Open Door Under Linux: Hackers Surf a Wave of Server Breaches
In the vast expanse of the digital ocean, a new wave of cyber attacks has emerged, targeting the seemingly unassuming Linux SSH servers. These attacks, meticulously analyzed by the experts at AhnLab Security Emergency Response Center (ASEC), reveal a sophisticated modus operandi aimed at exploiting vulnerabilities in poorly managed servers.
At the heart of these attacks lies a devious plan: to install malware, notably DDoS bots and CoinMiners, onto vulnerable systems. But the journey to this end is far from straightforward. It begins with gathering essential information – the IP address and SSH account credentials of the target. This reconnaissance phase involves IP scanning to identify servers with an active SSH service or port 22.
Once potential targets are pinpointed, the attackers deploy brute force or dictionary attacks to crack the IDs and passwords. This approach not only grants them access to the servers but also allows them to install additional malware that can perform similar scanning and brute force attacks, perpetuating a cycle of vulnerability exploitation.
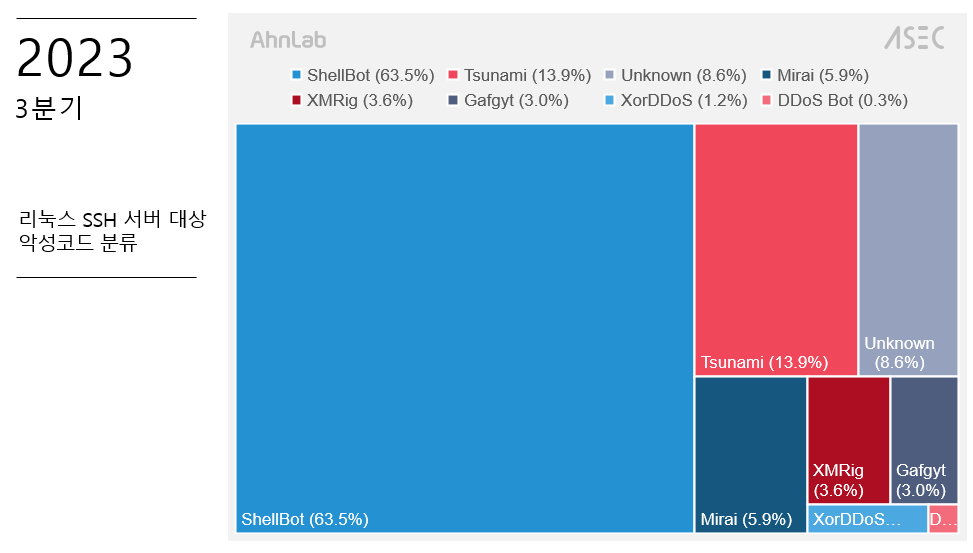
Among the common malware installed during these attacks are names that resonate with ominous tones in the cybersecurity world: ShellBot, Tsunami, ChinaZ DDoS Bot, and XMRig CoinMiner. Each piece of malware serves a distinct purpose, from hijacking system resources for cryptocurrency mining to launching devastating Distributed Denial of Service (DDoS) attacks.
Interestingly, these threat actors don’t always install malware directly. In some cases, they choose to install only scanners, selling the breached IP and account credentials on the dark web. This strategy exemplifies the multifaceted nature of these attack campaigns, where direct damage is only one facet of a broader, more insidious threat.
An in-depth analysis of the attack process unveils a meticulous sequence. After successfully logging in using stolen credentials, the threat actor executes a series of commands. These include checking the number of CPU cores, downloading a compressed file containing a port scanner and an SSH dictionary attack tool, and executing these tools to widen the net of compromised systems.

Classification of malware targeting Linux SSH servers in Q3 2023 | Image: ASEC
A notable aspect of these attacks is the usage of scripts like ‘go’, ‘gob’, and ‘rand’, each serving a specific function in scanning IP addresses and launching further attacks. The ultimate goal is clear: to identify as many vulnerable systems as possible and exploit them for either direct attacks or further reconnaissance.
In response to this escalating threat, ASEC strongly advises administrators to bolster their defenses. This includes using robust, hard-to-guess passwords, regularly changing them, updating systems with the latest patches, and employing security measures like firewalls to restrict unauthorized access.
Moreover, real-time collection of attack source addresses using Linux SSH Honeypots and the deployment of up-to-date security programs are critical steps in preemptively blocking malware infection.





