Recox: Master script for web reconnaissance
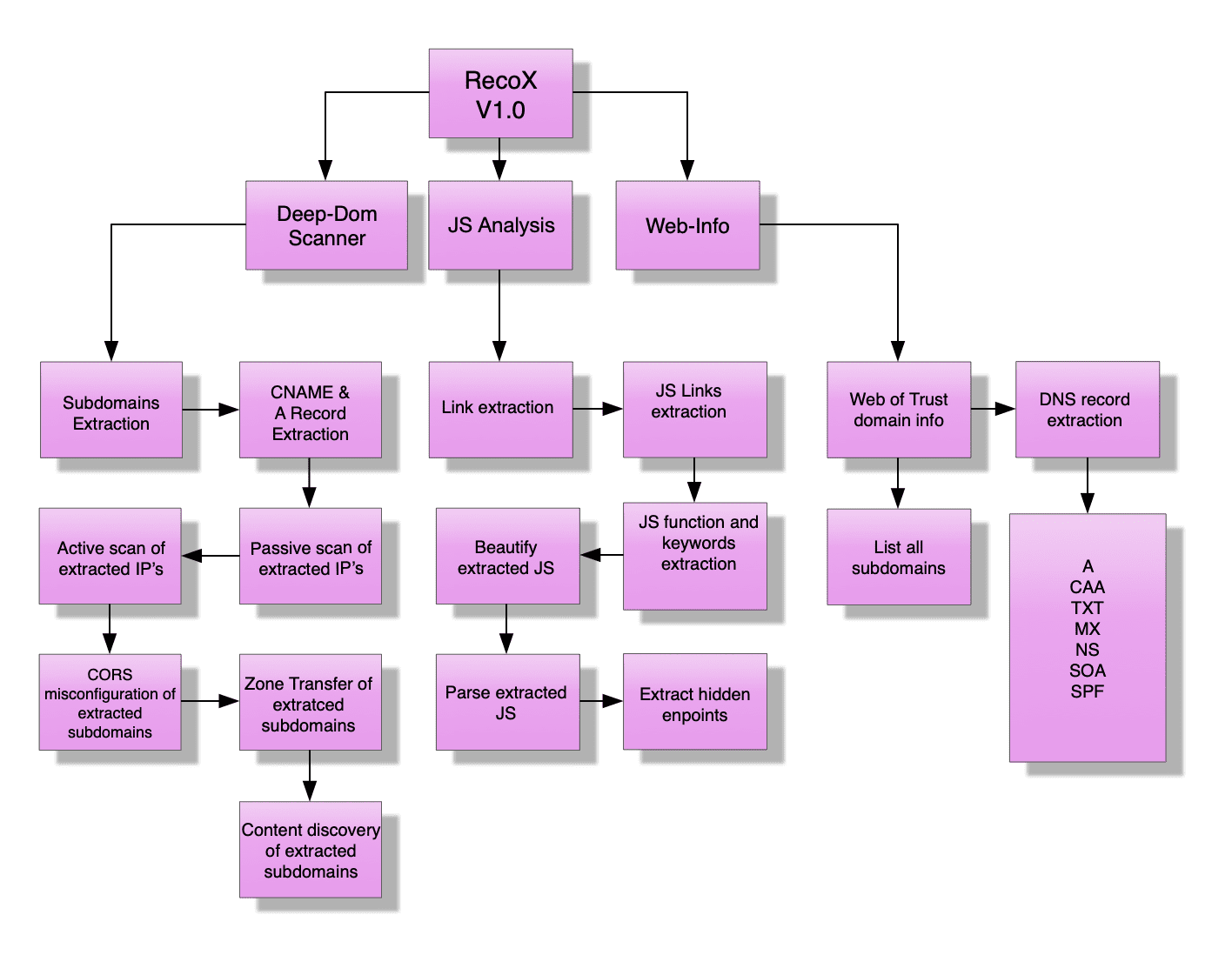
Recox v1.0
The script aims to help in classifying vulnerabilities in web applications. The methodology RecoX is arising can spot weaknesses other than OWASP top ten. The script presents information against the target system. It gathers the information recursively over each subdomain and IP addr for a sophisticated attack. RecoX automates several functions and saves a significant amount of time that requires throughout a manual penetration test.
The deep scanner comprises many check-ups including subdomain takeover, A record, passive scan, active scan, CORS misconfiguration, zone transfer test, and web content discovery. 
- Deep-Dom Scanner
The deep scanner comprises many check-ups including subdomain takeover, A record, passive scan, active scan, CORS misconfiguration, zone transfer test, and web content discovery. - Subdomain Takeover
The subdomain takeover is a process in which a subdomain points to an external non-existing domain where attacker registers the non-existing domain to take over the subdomain. The DNS misconfiguration enables an attacker to gain full authority across subdomains leading to providers such as Heroku, Github, Bitbucket. The web becomes vulnerable if DNS entries pointed to an external service provider and are not in use. The misconfiguration enables unverified users to claim the non-existing subdomain from an external service provider in order to serve content for personal and financial gain (Detectify Labs, 2014). RecoX obtains all subdomains related to the main domain by using the VirusTotal API (Application Programming Interface). The script starts extracting the CNAME record for each subdomain to check which external service the subdomain is pointing. It displays all the CNAME record for each subdomain and then asks if user want to check against subdomain takeover vulnerability. - For more detail please read this document.
Download
git clone https://github.com/samhaxr/recox
chmod +x recox.sh
mv recox.sh /usr/local/bin/recox
Use
./recox.sh
Copyright (C) 2020 samhaxr
Source: https://github.com/samhaxr/





