NuGet’s Stealth Malware: The Hidden SeroXen RAT Threat
Cybersecurity experts are sounding the alarm bells after ReversingLabs discovered alarming connections between a recent malicious campaign identified by Phylum and numerous malicious packages found on the NuGet package manager since early August. These revelations provide irrefutable evidence of a persistent and evolving cyber threat campaign.
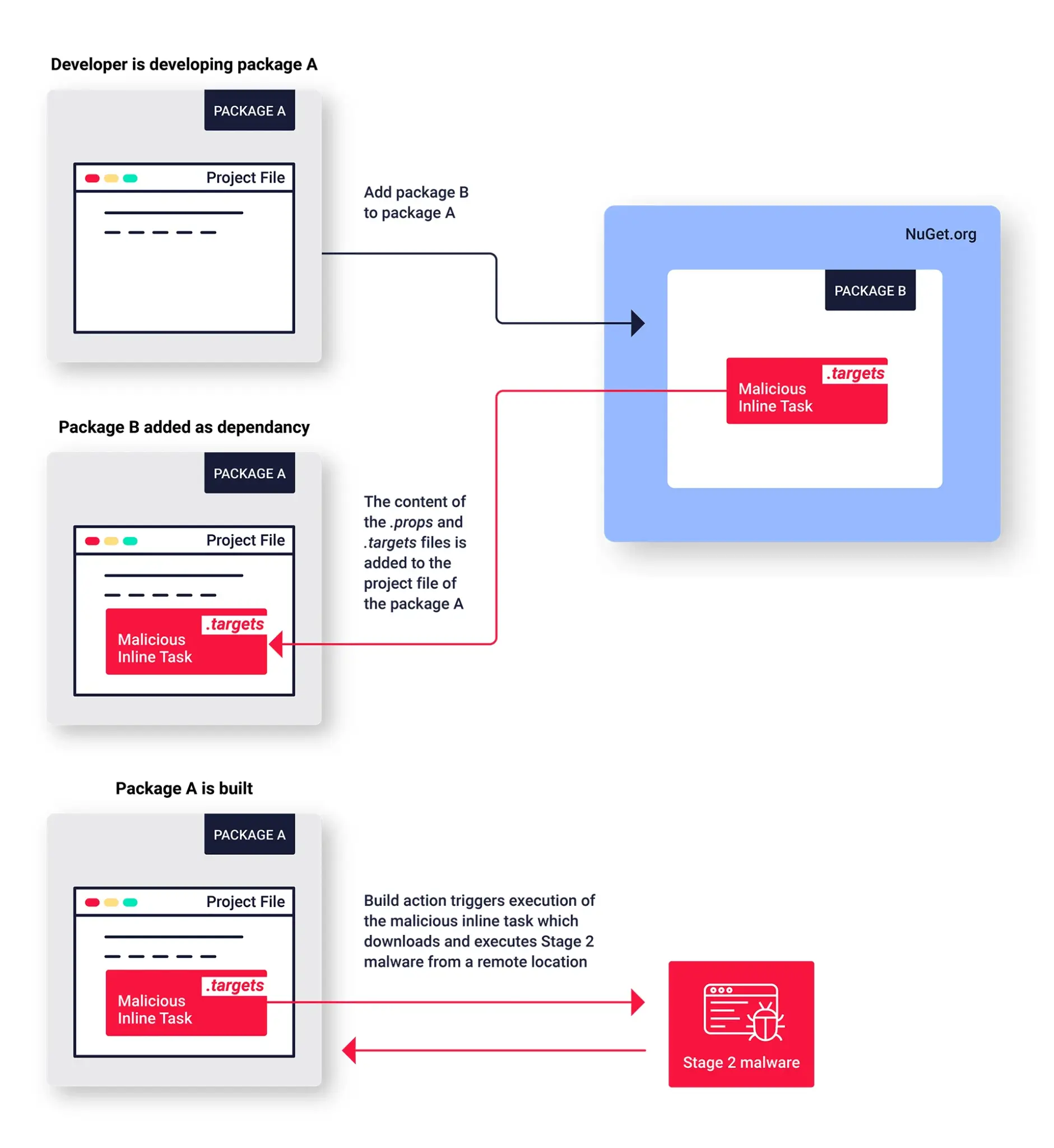
Threat actors, who once relied on simple downloaders run within install scripts, have since upgraded their arsenal. Now, they exploit NuGet’s MSBuild integrations feature, a more sophisticated technique, which the cyber community had only suspected until recently. Three packages, namely ZendeskApi.Client.V2, Betalgo.Open.AI, and Forge.Open.AI, were found to be typosquatting on well-known Nuget packages. They employed a unique code execution technique, setting them apart from traditional malware on NuGet.

Utilizing MSBuild integrations to execute malicious code in NuGet packages | Image: ReversingLabs
Most malware on NuGet embeds malicious code within initialization and post-installation PowerShell scripts. However, these specific packages took a different route. The rogue functionality was nested within the <packageID>.targets file in their “build” directory, a technique previously observed in version 6.5.3 of the Pathoschild.Stardew.Mod.Build.Config package.
A deep dive revealed that this novel execution technique traces its origins back to the “IAmRoot” package created by C. Augusto Proiete in 2019. Crafted to show that any NuGet package could run code on a user’s machine, IAmRoot exploited MSBuild integrations that were initially added to NuGet v2.5 to support native projects. However, these integrations can allow malicious inline tasks containing executable code to run when certain packages are built. The cybersecurity community has been aware of the potential risks of such mechanisms, but so far, solutions remain elusive. And now, the chickens are coming home to roost.
Upon further analysis, the three aforementioned packages were found to be part of a massive campaign initiated in August. These packages and Pathoschild.Stardew.Mod.Build.Config share striking similarities, especially in the .targets file. The culprits behind these packages also employed obfuscation techniques to fly under the radar, shifting their download source from an attacker-controlled IP to GitHub repositories. Notably, ReversingLabs detected and reported these packages within 24 hours of their publication, highlighting their proactiveness.
But the threat landscape is shifting rapidly. Just a week after the discovery of these packages, new sets of benign-appearing packages surfaced on NuGet. Within days, malicious versions were rolled out, imitating popular packages from renowned NuGet publishers. Their subterfuge was detailed, from mimicking icons to creating package names that differed by just a dot, making detection a challenge for the unsuspecting developer.
Connecting the dots, there are apparent ties between these latest packages and a typosquatting campaign described by Phylum in early October. The campaign delivered the SeroXen RAT and relied on PowerShell scripts inside the NuGet package for execution. This older campaign, however, was noisier and arguably less sophisticated than the recent packages, but their links are undeniable.
In conclusion, the NuGet package manager is under the spotlight as malicious actors relentlessly exploit its vulnerabilities. The tech community must remain vigilant and proactive in the face of these evolving threats, continually updating cybersecurity practices and encouraging developers to scrutinize every package they use.





