Ransomware Cipher Crime: Encryption Used Maliciously

Credit: gregorly via Canva
Ransomware from Several Perspectives
Ransomware has many facets and angles to explore. Let’s explore it from a general, technical, personal and monetary perspective. Then let’s perhaps dive into how some of these different angles interrelate.
Generally Speaking
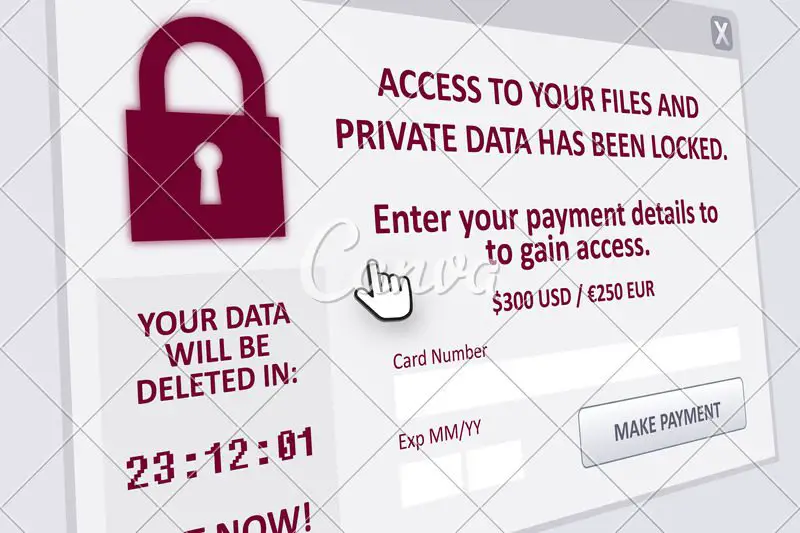
Ransomware is a malicious application that renders user or business data inaccessible with the ultimate goal of receiving ransom payments from its unsuspecting cyber victims.
Encryption in History
Encryption was used 2000 years ago by the Romans on the battlefield used an encryption algorithm called substitution cipher developed by Caesar. Caesar needed a way to send documents to his troops in remote locations while ensuring only its intended recipients would be able to understand the text.
Digital encryption has been in existence for several decades, going back to the 1970s. At that time, IBM started protecting their customers’ data using encryption.
Encryption used for Cybercrime
Cybercriminals are just using something that is generally a valid solution to protect the privacy and sensitivity of digital information and turn it into a tool to commit a malicious cybercrime/cyber theft.
Root Cause: Complacency
We could safely assume that most ransomware victims did not use anti ransomware or other cybersecurity-related products such as antivirus and malware protection solutions. Once a ransomware attack occurs, many cyber victims have no other choice but to give in and pay ransom to regain access to their data.
Cyber ransomware will typically encrypt personal and enterprise-grade data. Once the encryption is complete and verified, a ransom for that data depends on the value deemed. A high-pressure ultimatum often comes attached with the ransom request.
In the next section, we will take a deeper dive into the technical side of encryption which is at the core of a ransomware attack. Cryptocurrencies have made it even easier for cyber gangs to remain elusive and evade the law. Crypto ransom has made it much more challenging and often near impossible to track by law enforcement.
Technically Speaking
Encryption, which is at the heart of a ransomware cyberattack, is a process of encoding data into a series of letters, numbers and other characters, which essentially renders a coherent piece of data into gibberish.
Data at Rest and Data in Transit
Encryption protects sensitive documents by organizations and regular end-users, and it falls under two different categories, data at rest and data in transit. Data at rest could be data in a hard drive, and data in transit is any data that travels over digital communication channels, such as a peer-to-peer chat.
Another example of data at rest encryption is when a password is on a Microsoft Word document. What happens is that the file becomes scrambled with indiscernible ciphertext or a series of random characters.
Essentially the password, in this case, is the key that can unlock the data. Encryption can take place for a much larger batch of data, including encrypting an entire physical hard drive at the hardware level.
This process converts the original representation of the information, known as plaintext, into an alternative form known as ciphertext. Ideally, only authorized parties can decipher a ciphertext back to plaintext and access the original information.
Encryption Protocols and Keys
Encryption protocols use encryption algorithms to scramble the text into set-sized blocks, which can be 56 bits, 128 bits and more in size. These algorithms used advanced mathematical functions to perform their operations and then create a key. The same key is generally needed to decrypt the data with a symmetric encryption protocol, and Asymmetrical protocols require public and private keys.
Some of the most popular encryption protocols are DES and AES, which stand for Data Encryption Standard and Advanced Encryption Standard.

Credit: mantejmo via Canva
The Key is in the Key Size
Theoretically, a brute force attack could guess a given algorithm key by guessing all of its possible respective keys. This is why the key length of a given encryption algorithm makes a massive difference.
For example, a 56 bit DES cipher encryption algorithm could be hacked in 1 hour with a supercomputer, and 128 bit AES cipher encryption algorithm could take 5.3 x 1017, which is 5.3 times almost a QUINTILION YEARS or 5.3 x 100000000000000000 YEARS for a supercomputer to hack. This is not even close to other bigger key lengths out there.
Imagine how much time it would take for an organization to guess the key to deciphering their data. Actually, don’t bother, it is UNIMAGINABLE.
Monetarily Speaking
In 2020, an estimated $18 billion was paid out as a result of ransomware cyber-attacks by businesses and home users, and this number is expected to grow.






