Philips VUE PACS Vulnerabilities Expose Healthcare Sector to Cyberattacks
Philips, a leading health technology company, recently disclosed multiple vulnerabilities in its Vue Picture Archiving and Communication System (PACS), a widely used medical imaging solution. These vulnerabilities, ranging from high to critical severity, could potentially allow attackers to gain unauthorized access to sensitive patient data, disrupt critical medical services, and even manipulate diagnostic information.
Philips VUE PACS is an advanced system designed to manage, store, and transmit digital medical images and reports. Used predominantly in hospitals, diagnostic imaging centers, and other healthcare facilities, it integrates seamlessly with Electronic Medical Records (EMR) and Radiology Information Systems (RIS). This integration facilitates the efficient storage and retrieval of images from various modalities such as X-rays, MRI, CT scans, and ultrasound, thereby enhancing diagnostic accuracy and patient care.
Among the thirteen vulnerabilities reported to government agencies, including the U.S. Cybersecurity Infrastructure and Security Agency (CISA), several have been categorized as high and critical severity. These vulnerabilities, if exploited, could allow attackers to gain unauthorized access to sensitive patient data, disrupt critical medical services, and manipulate diagnostic information.
Key Vulnerabilities Include:
- CVE-2020-36518: Out of Bounds Write (CVSS 7.1)
- CVE-2020-11113: Deserialization of Untrusted Data (CVSS 8.8)
- CVE-2020-35728: Deserialization of Untrusted Data (CVSS 9.3)
- CVE-2021-20190: Deserialization of Untrusted Data (CVSS 9.3)
- CVE-2020-14061: Deserialization of Untrusted Data (CVSS 9.3)
- CVE-2020-10673: Deserialization of Untrusted Data (CVSS 8.7)
- CVE-2019-12814: Deserialization of Untrusted Data (CVSS 8.7)
- CVE-2017-17485: Deserialization of Untrusted Data (CVSS 9.3)
- CVE-2021-28165: Uncontrolled Resource Consumption (CVSS 8.8)
- CVE-2023-40704: Use of Default Credentials (CVSS 8.4)
- CVE-2023-40539: Weak Password Requirement (CVSS 4.8)
- CVE-2023-40159: Exposure of Sensitive Information to an Unauthorized Actor (CVSS 8.8)
The vulnerabilities are particularly concerning due to their low attack complexity and remote exploitability. Cyble Research and Intelligence Labs (CRIL) identified 495 internet-exposed Philips VUE PACS instances, with the highest exposures observed in Brazil and the United States.
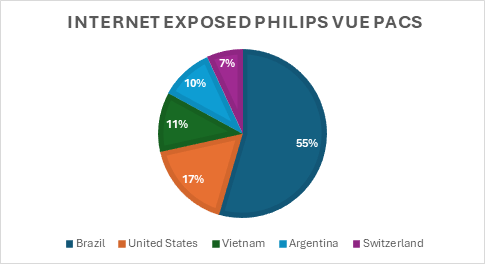
Image: CRIL
Philips has released patches to address these vulnerabilities and strongly recommends that all customers upgrade to the latest version of Vue PACS as soon as possible. The company has also provided mitigation guidance for customers who are unable to immediately upgrade.





