Researcher details Oracle JDeveloper ADF Faces RCE (CVE-2022-21445)
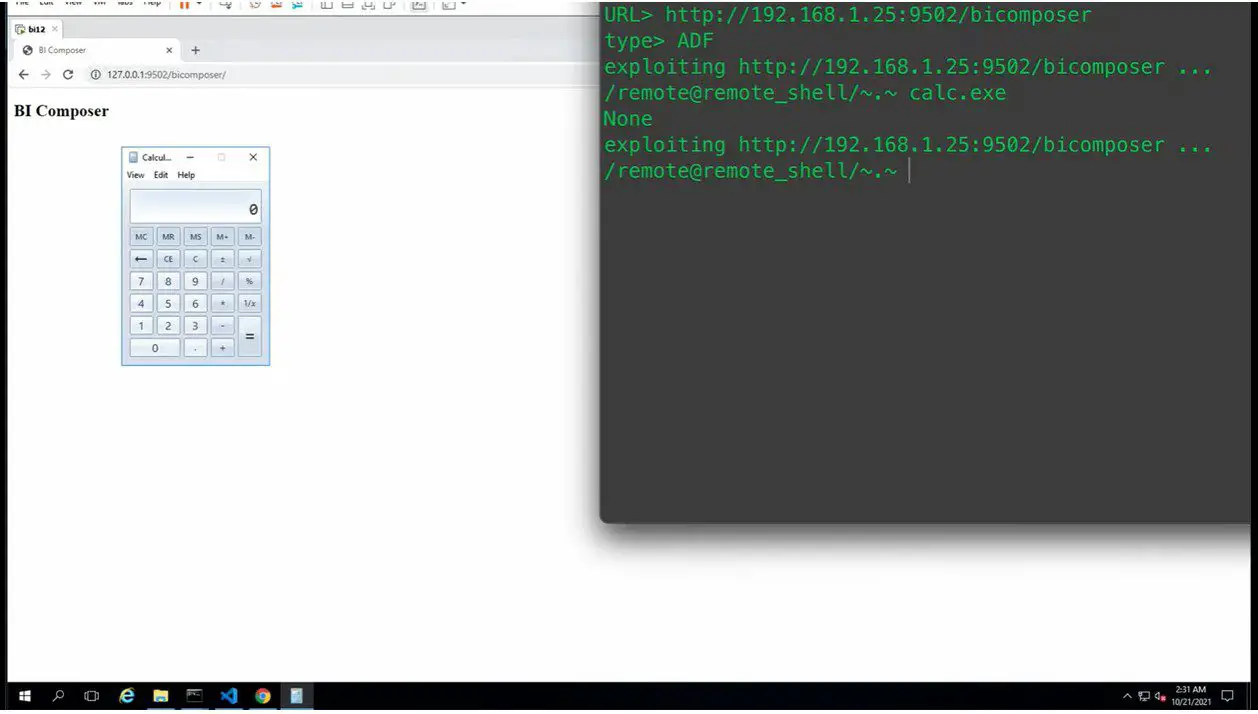
CVE-2022-21445 PoC (proof-of-concept) exploit code is about to be published for a vulnerability that allows an attacker to gain remote code execution on the server-side, and eventually, take over the server.
Oracle released patches for CVE-2022-21445 in its April 2022 Critical Patch Update. It also has the highest CVSS score (9.8) and severity (Critical). Supported versions that are affected are 12.2.1.3.0 and 12.2.1.4.0. This flaw exists in the ADF Faces component, it is the deserialization of untrusted data that could lead to arbitrary code execution. The weakness was reported by Jangggg and peterjson.

The easily exploitable vulnerability allows unauthenticated attackers with network access via HTTP to compromise Oracle JDeveloper.
This bug impacts all applications that rely on ADF Faces, including Business Intelligence, Enterprise Manager, Identity Management, SOA Suite, WebCenter Portal, Application Testing Suite, and Transportation Management.
Security researcher peterjson announced recently that he managed to create a working CVE-2022-21445 PoC exploit code and released a technical report.
“Now after a period of time after Oracle released the patch, we decided to publish this blog to share the detail of Miracle exploit. We were very very excited at the time (6 months ago), but now we don’t have that feeling anymore because Oracle took too long to patch this vulnerability, more than the standard.” reported the security duo in a blog post. “Anyway, this is a cool exploit, a cool story me and Jang worked together in a month so let us tell you about our story.”





