New Trojan “MiyaRat” Unleashed by Bitter Group (APT-Q-37)
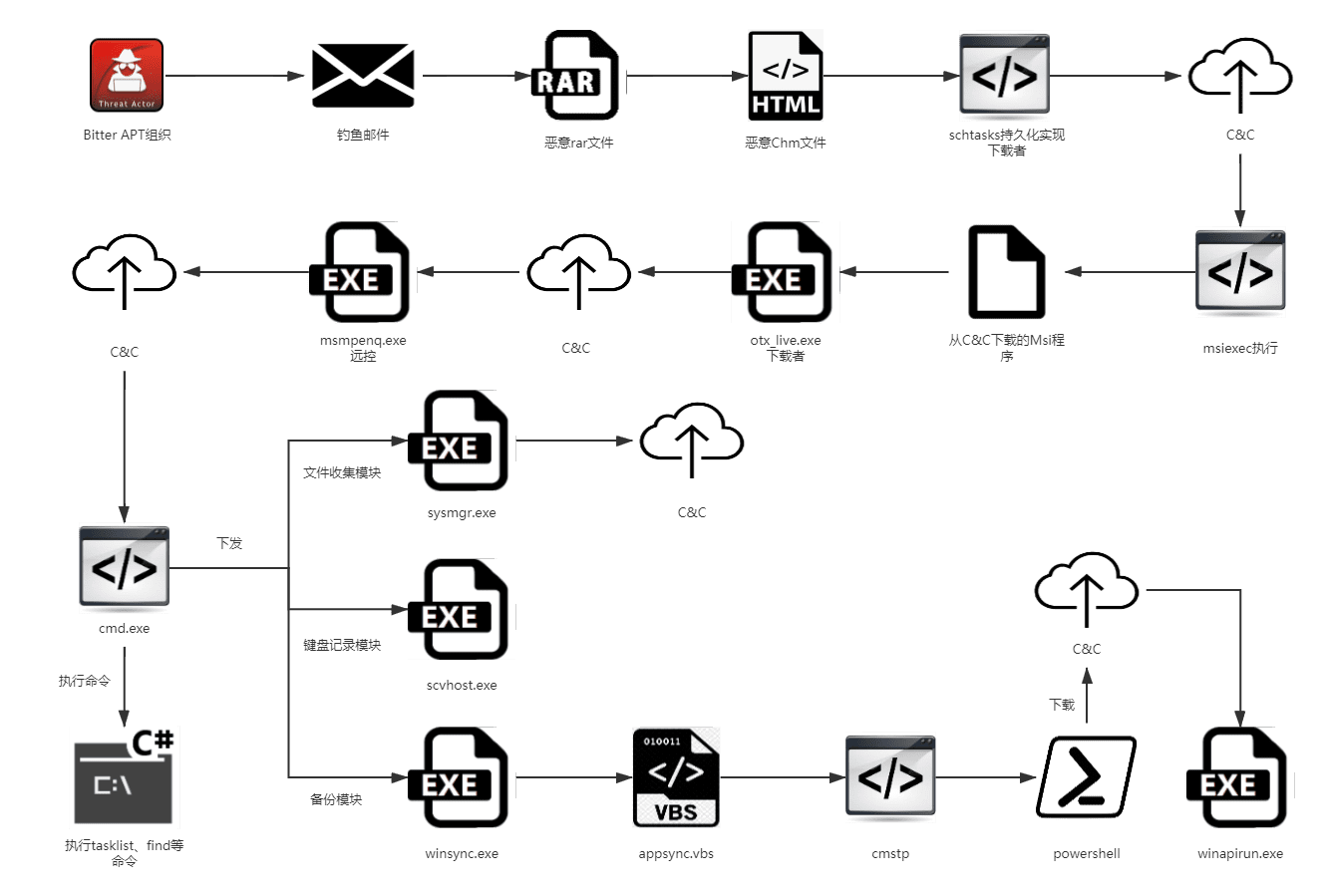
The QiAnXin Threat Intelligence Center recently reported the discovery of a new Trojan, dubbed “MiyaRat,” developed by the Bitter Group (APT-Q-37). This threat actor, known for targeting South Asian entities, continues its campaign with tactics aimed at bypassing detection through diverse attack methods and tools. As QiAnXin analysts explain, “The tactics of these groups have hardly changed much from 2019 to the present, and the attack technology The upper limit is low, but the phishing mode by casting a wide net can still affect government and enterprise customers to a certain extent.”
MiyaRat, named by the attackers in its Program Database (PDB) as “Miya,” was released as part of an MSI file (“mspnx.msi”). The Trojan’s operations begin with the decryption of the command-and-control (C2) domain “samsnewlooker.com” using a unique key, “doobiedoodoozie.” Once connected to the C2 server, the Trojan initiates a series of data-collecting processes, including gathering disk information, machine name, username, and even system version.
MiyaRat is particularly powerful in its capabilities, enabling comprehensive control over infected systems. The Trojan’s command repertoire includes functions such as file enumeration, command execution, file transfer, and even capturing screenshots. One of the standout features is the command SH1cmd, which establishes a shell for command execution, allowing attackers to execute commands directly on the compromised machine. The SFS command facilitates file transfers, employing subcommands UPL1 and DWNL for upload and download operations, respectively.
While the Bitter Group has traditionally relied on outdated techniques like CHM and LNK files, MiyaRat represents a shift toward more sophisticated evasion strategies. This year, the group attempted to use various methods, including PowerShell and even a steganography plugin. However, as QiAnXin noted, “the effect was not very satisfactory, and ultimately [they] distributed a brand new trojan horse, MiyaRat, in September.”
QiAnXin advises organizations to deploy Endpoint Detection and Response (EDR) solutions across both office and server environments to help detect and block generic threats. “We recommend our clients to deploy QAX Endpoint Detection and Response (EDR) in both office area and server area, which can realize the discovery and blocking of generic threats such as chm and lnk with the cloud checking function enabled,” QiAnXin states in the report.



