PSKracker v0.3.1 releases: An all-in-one WPA/WPS toolkit
PSKracker is a collection of WPA/WPA2/WPS default algorithms/password generators/pingens written in C.
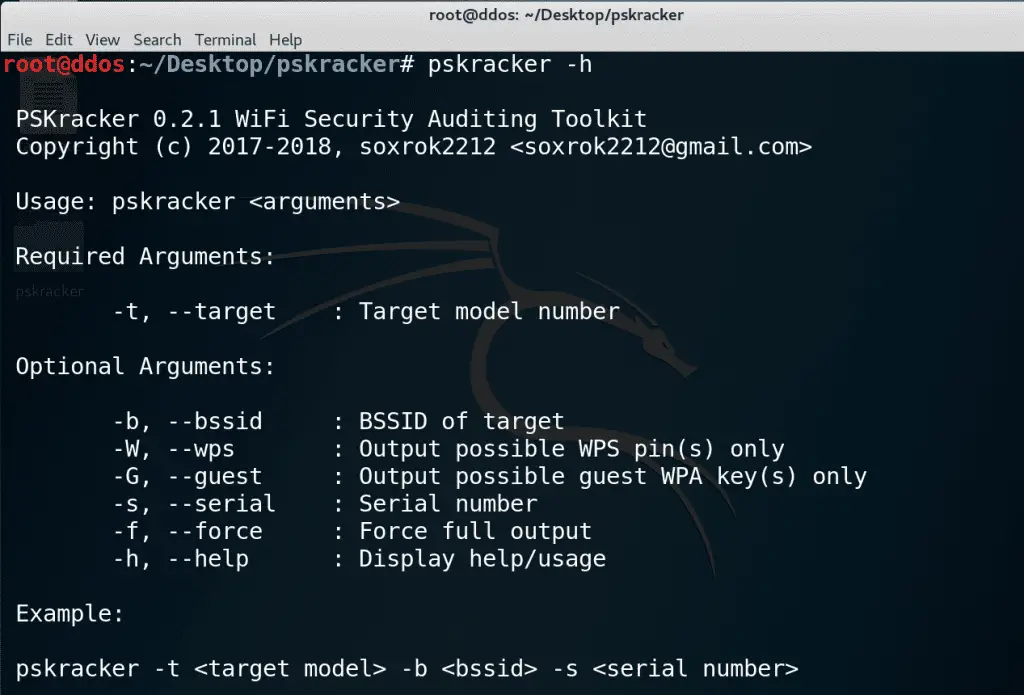
Attack Types
means PSKracker will output a large number of possible keys and should be piped into a password recovery tool, such as Hashcat.
means you will be given one (or a handful) of possible keys.
means you will be given one (or a handful) of possible WPS PINs.
means there are one or more dictionaries included in the ‘dicts’ folder.
means the bssid of the network is required.
- If there is a model in code tags listed, that is the option to use with the -t argument in pskracker.
Supported OS
PSKracker should compile on macOS, Windows (with Cygwin), and any Linux system.
It has been tested on macOS High Sierra 10.13.6, Windows 10, Ubuntu 16.04, Ubuntu 18.04 and ArchLinux. Embedded systems are not supported, though may still work. PSKracker is intended to be run on true pentesting environments (Desktop/Workstation/Laptop). Some psk generators (not bruteforce) are still suitable for embembedded systems, but I will not provide support due to the nature of the tool.
Changelog v0.3.1
- add older Belkin algorithm
- update Netgear wordlists and fix typo
- add small FiOS wordlist
- add optimized NVG589 algorithm (mrfancypants)
- ISP/manufacturers can be selected with -t
- -f outputs all possible keys for selected target (useful for checking various algorithms when the exact target model is unknown)
Install
git clone https://github.com/soxrok2212/pskracker cd pskracker/ make sudo make install
Usage
Disclaimer
This project is intended for testing and securing your own networks or networks you have permission to audit. This is not intended to be used maliciously.
Copyright (C) 2017 soxrok2212
Source: https://github.com/soxrok2212/
 means PSKracker will output a large number of possible keys and should be piped into a password recovery tool, such as Hashcat.
means PSKracker will output a large number of possible keys and should be piped into a password recovery tool, such as Hashcat. means you will be given one (or a handful) of possible keys.
means you will be given one (or a handful) of possible keys. means you will be given one (or a handful) of possible WPS PINs.
means you will be given one (or a handful) of possible WPS PINs. means there are one or more dictionaries included in the ‘dicts’ folder.
means there are one or more dictionaries included in the ‘dicts’ folder. means the bssid of the network is required.
means the bssid of the network is required.



