One-Day Exploits, Stealthy Tactics: Why Raspberry Robin Worm is a Cybersecurity Nightmare
Raspberry Robin has emerged as a significant point of interest among cybersecurity experts. First identified by Red Canary in 2021, this worm has demonstrated a sophisticated level of adaptability and innovation, capturing the attention of researchers and security analysts worldwide. Recently, security researchers from cybersecurity company Check Point analyzed this worm in detail.
Raspberry Robin operates within a vast malware ecosystem, serving as an initial access broker for further malicious deployments by various cybercrime groups, including notable entities like EvilCorp and TA505. Its role in facilitating additional malware attacks underscores its critical position in the cybercriminal infrastructure.
The worm has shown remarkable persistence and ingenuity in its evolution. It continuously adopts new tactics, techniques, and procedures (TTPs), making it increasingly challenging to analyze and mitigate. Notably, Raspberry Robin exploits vulnerabilities with remarkable speed, often utilizing 1-day exploits that are not publicly known at the time of their use. This proactive approach to leveraging vulnerabilities, such as the exploit for CVE-2023-36802, highlights its sophistication and the threats it poses to global cybersecurity.

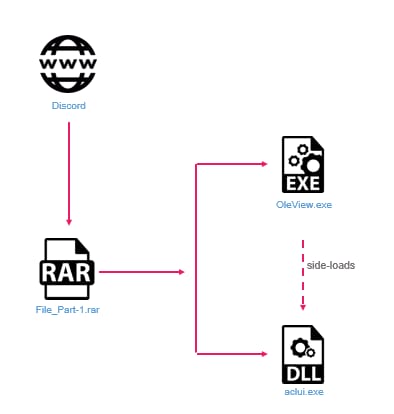
The Raspberry Robin attack flow
Raspberry Robin’s modus operandi involves multiple initial access vectors, with a common method being the use of disguised LNK files. Recent campaigns have seen the worm distributed via archive files on platforms like Discord, containing a mix of legitimate and malicious files designed to execute the worm’s payload discreetly.
The worm employs advanced techniques for privilege escalation, exploiting vulnerabilities specifically targeted at certain Windows versions and builds. Its use of encrypted exploits and the ability to inject these into processes like cleanmgr.exe showcase its adaptability and focus on stealth and effectiveness.
Moreover, Raspberry Robin has refined its evasion and persistence mechanisms. It incorporates checks against security product hooks, employs methods to avoid detection by system processes, and utilizes novel techniques to maintain operation even during system shutdowns. Its lateral movement tactics have also evolved, indicating a strategic approach to spreading within affected networks.
The communication strategy of Raspberry Robin has seen adaptations, with the worm now testing connections to legitimate Tor domains before attempting to communicate with its command and control (C2) servers. This shift signifies an increased emphasis on avoiding detection and maintaining operational security.
“Due to the rapid turnover in the exploits used, we also assume that Raspberry Robin will keep using new exploits for vulnerabilities that as of the first time they are used still have no public POC,” the researcher concluded.