PoC Released for Windows SysInternals Sysmon Privilege Escalation (CVE-2023-29343) Bug
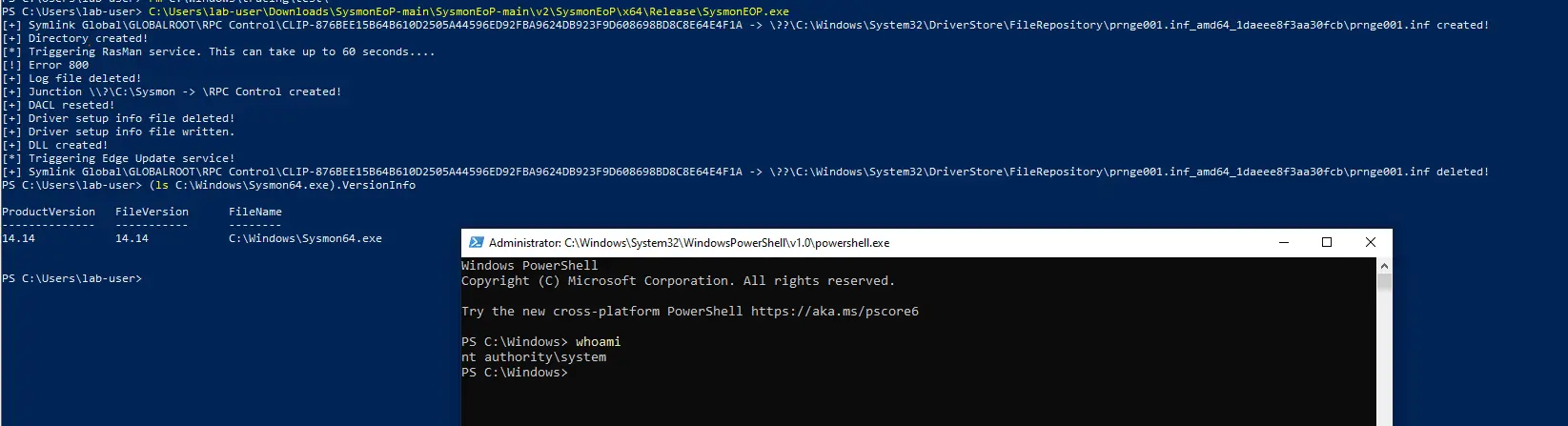
In the dynamic world of cybersecurity, threats are constantly evolving, necessitating vigilance from system administrators and everyday users alike. A proof-of-concept (PoC) exploit for the Microsoft Windows SysInternals Sysmon privilege escalation flaw, traced as CVE-2023-29343 has been publicly released by security researcher Filip Dragović. This Elevation of Privilege Vulnerability could potentially grant authenticated attackers the ability to obtain SYSTEM privileges, the highest level of authority in the Windows environment.
The bug at the heart of this issue involves the Sysmon tool, a Windows system service and device driver that monitors and logs system activity to the Windows event log. As Dragović has detailed, the issue lies in how Sysmon validates access and ownership of its archive directory.
After the last security patch, Sysmon was configured to check if the archive directory exists, and if so, confirm it is owned by the SYSTEM. Moreover, it ensured that access was granted exclusively to SYSTEM. Should both these conditions be met, Sysmon would proceed to write or delete files within this directory.

Image: Filip Dragović
Unfortunately, as Dragović noted, it’s not possible for low-privilege users to alter file or directory ownership. This necessitated the identification of a directory already owned by SYSTEM but granting full access—or at least WRITE_DAC, DELETE, and FILE_WRITE_ATTRIBUTES—to a low-privilege user or any group such a user might belong to.
Microsoft initially addressed the bug by releasing security updates on May 9th, urging all customers to immediately apply these patches to prevent potential exploitation attempts. Dragović’s proof-of-concept, however, highlights the continued need for system maintenance and security vigilance.
With the PoC exploit for CVE-2023-29343 now public, it’s likely that threat actors will scramble to exploit this vulnerability in a bid to carry out nefarious activities, including data theft, ransomware deployment, or other forms of cyber sabotage. Custom versions of the exploit could potentially target any unpatched Windows system, making this a critical concern for businesses and individual users who may not yet have implemented the provided patches.
Security vulnerabilities such as CVE-2023-29343 underscore the importance of diligent system upkeep and prompt application of security patches. To avoid falling victim to this bug, users should ensure their systems are updated with the latest patches and have strong security measures in place.





