R0bl0ch0n TDS – New Affiliate Fraud Scheme Impacts 110 Million Users
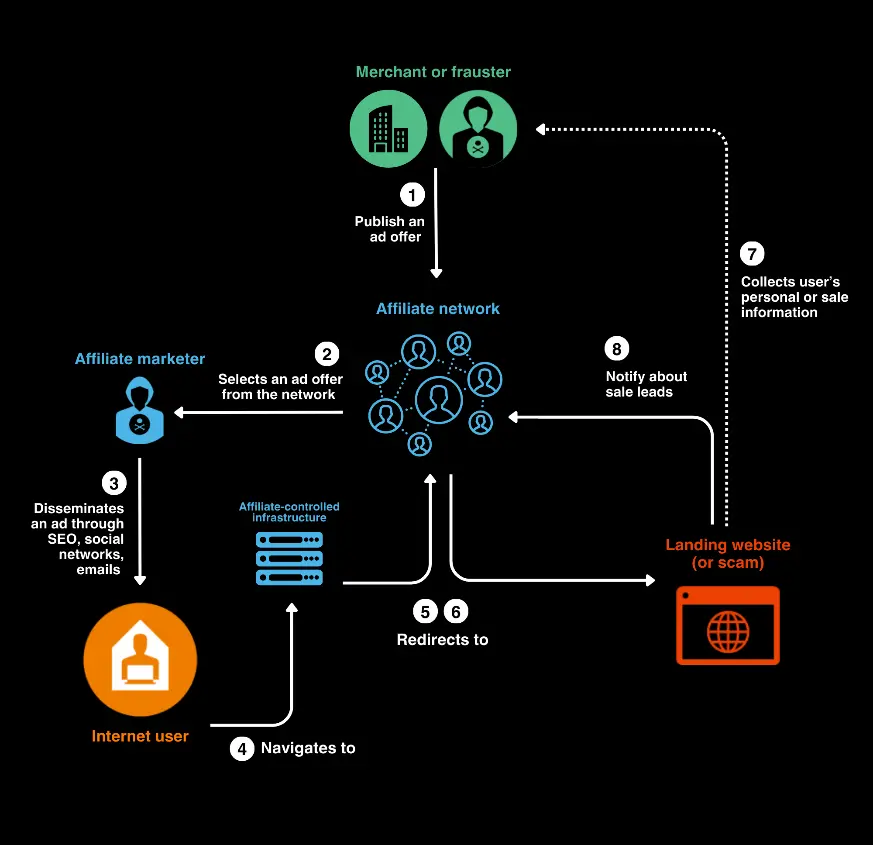
A team of specialists from World Watch has discovered a new Traffic Distribution System (TDS) closely linked to affiliate marketing and actively used in fraudulent schemes. This system, named R0bl0ch0n TDS due to the characteristic “0/0/0” sequences in URL redirects, has affected approximately 110 million internet users worldwide.
Affiliate marketing, typically a legitimate method for promoting goods and services, has been transformed into a tool for disseminating fraudulent advertisements in this case. Researchers have identified hundreds of small affiliate networks specializing in promoting suspicious offers leading to well-known scam schemes.
R0bl0ch0n TDS represents a sophisticated infrastructure comprising numerous domains and dedicated servers, securely protected by Cloudflare. Although the perpetrators have included some legitimate features in their campaigns, such as unsubscribe and feedback forms, they have taken significant measures to obscure the true organizations behind these operations.
A technical analysis of R0bl0ch0n TDS revealed that the URLs embedded in emails follow consistent patterns (<domain>/bb/[0-9]{18}). These links contain multiple automatic redirects, leading users to fake shops or survey pages. It is noteworthy that these URLs cannot be accurately analyzed by automated systems, as bypassing the fake CAPTCHA requires user involvement.
Experts discovered that domains hosting fake surveys actively exchange user data with third-party websites. For instance, the domain facileparking.sbs transmits information to event.trk-adulvion.com. This domain network began operating in the summer of 2021 and includes over 300 dedicated IP addresses on Amazon Web Services (AWS) servers.
According to DomainTools, the total number of A-type DNS requests for event subdomains since 2021 amounts to about 110 million. Given that only one DNS request is registered per user due to fingerprinting mechanisms, this figure reliably reflects the total number of people targeted by these fraudulent schemes.
Researchers identified two main categories of fraudulent offers distributed through R0bl0ch0n TDS:
Prize Draws:
- Attractive messages about winning a lottery.
- After completing a short online survey, users are asked to pay a small shipping fee.
- In reality, this enrolls them in a subscription for regular payments (from 20 to 45 euros every two weeks).
- The US Federal Trade Commission reported complaints totaling over $300 million in losses, with an average loss of $900 per person.
- World Watch experts believe the actual figures are significantly higher, considering the vast number of campaigns sent out daily.
Home Improvement Offers:
- Advertisements for overpriced services such as gutter filters, solar panels, heat pumps, or walk-in showers for the elderly.
- These schemes are often spread through email and/or promoted using search engine optimization (SEO).
- Affiliates earn a commission each time a user fills out a contact form.
- Subsequently, a “salesperson” calls the potential client.
- Often, sellers deliberately inflate the amount of government subsidies the client may be eligible for.
Various methods are employed for the initial distribution of URLs redirected through R0bl0ch0n TDS:
- Using random AWS subdomains with data in the URL fragment part, which is passed to R0bl0ch0n TDS and likely linked to affiliate program parameters.
- Using random Azure subdomains with URLs matching the pattern <random_subdomain>.blob.core.windows.net/<random_subdomain>/1.html. Data in the URL fragment is also passed to R0bl0ch0n TDS.
- Using URL shortening services.
Experts note that leveraging legitimate services such as AWS or Azure infrastructure or URL shorteners allows affiliates to easily modify and deploy new infrastructure. This helps them circumvent detection systems and countermeasures implemented in Google Safe Browsing or anti-spam filters.
Related Posts:
- Unit 42 Exposes Parrot TDS: A Global Malware Menace
- BlackTDS: new Traffic Distribution System
- BattleRoyal Cluster: A DarkGate Contender Rises with Devious Tricks and Evolving Tactics
- Uncovering Deceit: Strategies for Unearthing Fraudulent Activity
- “The Com” Phishing Attacks Escalate, Targeting Businesses with Fake Login Pages





