Researcher details the CVE-2022-26809 PoC
CVE-2022-26809 PoC (proof-of-concept) exploit code is about to be published for a vulnerability that allows an attacker to gain remote code execution on the server-side.
Microsoft released patches for CVE-2022-26809 in Microsoft’s April 2022 Patch Tuesday, reportedly a zero-click exploit targeting Microsoft RPC services. It also has the highest CVSS score (9.8) and severity (Critical). This flaw exists in the Windows Remote Procedure Call Runtime library impacting all supported Windows products.
Microsoft Remote Procedure Call (RPC) defines a powerful technology for creating distributed client/server programs. The RPC run-time stubs and libraries manage most of the processes relating to network protocols and communication. This enables you to focus on the details of the application rather than the details of the network.
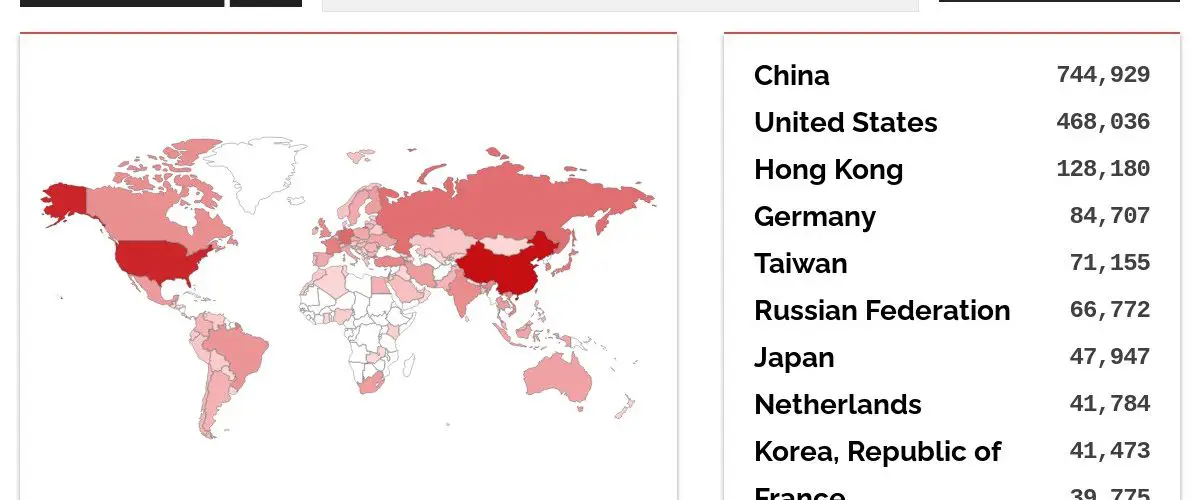
Microsoft evaluates that CVE-2022-26809 has a low attack complexity and needs no privileges and no user interaction. These features could make the vulnerability potentially wormable. Windows machine where port 445 is exposed and the RPC runtime library is not patched is vulnerable. The number of hosts exposed on different ports (based on Shodan.io) shows that over 2 million Microsoft machines appear potentially exposed.
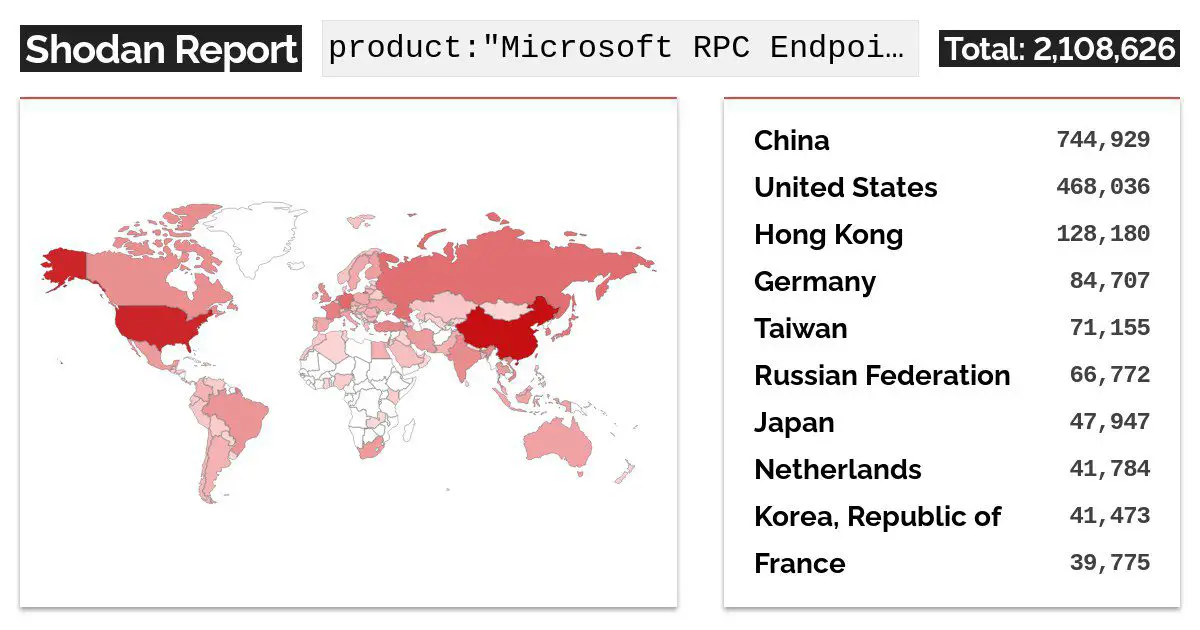
Image: TodayCyberNews
Security researcher s1ckb017 announced recently that he managed to create a working CVE-2022-26809 PoC exploit code and released a technical report. He said:“The PoC has not been fully tested, because it should trigger the vulnerability, i.e integer overflow, that leads to a buffer overflow on the heap is reached after 1048576 packets sent, because 1048576*4096 overflow integer of 32 bits.”
Microsoft recommends that
Although blocking ports 139 and 445 [SMB] at the perimeter firewall is a recommended practice, it does not directly protect against all potential attack scenarios for this specific vulnerability. At this time we are not aware of any other specific attack vectors for this vulnerability, and continue to encourage users to:
- Apply the April 2022 security updates to fully address this issue.
- Follow Microsoft guidelines to secure SMB traffic. See Secure SMB Traffic in Windows Server.