PixPirate Malware Evades Detection with Innovative Hiding Technique
IBM Trusteer researchers have uncovered a sophisticated Android trojan dubbed PixPirate, specifically targeting banking users in Brazil. This Remote Access Trojan (RAT) malware employs advanced evasion techniques, making it a potent threat with the potential to cause significant financial harm.
Core Technique: Icon-less Execution and Persistence

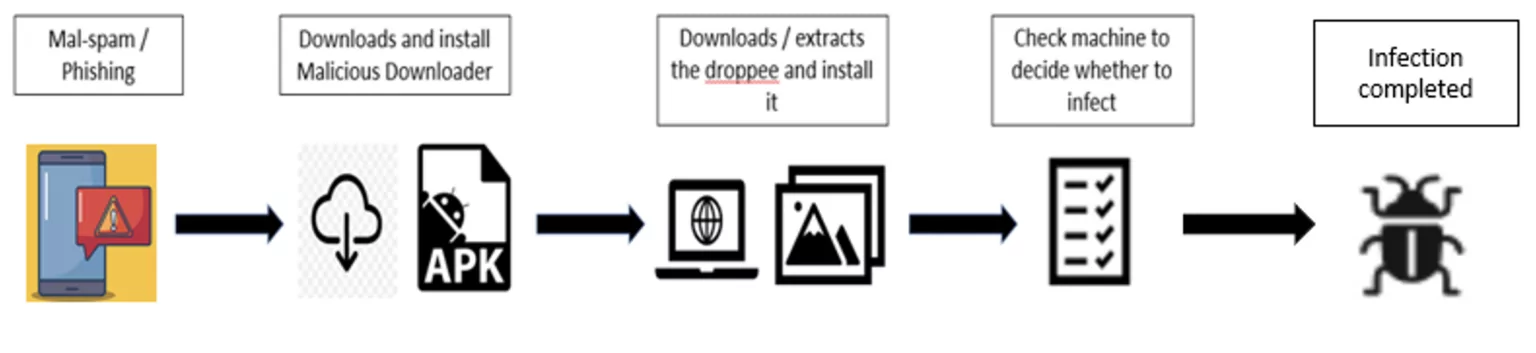
PixPirate infection flow | Image: IBM Trusteer
PixPirate has introduced an unprecedented technique of evasion, forgoing the traditional launcher icon for a more covert approach. By not having a main activity, PixPirate ensures its icon never appears on the victim’s home screen, making it virtually invisible. PixPirate departs from the traditional method of malware hiding by removing the application icon via the SetComponentEnabledSetting API. This technique, rendered obsolete by Android 10 security updates, is bypassed with an innovative approach:
- Two-Part Deployment: PixPirate uses a downloader and a droppee. The downloader masquerades as a legitimate app, tricking the victim into installation, and is responsible for both installing and launching the droppee.
- Service-Based Execution: The droppee crucially lacks a main activity definition in the manifest. Instead, it has an exported service with a custom action. The downloader binds to this service, effectively launching the hidden droppee.
- Persistence: This technique ensures the malware runs even if the downloader is removed, significantly hindering victim’s attempts to neutralize the threat.
RAT Capabilities and Fraudulent Activities
Victims are lured onto PixPirate’s deck through phishing messages via WhatsApp or SMS, enticing them to download what appears to be a legitimate banking authentication app. Once the hook is set, the downloader masquerades as an update, installing the PixPirate malware in disguise. Through cunning and deceit, PixPirate gains the necessary permissions under the guise of accessibility services. PixPirate abuses the Android accessibility service to achieve powerful RAT capabilities, including:
- Application manipulation and control
- Keylogging
- Device data collection (installed apps, device location, accounts)
- Anti-VM/Anti-Debugging
- SMS interception (for 2FA bypass)
- Google Play Protect circumvention
Focus on Pix Fraud: PixPirate’s primary attack vector targets Pix, the widely used Brazilian instant payment system. Fraud methods include:
- Credential Theft and Fraudulent Transfers: Malware silently steals login credentials, then initiates Pix transfers to attacker-controlled accounts.
- Man-in-the-Middle Transaction Tampering: PixPirate can intercept ongoing user-initiated Pix transfers and change recipient details to divert funds.
Automated and Remote Control Fraud
PixPirate automates its fraudulent activities with pre-coded routines for seamless execution. Additionally, it has a remote control capability whereby attackers can live-control the victim’s device through an overlay screen. This opens the door for a broader range of malicious activities.
Defense and Recommendations
The stealth and sophistication of PixPirate underscore the evolving threat landscape. To mitigate risks, users and organizations are advised to:
- Restrict App Installations: Avoid sideloading or downloading from unofficial sources.
- Security Awareness: Educate users on phishing tactics and the dangers of malicious apps.
- Advanced Endpoint Protection: Deploy robust endpoint security solutions capable of detecting behavioral anomalies and suspicious activities.
- Threat Intelligence: Actively track the latest threat actor techniques and malware developments.





