PyPI Poisoned: 116 Malicious Packages Target Windows and Linux
A recent ESET research study has shed light on a disturbing development in the Python Package Index (PyPI), the official repository for the Python programming language. The study uncovers a sophisticated web of malicious Python projects, revealing a pernicious potpourri of compromised code that targets both Windows and Linux systems.
The study, conducted using advanced malware detection techniques, identified 116 malicious packages in PyPI, distributed across 53 projects. These compromised packages, downloaded over 10,000 times, often delivered a custom backdoor capable of remote command execution, exfiltration, and even taking screenshots. In some instances, victims received a variant of the infamous W4SP Stealer or a simple clipboard monitor designed to steal cryptocurrency.

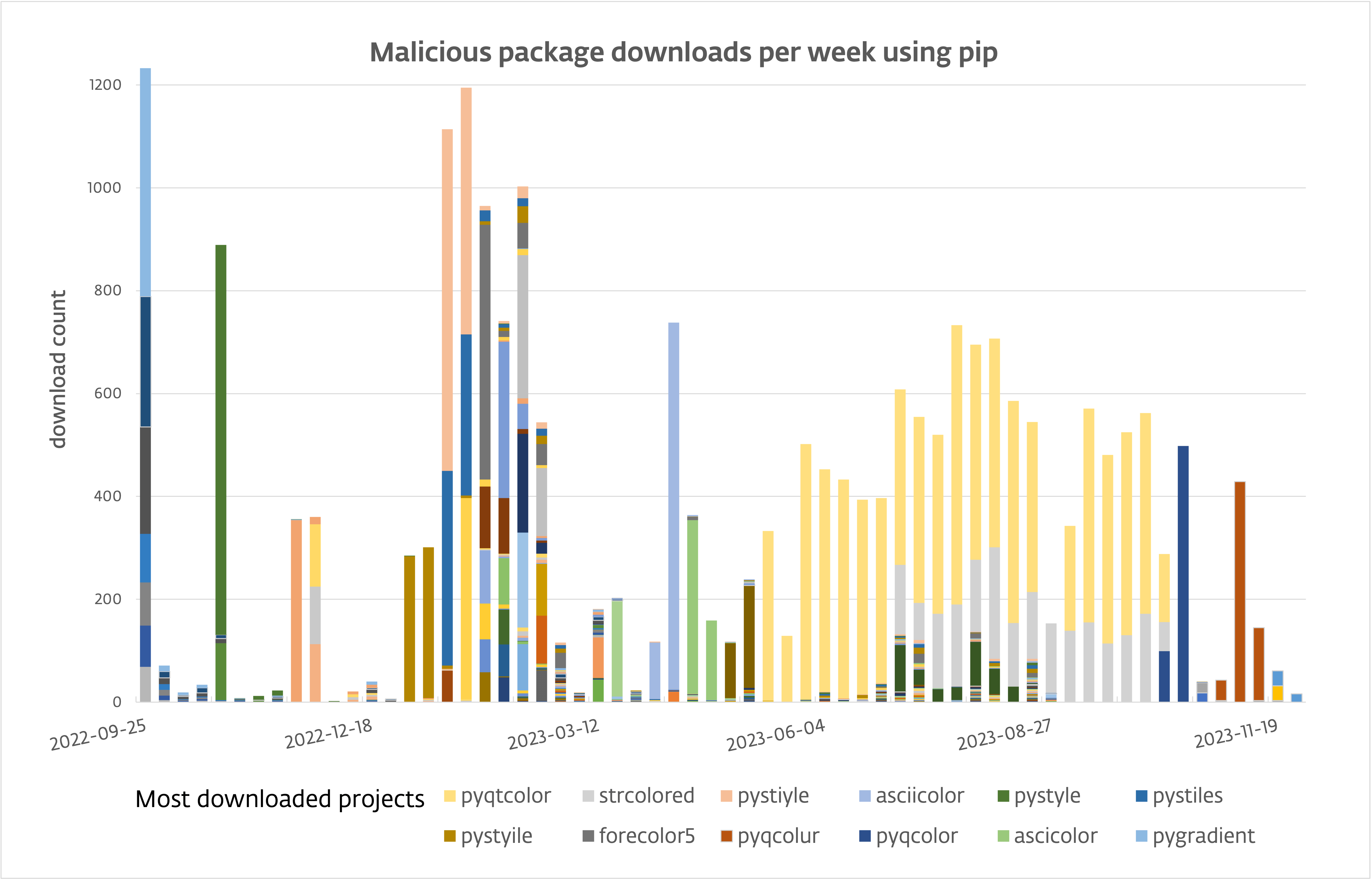
Malicious package downloads over the past year from PyPI using pip | Image: ESET
The operators behind these nefarious activities employed three primary techniques to insert malicious code into Python packages:
1. Malicious `test.py` Module: A ‘test’ module with obfuscated code was inserted within the package. This code would execute whenever the package was imported, affecting both Windows and Linux systems.
2. PowerShell in `setup.py`: This technique involved embedding PowerShell code in the `setup.py` file, which is automatically run by package managers like pip. It primarily targeted Windows systems, downloading and executing subsequent stages of the malware.
3. Pure Malware: In some cases, the package contained only malicious code in a lightly obfuscated form, forgoing any pretense of legitimacy.
The study also revealed sophisticated persistence mechanisms. On Windows, persistence was typically achieved via a VBScript Encoded file scheduled to run periodically. In contrast, Linux systems were compromised through a malicious desktop entry placed in the `~/.config/autostart/` directory, executing on each system startup.
Beyond the custom backdoor, the payloads varied. Some packages delivered the W4SP Stealer, while others implemented a clipboard monitor targeting major cryptocurrencies. This technique involved using the legitimate `pyperclip` package to monitor clipboard content for wallet addresses, which the malware would replace with attacker-controlled addresses.
ESET products have been updated to detect these malicious Python packages as variants of Python/Agent and Python/TrojanDownloader, and the backdoor as Python/Agent.AOY or Linux/Spy.Agent.BB. Most of these packages were taken down by PyPI at the time of the research, and ESET collaborated with PyPI to ensure the removal of any remaining malicious packages.
This revelation underscores the need for Python developers to thoroughly vet the code they download, especially checking for these tactics before installation. The abuse of PyPI by cyber attackers continues to evolve, posing a significant risk to both individual developers and larger organizations.





