OfflRouter Virus: A Persistent Threat in Ukraine Exploiting Confidential Documents
Cisco Talos security researchers have uncovered a persistent, multi-component virus known as OfflRouter that has been quietly infecting Ukrainian systems and stealing sensitive documents since 2015. This unusual malware highlights the enduring dangers of legacy file formats and the importance of proactive threat hunting.
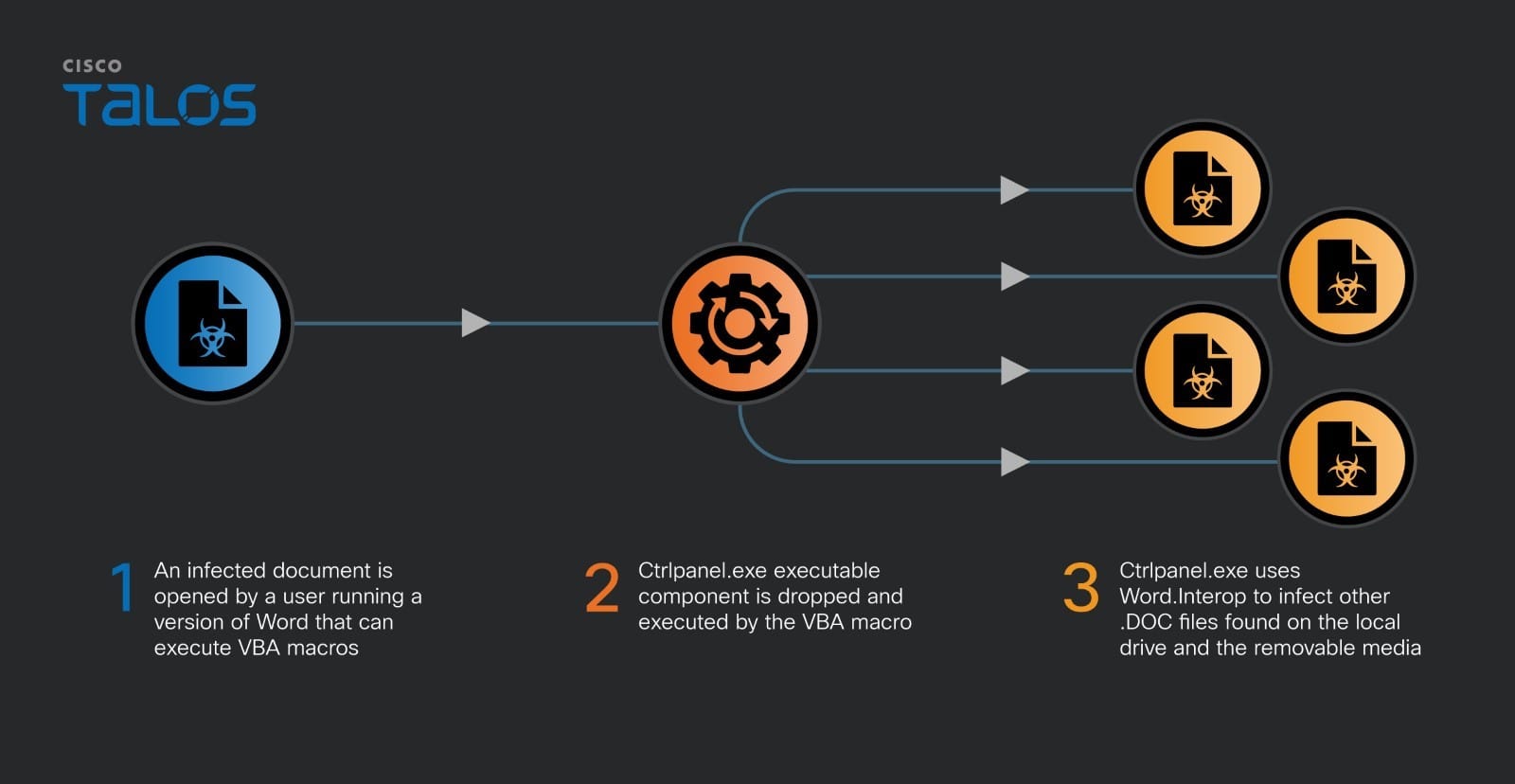
OfflRouter infects documents through a rare infection mechanism that utilizes .NET interop functionality. The virus specifically targets Microsoft Word documents with the “.doc” extension, a format still used by some organizations, despite being less common than the newer “.docx”. The malware is delivered via VBA (Visual Basic for Applications) macros embedded within these documents.

Infected Word documents drop the .NET component that infects other documents.
Upon execution, these macros deploy an executable named ctrlpanel.exe, which operates as the primary payload. This executable has been poorly masked by the malware’s developer—evident from programming errors and lack of testing—revealing the likely inexperience of its creator. However, the design choices made during its development have allowed OfflRouter to stay under the radar and limit its spread within Ukraine for nearly a decade.
The infection process is intriguing due to its simplicity and effectiveness. The virus utilizes the .NET module to infect documents by generating VBA code from hard-coded strings combined with encoded bytes of the ctrlpanel.exe binary. This approach makes each infection cycle relatively predictable and easier to detect but has still managed to persist undetected for many years.
Once the infected Word document is opened and macros are enabled, the virus begins its operation. It first checks the presence of the executable on the system, then executes it if not already running. The executable then uses threading timers to manage its operations, which include document infection and scanning for potential plugin modules.
OfflRouter’s spreading mechanism is limited to document sharing and removable media like USB sticks, as it cannot propagate through email. The virus also checks the list of recent Word documents to attempt further infections, contributing to its spread across connected drives.
Despite its confinement to Ukraine—likely due to the initial documents being in Ukrainian—OfflRouter represents a significant threat due to its potential to leak sensitive information. The infected documents discovered date back several years and include potentially sensitive data from government and police organizations.
The OfflRouter case is a compelling reminder that even legacy threats and coding errors shouldn’t be underestimated. A lack of cybersecurity awareness, coupled with outdated software and systems, creates fertile ground for persistent malware. Organizations must adopt a multi-layered defense strategy combining robust security tools, constant vigilance, and ongoing user education to effectively combat these evolving threats.