PyPI Under Attack: Malicious Crypto-Stealing Packages Discovered
Checkmarx Zero, the research arm of Checkmarx, has uncovered a new wave of malicious Python packages infiltrating the popular PyPI repository. These packages, disguised as helpful tools for cryptocurrency wallet management, are designed to steal sensitive data, including private keys and mnemonic phrases, from unsuspecting users.
The malicious packages, with names like “AtomicDecoderss,” “TrustDecoderss,” and “Exodus Decodes,” target users of popular wallets such as Atomic, Trust Wallet, Metamask, Ronin, TronLink, and Exodus. These packages exploit the trust users place in open-source repositories and the perceived utility of wallet management tools.
The attackers employed a sophisticated strategy to deceive users and evade detection:
- Deceptive Naming and Documentation: The packages used names similar to legitimate tools and included professionally written README files with detailed instructions and fake popularity statistics to lure users into a false sense of security.
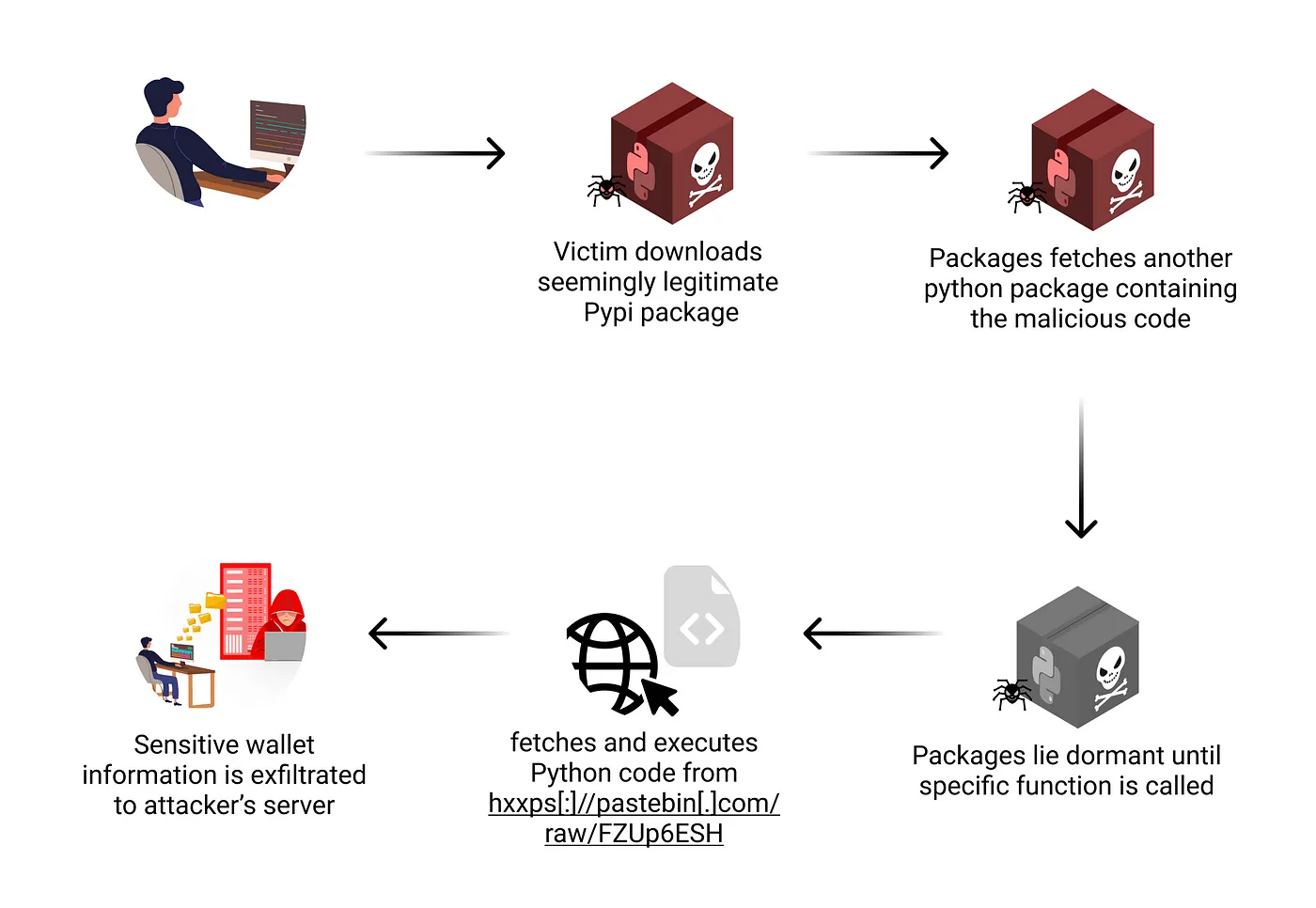
- Distributed Malicious Code: The core malicious code was hidden within dependencies, making the main packages appear harmless upon initial inspection and complicating the analysis process.
- Delayed Activation: The malicious code only activated when specific functions were called, not upon installation, further reducing the chances of early detection by security tools.
- Dynamic Command and Control: The address of the attackers’ command and control server was retrieved dynamically, making static analysis more difficult and allowing attackers to change their infrastructure without updating the packages.
The attacker behind this campaign left no detail untouched in their effort to deceive potential victims. Each package was accompanied by a professionally crafted README file, complete with installation instructions, usage examples, and even fabricated popularity metrics, such as download statistics. These tactics were designed to create an illusion of legitimacy and encourage unsuspecting users to trust and install the packages.
Upon installation, the malicious packages lay dormant until users attempted to access specific functions related to wallet recovery or data extraction. At that point, the malware would spring into action, accessing the wallet’s sensitive data such as private keys and mnemonic phrases. This data was then encoded and transmitted to a remote server controlled by the attacker.
The consequences for victims can be severe, including:
- Financial Loss: Attackers can use stolen private keys and mnemonic phrases to drain cryptocurrency wallets, resulting in irreversible financial losses.
- Ongoing Vulnerability: Compromised wallet data can lead to continued exploitation and monitoring by attackers.
- Expanding Threats: The ability to fetch external code allows attackers to dynamically update and expand their malicious capabilities, potentially introducing new threats or targeting additional assets over time.
Users should carefully scrutinize packages, including their dependencies, before incorporating them into their projects.
Checkmarx Zero has reported these malicious packages to PyPI, and they have been removed from the repository. However, it is crucial to remain cautious and take proactive steps to protect your cryptocurrency wallets and sensitive data.
For more detailed information on this attack and the specific packages involved, please refer to the Checkmarx Zero report.




