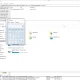
Pastejacking: Attack vector

Browsers now allow developers to automatically add content to a user’s clipboard, following certain conditions. Namely, this can only be triggered by browser events. This post details how you can exploit this to trick a user into running commands they didn’t want to get run and gain code execution.
It should also be noted, for some time similar attacks have been possible via html/css. What’s different about this is the text can be copied after an event, it can be copied on a short timer following an event, and it’s easier to copy in hex characters into the clipboard, which can be used to exploit VIM, all shown below.
Impact
This method can be combined with a phishing attack to entice users into running seemingly innocent commands. The malicious code will override the innocent code, and the attacker can gain remote code execution on the user’s host if the user pastes the contents into the terminal.
Demo
Reference: Github