Memory addressing principle In the network security incident analysis, will encounter memory addressing knowledge. Today, i am going...
Today, big data platform, big data analysis, big data applications have been developed in full swing. Our...
Managing network traffic is one of the toughest tasks that system administrators must deal with. We must...
Keybase is an official multi-platform utilities for composing ENCRYPTED messages to any Twitter, Facebook, Reddit, HackerNews, or...
In the case of project management with Git, there are some frequently encountered problems that are complicated...
Recently, security researchers have discovered a new malware. The malware, like WannaCry extortion software, spreads itself by...
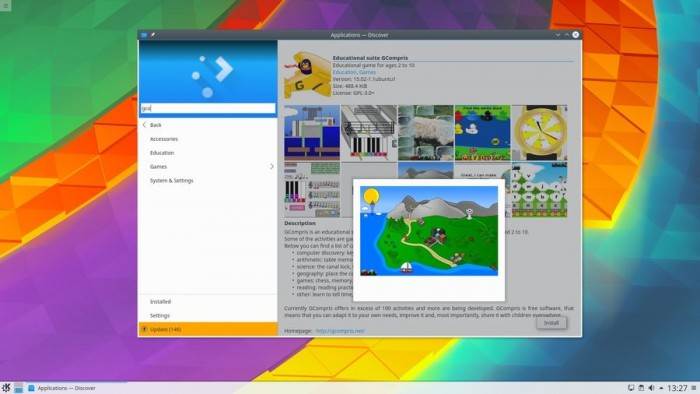
KDE today announced the KDE Plasma 5.13 desktop environment ushered in the first seven maintenance updates. KDE...
What is a robots.txt file? Search engine through a program robot (also known as spider), automatically access...
A function that often needs to be used to locate a network failure in a process is...
GoTTY is a simple command line tool that turns your CLI tools into web applications. GoTTY 1.0.0...
A Fork Bomb is a denial of service attack in the computer field using a system call...
Steganography is the art and science of writing hidden messages in such a way that no one,...
Due to large-scale worm struck, the most urgent thing is to close windows 445/137/138/139 port, where several options...
Using curl + Plain text formatted output + JSON formatted output + XML formatted output + Get...
Grml is a Debian based live system focusing on the needs of system administrators. This Grml release...