omnibus: OSINT Omnibus
Omnibus
An Omnibus is defined as a volume containing several novels or other items previously published separately and that is exactly what the InQuest Omnibus project intends to be for Open Source Intelligence collection, research, and artefact management.
By providing an easy to use interactive command line application, users are able to create sessions to investigate various artefacts such as IP addresses, domain names, email addresses, usernames, file hashes, Bitcoin addresses, and more as we continue to expand.
This project has taken motivation from the greats that came before it such as SpiderFoot, Harpoon, and DataSploit. Much thanks to those great authors for contributing to the world of open source.
The application is written with Python 2.7 in mind and has been successfully tested on OSX and Ubuntu 16.04 environments.
As this is a pre-release of the final application, there will very likely be some bugs and uncaught exceptions or other weirdness during usage. Though for the most part, it is fully functional and can be used to begin OSINT investigations right away.
Omnibus is built in a modular manner that allows the easy addition, or removal, of OSINT plugins. Each module is included in a single directory, and by adding a few lines of code, your module could be the next one!
Modules
Omnibus currently supports the following list of modules. If you have suggestions or modules or would like to write one of your own, please create a pull request.
Also, within the Omnibus console, typing the module name will show you the Help information associated with that module.
Modules
- Blockchain.info
- Censys
- ClearBit
- Cymon
- DNS subdomain enumeration
- DNS resolution
- DShield (SANS ISC)
- GeoIP lookup
- Full Contact
- Gist Scraping
- GitHub user search
- HackedEmails.com email search
- Hurricane Electric host search
- HIBP search
- Hunter.io
- IPInfo
- IPVoid
- KeyBase
- Nmap
- PassiveTotal
- Pastebin
- PGP Email and Name lookup
- RSS Feed Reader
- Shodan
- Security News Reader
- ThreatCrowd
- ThreatExpert
- TotalHash
- URLVoid
- VirusTotal
- Web Recon
- WHOIS
Install
git clone
Use
python2.7 omnibus-cli.py
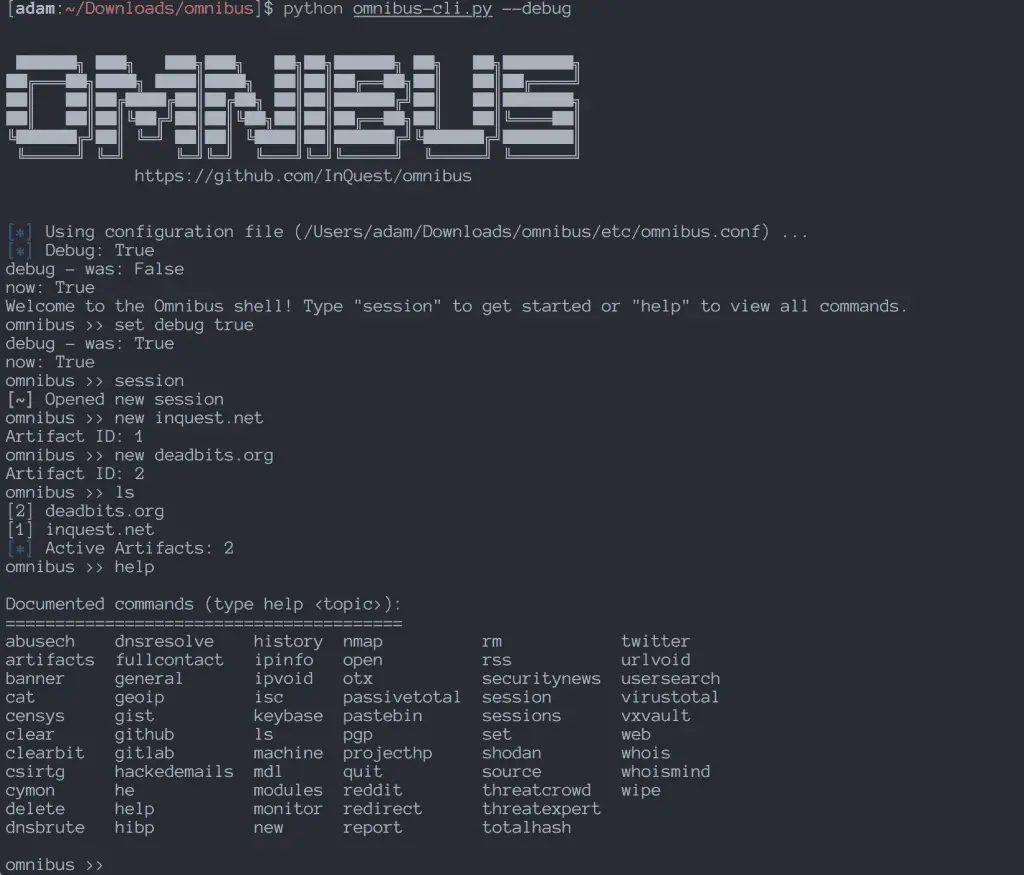
For a visual reference of the CLI, pictured above is the Omnibus console after a new session has been started, 2 artefacts have been added to a session, and the help menu is shown.
API Keys
You must set any API keys you’d like to use within modules inside the omnibus/etc/apikeys.json file. This file is a JSON document with placeholders for all the services which require API keys and is only accessed by Omnibus on a per module basis to retrieve the exact API key a module needs to execute.
It should be noted that most of the services requiring API keys have free accounts and API keys. Some free accounts may have lower resource limits, but that hasn’t been a problem during smaller daily investigations or testing the application.
A handy tip: Use the cat apikeys command to view which keys you do in fact have stored. If modules are failing, check here first to ensure your API key is properly saved.
Copyright (c) 2018 InQuest, LLC.