PySilon: A Discord Bot Turned Malicious RAT for Data Theft and Surveillance
In a recent report, cybersecurity firm AhnLab has highlighted a disturbing trend in which Discord Bots, initially designed for benign server management, have been weaponized to deploy Remote Access Trojans (RATs). The latest case involves the malware variant PySilon, a RAT that leverages the Discord Bot platform to infiltrate systems and harvest sensitive data.
Discord, once primarily a gaming hub, has grown into a platform where diverse communities communicate in real-time. AhnLab explains, “A Discord Bot is a program that automatically performs specific tasks on user-created servers, offering various features such as server management, automated message responses, game facilitation, music playback, and notification delivery.” However, PySilon distorts these functions to operate maliciously within the Discord infrastructure.
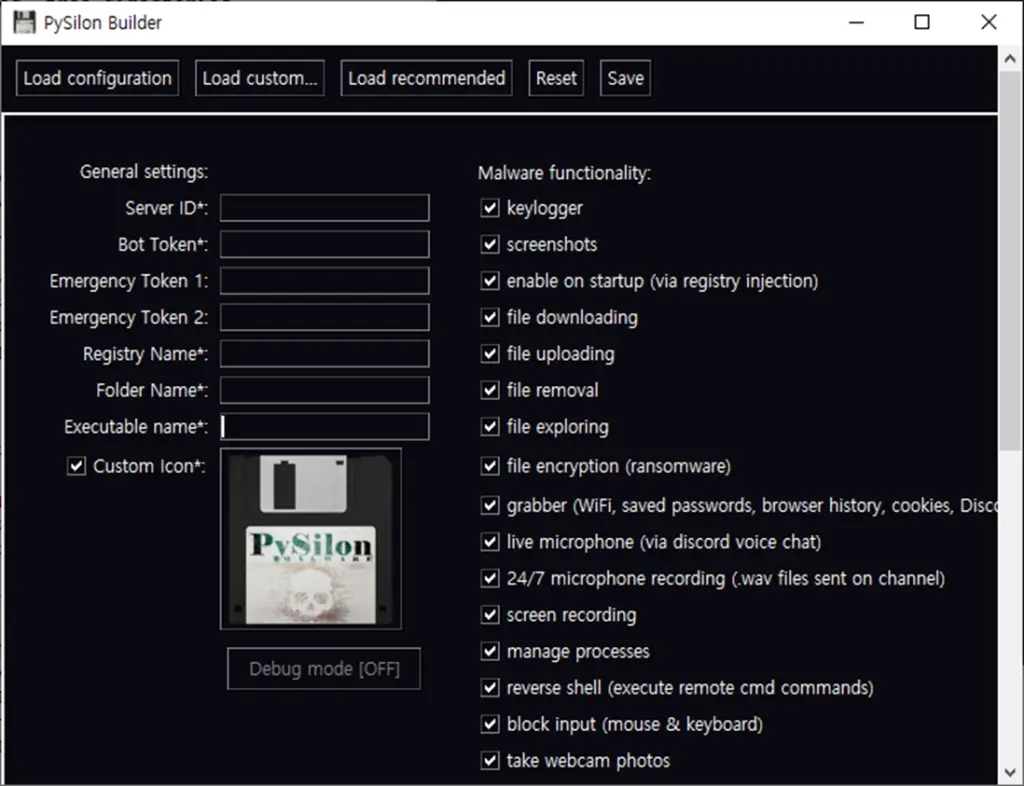
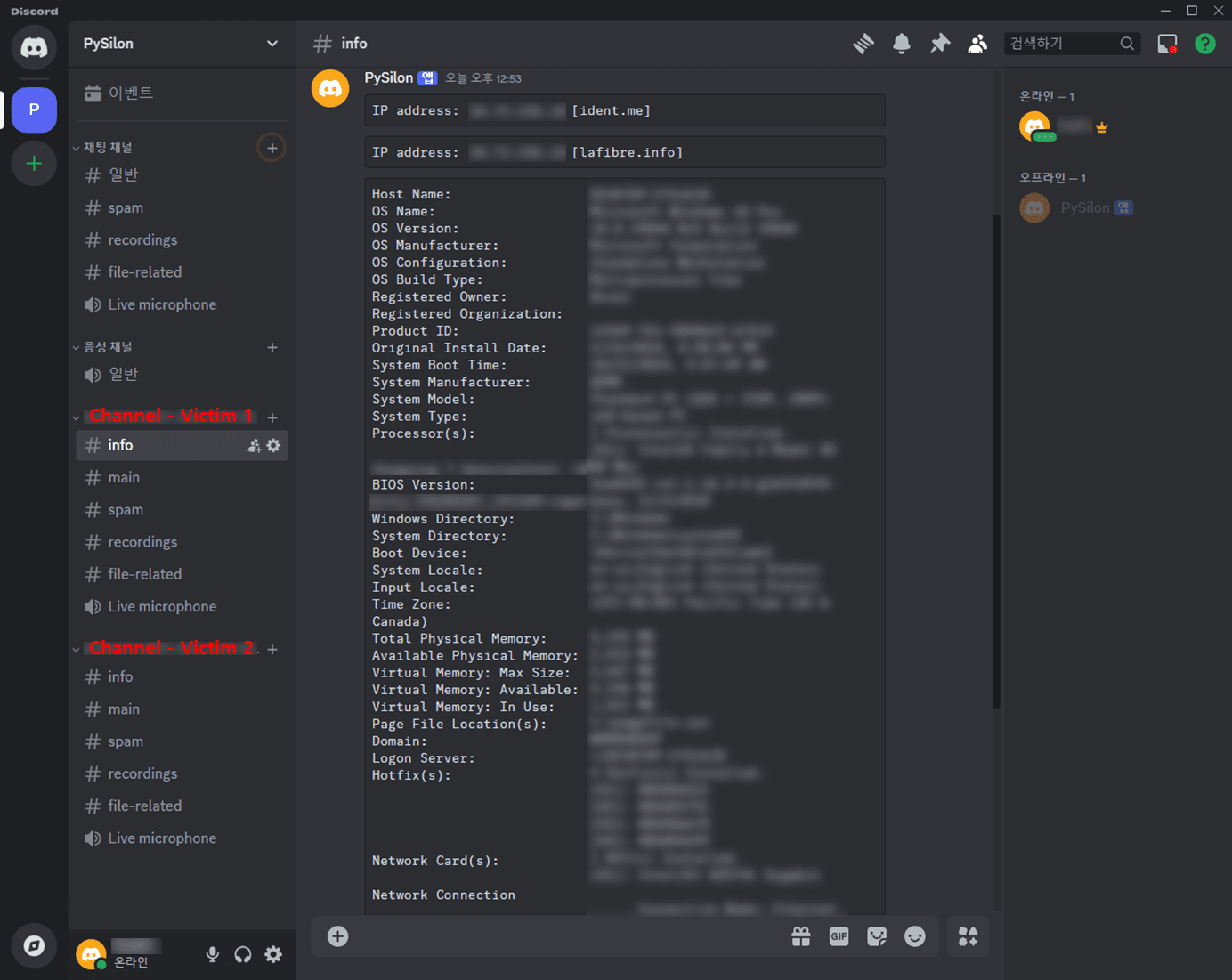
RAT malware builder program | Image: AhnLab
The RAT malware, developed using Python, is accessible on GitHub, making it simple for threat actors to build customized versions. By adjusting details like Server ID and bot token, attackers create a personalized malware build using a builder program. “The custom information is entered into the pre-implemented Python code, and it is converted into an executable file (.exe) using PyInstaller,” AhnLab reports, allowing attackers to generate files that seamlessly integrate with Discord servers.
Upon execution, PySilon creates a new channel within the attacker’s server to relay initial system information, such as IP addresses, to the operator. AhnLab notes, “A new channel is created for each PC infected by the bot, allowing the threat actor to control each infected PC individually,” giving hackers a persistent communication link with infected devices.
PySilon’s extensive range of commands reveals its utility for espionage, data theft, and sabotage. The malware enables attackers to perform functions such as:
- Collecting Personal and System Information: Through its “Grab” command, PySilon extracts Discord tokens, browsing history, cookies, and even payment information.
- Screen and Audio Recording: The malware can capture real-time screen and audio data, using modules like
pyautoguiandsounddevice, with recordings sent directly to the attacker’s server. - Keylogging: Every keystroke input is transmitted back to the attacker when users press “Enter,” enabling detailed monitoring of user activity.
- Folder Encryption: Using the Fernet algorithm, PySilon encrypts files in specified folders, saving the decryption key in a user-accessible directory, and appending a .pysilon extension without a ransom demand.
AhnLab highlights the challenge of detecting such threats, as “data is transmitted using official Discord servers implemented for normal bot functions,” obscuring its malicious nature. This use of legitimate channels makes detection difficult, as the transmission appears no different from standard bot communications.