Phishing Campaign Targets World Agricultural Cycling Competition Attendees with Havoc C2 Malware
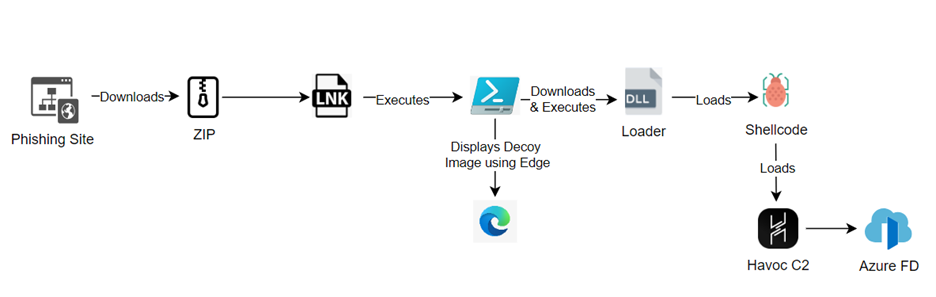
A recent report from Cyble Research and Intelligence Labs (CRIL) reveals a concerning phishing campaign that targeted participants and enthusiasts of the World Agricultural Cycling Competition (WACC). The attackers exploited the event’s popularity by creating a fake website mimicking the official WACC site and offering seemingly harmless event photos as bait.
The threat actor behind this campaign capitalized on the excitement following the real cycling event, which took place from June 7th to 9th. Shortly after the event concluded, the attacker launched a fake “PHOTO” section on the cloned website, purporting to offer official event photos for download. This was a calculated move, aimed at attracting participants and enthusiasts eager to view or download memories of the event.
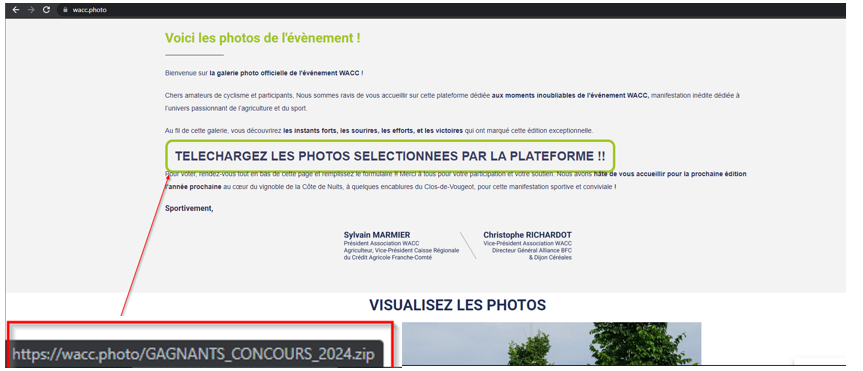
Downloading the ZIP file | Image: CRIL
However, instead of photos, the download offers a malicious ZIP file containing shortcut files disguised as images. When clicked, these files trigger a PowerShell script that stealthily downloads and executes a dangerous payload, all while displaying legitimate images to maintain the illusion of authenticity.
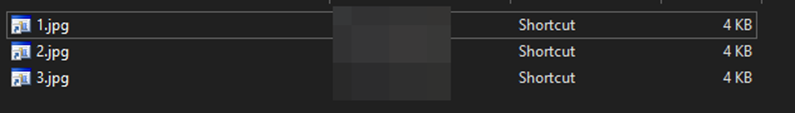
Contents of the Zip File | Image: CRIL
The ZIP file contains three .lnk files masquerading as images. Upon execution, these files initiate a PowerShell script that downloads actual images as decoys, displayed through Microsoft Edge. Simultaneously, the script covertly downloads and executes a malicious DLL file named “KB.DLL,” setting the stage for further compromise.
The real threat emerges as this DLL acts as a shellcode loader, deploying obfuscated shellcode designed to establish a connection with a command and control (C&C) server. This sophisticated post-exploitation framework, known as Havoc C2, is capable of executing a range of malicious activities, including lateral movement within networks, establishing persistence, and deploying additional malware payloads.
The shellcode leverages a clever technique to evade detection, executing under the guise of font enumeration—a method that helps it slip past conventional security defenses.
Although the C&C server was inactive during the CRIL analysis, preventing a full investigation, the deployment of Havoc C2 suggests a well-prepared attacker with potentially strategic objectives. The focus on the French agricultural sector hints at a targeted campaign, possibly aimed at compromising systems within this industry for long-term access and exploitation.
This campaign serves as a stark reminder of the increasing sophistication of phishing attacks and the need for heightened vigilance, especially in industries that may not traditionally consider themselves prime targets for cyberattacks.





