New Rust-Based Embargo Ransomware Threatens US Companies with Advanced Attack Techniques
A new and highly sophisticated ransomware group, Embargo, has been targeting companies in the US. First observed in May 2024, Embargo ransomware attacks have escalated rapidly, with the group deploying custom-made tools to bypass security systems and encrypt valuable data. According to ESET researchers, the group has shown to be well-resourced and adaptable, leveraging advanced techniques to avoid detection and increase ransom demands.
Embargo caught the attention of the cybersecurity community not only for its successful breaches but also for its use of the Rust programming language, making it part of a growing trend alongside other infamous groups like BlackCat and Hive. “Embargo chose Rust, a cross-platform programming language, allowing development of more versatile ransomware targeting both Windows and Linux,” ESET researchers note in their report. This flexibility allows Embargo to infect many systems, amplifying its impact.
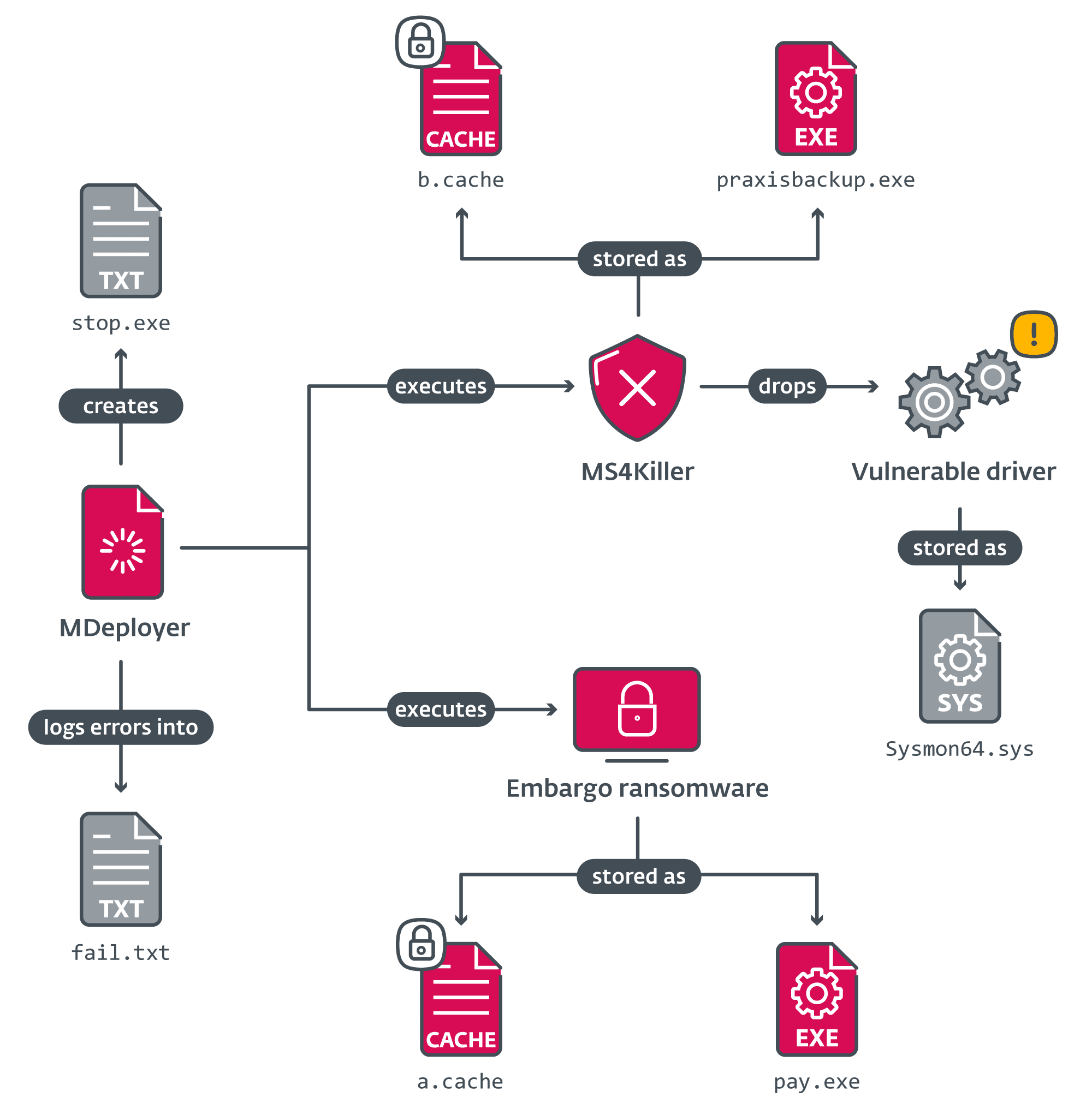
Embargo ransomware is typically deployed using MDeployer, a malicious loader that delivers the ransomware payload and the MS4Killer tool. MS4Killer is an “EDR killer” that disables endpoint detection and response (EDR) tools on compromised systems by exploiting a vulnerable driver, thereby clearing the way for the ransomware to execute without interference.
“The versions of MDeployer and MS4Killer observed in each intrusion differ slightly, suggesting that the tools are actively developed,” researchers explain. The attackers have shown a remarkable ability to adjust their tactics, often deploying different versions of MDeployer in a single attack to overcome obstacles. This flexibility makes Embargo particularly dangerous, as it can quickly evolve its methods to exploit weaknesses in a target’s defenses.
Embargo uses a double extortion strategy to pressure victims into paying. This involves not only encrypting data but also threatening to publish the stolen information on their leak site if the ransom is not paid. Communication with victims is conducted through their infrastructure, with the group also offering the option to communicate via Tox, an anonymous messaging platform.
The group operates under a Ransomware as a Service (RaaS) model, where affiliates can use their ransomware tools for a cut of the profits. As ESET researchers explain, “Given the group’s sophistication, the existence of a typical leak site, and the group’s claims, we assume that Embargo indeed operates as RaaS provider.”
One of the unique elements of Embargo’s approach is its meticulous attention to disabling security solutions. MDeployer works in conjunction with MS4Killer to neutralize antivirus and EDR tools, often exploiting Safe Mode, a minimal functionality state of Windows, to avoid detection. “The loader attempts to reboot the victim’s system into Safe Mode in order to disable selected security solutions,” explains ESET.
Once in Safe Mode, Embargo’s tools systematically disable security software by renaming installation directories and removing persistence mechanisms before executing the ransomware payload. This ensures that the ransomware can encrypt the system without being interrupted by cybersecurity defenses.
Additionally, the Embargo ransomware uses distinctive markers during its attacks, such as dropping ransom notes titled HOW_TO_RECOVER_FILES.txt and assigning encrypted files a random six-letter extension made of hexadecimal characters, e.g., .b58eeb or .3d828a.
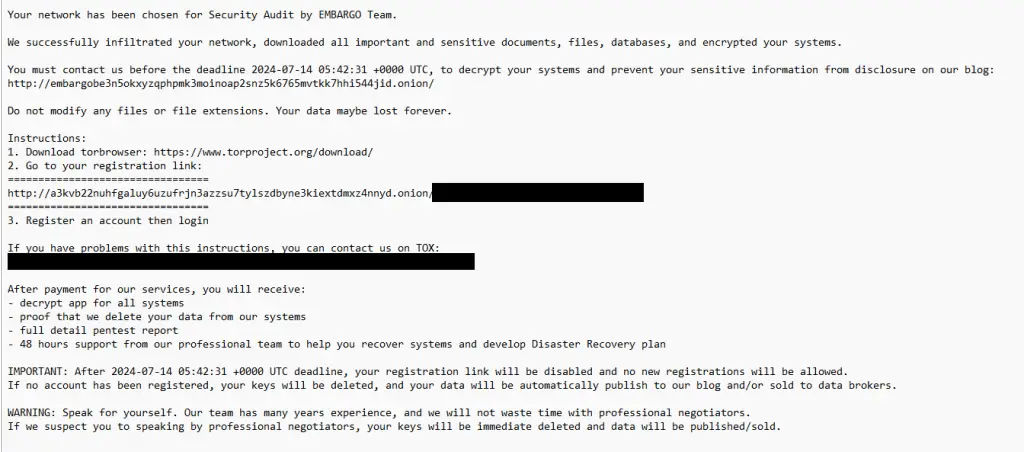
Embargo ransom note | Image: ESET
ESET’s analysis reveals that the group often deploys “multiple versions of the loader being used in a single incident,” suggesting that they refine their attacks on the fly. This makes them particularly challenging to defend against, as they can adjust their strategies to suit each victim’s environment.
“The attacker deploying the tools has the ability to quickly modify the source code and recompile their tools during an intrusion,” ESET researchers observe, underscoring the agility and resourcefulness of this group.





