PoC Exploit Released for MacOS SUHelper Root Privilege Escalation (CVE-2022-22639)
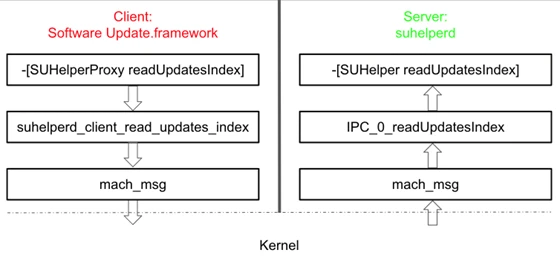
Mickey Jin, a security researcher from TrendMicro, has released proof-of-concept (PoC) exploit code for a MacOS SUHelper Root Privilege Escalation (CVE-2022-22639) vulnerability that Apple patched in March this year. This flaw has a CVSS score of 7.8 and affected iOS, iPadOS, and MacOS.

The PoC exploit targets CVE-2022-22639, a vulnerability that can lead to gain elevated privileges. This issue was found in the suhelperd, a helper daemon process for Software Update in macOS. “A class inside suhelperd, SUHelper, provides an essential system service through the inter-process communication (IPC) mechanism. The process runs as root and is signed with special entitlements, such as com.apple.rootless.install, which grants the process permission to bypass System Integrity Protection (SIP) restrictions. This combination of functionalities presents an attractive opportunity for malicious actors to exploit the vulnerability,” the researcher explains.
The vulnerability was addressed with the release of the macOS Monterey 12.3 security update. In light of the criticality of some of the issues, users running affected installations are highly recommended to upgrade to the latest version as soon as possible.





