pFuzz: bypass web application firewall
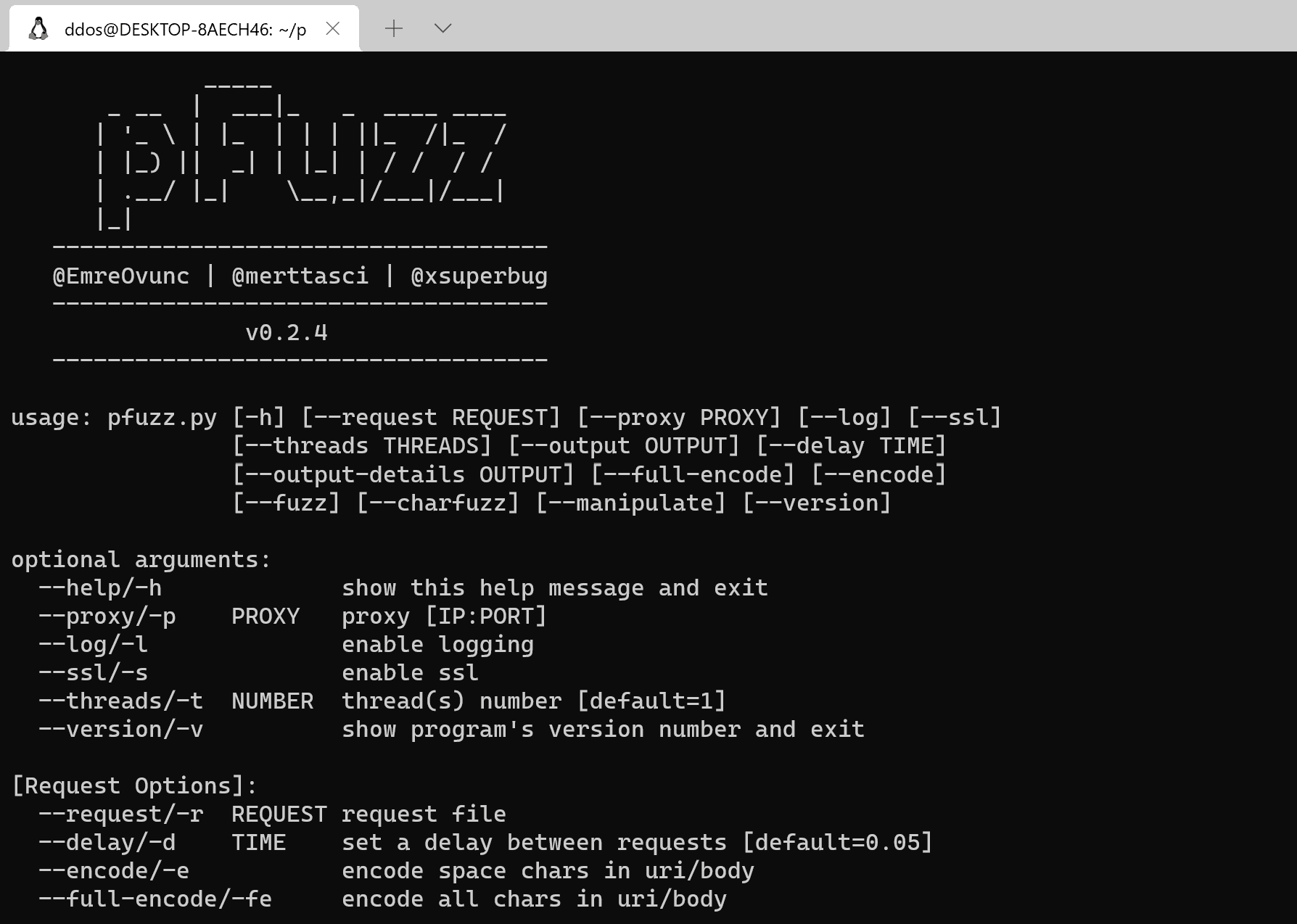
What is pFuzz
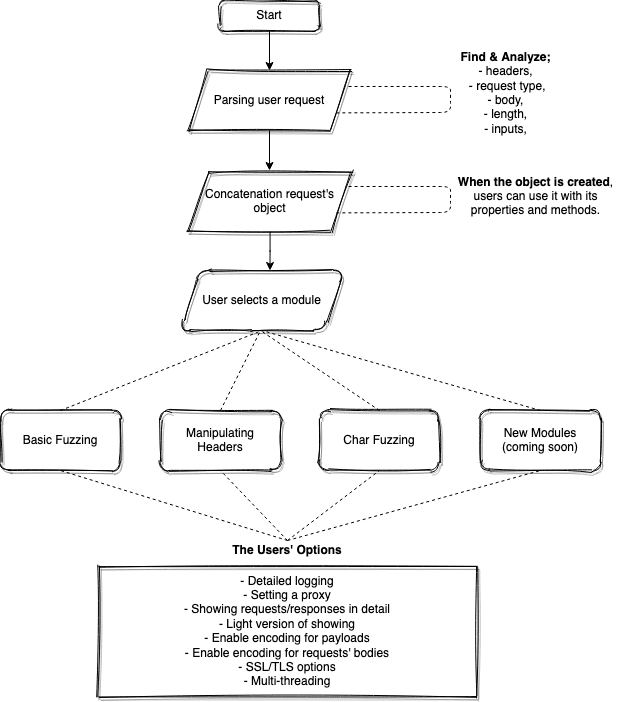
pFuzz is a tool developed in the python language to have advanced fuzzing capability in web application research. Since the application has a modular structure, it has the ability to quickly add new found / to be found WAF bypassing methods to pFuzz and test it on all other WAFs. In addition to a modular structure, multi-threading, multi-processing, and queue structures have been used to make the tool more flexible and the infrastructure has been created for future developments.
The tool is programmed so that a given request can be parsed and easily changed over an object. Thanks to this structure, those who will develop the application will be able to contribute easily and develop the tool in line with their own needs without changing the core structure of the application without having to learn.
What WAFs did we bypass?
- FortiWeb
- Cloudflare
- Sucuri
- Akamai
- Imperva
- F5 WAF
Install
git clone https://github.com/RedSection/pFuzz.git
sudo pip3 install virtualenv
python3 -m venv myvenv
source myvenv/bin/activate
pip3 install -r requirements.txt
python3 pfuzz.py –help
Use

Example
Manipulating Headers Module
python3 pfuzz.py -r request.txt -m
Charfuzzing Module
python3 pfuzz.py -r request.txt -cf
Fuzzing Module
python3 pfuzz.py -r request.txt -f
Add proxy
python3 pfuzz.py -r request.txt -f –proxy 127.0.0.1:8080
Add a delay between requests
python3 pfuzz.py -r request.txt -f -d 3
Enable TLS/SSL connection
python3 pfuzz.py -r request.txt -f -s
Enable logging
python3 pfuzz.py -r request.txt -f -l
Enable payload encoding/full-encoding function
python3 pfuzz.py -r request.txt -f -e
python3 pfuzz.py -r request.txt -f -fe
Set multi-threads
python3 pfuzz.py -r request.txt -f -t 5
Output to the terminal
python3 pfuzz.py -r request.txt -f -o terminal
python3 pfuzz.py -r request.txt -f -od terminal
Output to a file
python3 pfuzz.py -r request.txt -f -o ~/Desktop/
python3 pfuzz.py -r request.txt -f -od ~/tmp/
Tutorial
Copyright (C) 2021 RedSection





