacker.
One of the key post-infection activities observed by Unit 42 involved attackers attempting to gather data from a victim’s network, including domain controller information. The exfiltration process was initiated using legitimate tools like PuTTY and WinRAR, repurposed for malicious activities under false names like fsutil.exe and dsutil.exe.
While RomCom has historically been associated with ransomware and extortion campaigns, SnipBot’s behavior suggests a shift toward intelligence gathering and espionage. The targeted sectors, the choice of payloads, and the attackers’ careful post-infection movements imply a focus on data exfiltration rather than immediate financial gain.
Related Posts:
- RomCom Group’s Underground Ransomware Exploits Microsoft Zero-Day Flaw
- Two New Variants of the Spectre Vulnerability were found by Security researchers
- Palo Alto Networks’ Unit 42 Reveals a New Cyber Threat in China: Financial Fraud APKs
- New VMware Findings: Kernel Drivers’ Vulnerabilities Risk Total Device Takeover





