Researcher Releases Techniques & Burp Extension to Help Bypass WAFs
In the cybersecurity field, web application firewalls (WAFs) are pivotal in defending web applications from malicious attacks. However, recent insights from Shubham Shah, a seasoned security researcher and co-founder of Assetnote, reveal significant limitations in WAFs, highlighting innovative bypass techniques. Shah’s presentation, “Modern WAF Bypass Techniques on Large Attack Surfaces,” delves into these vulnerabilities, providing valuable strategies for security professionals and bug bounty hunters.
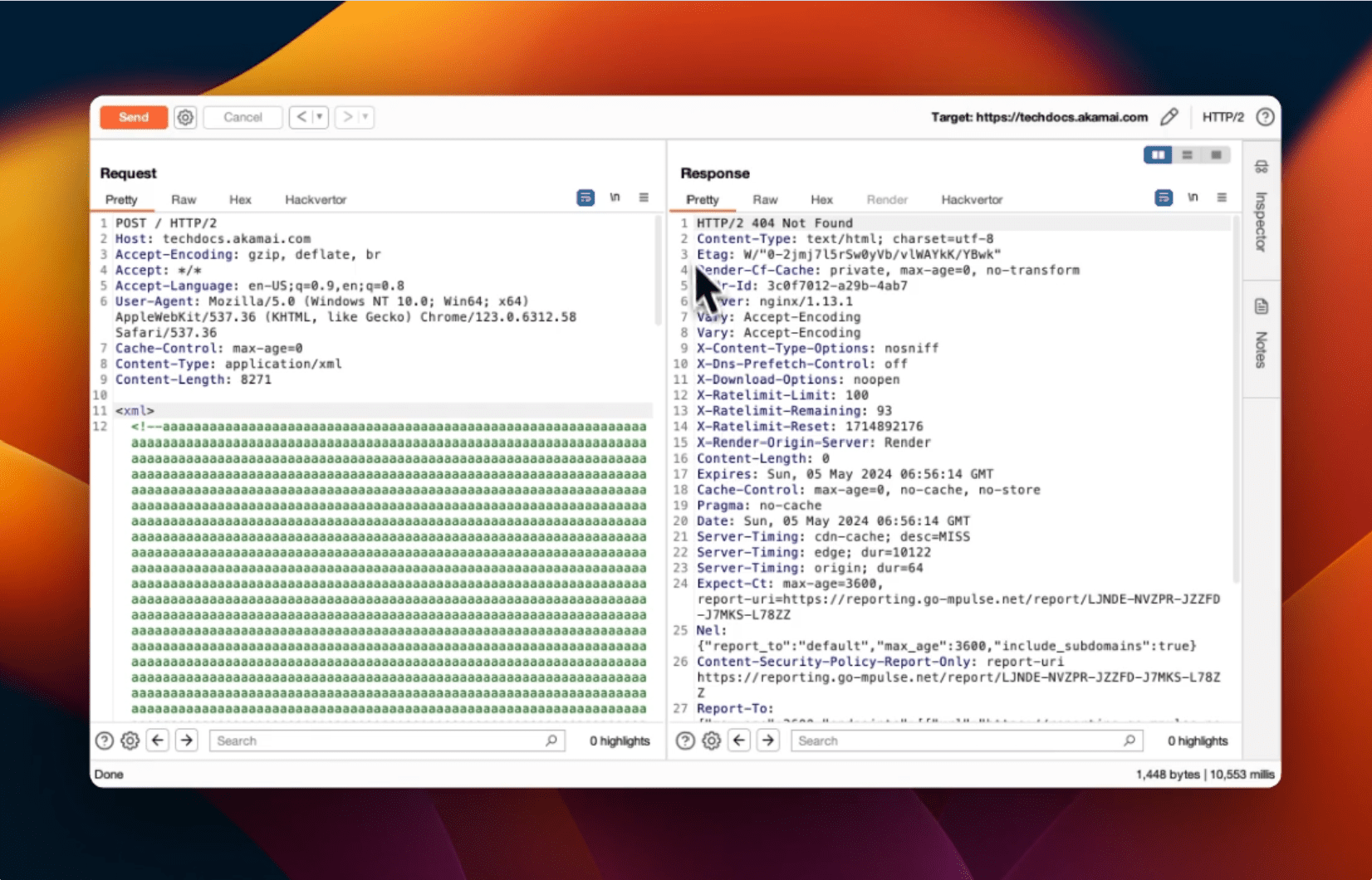
WAF blocked the payload
Shah emphasizes a pragmatic approach to WAF bypassing. Contrary to complex and meticulously crafted payloads, Shah advocates for simple and effective methods. His philosophy centers on the idea that easy bypasses are often the most effective, encouraging a mindset and methodology that avoid unnecessary complexities.
One of the critical vulnerabilities Shah highlights is the request size limits inherent in most WAFs. When processing HTTP requests with a body (such as POST, PUT, PATCH), WAFs typically inspect only a limited amount of the body content due to performance constraints. This limitation can be exploited by padding the request with junk data, allowing the malicious payload to bypass WAF inspection if it exceeds the WAF’s inspection limit.
For instance, the AWS WAF can inspect up to 8 KB for Application Load Balancer and AWS AppSync protections, and up to 64 KB for CloudFront, API Gateway, Amazon Cognito, App Runner, and Verified Access protections. By strategically padding requests to exceed these limits, attackers can effectively bypass the WAF.

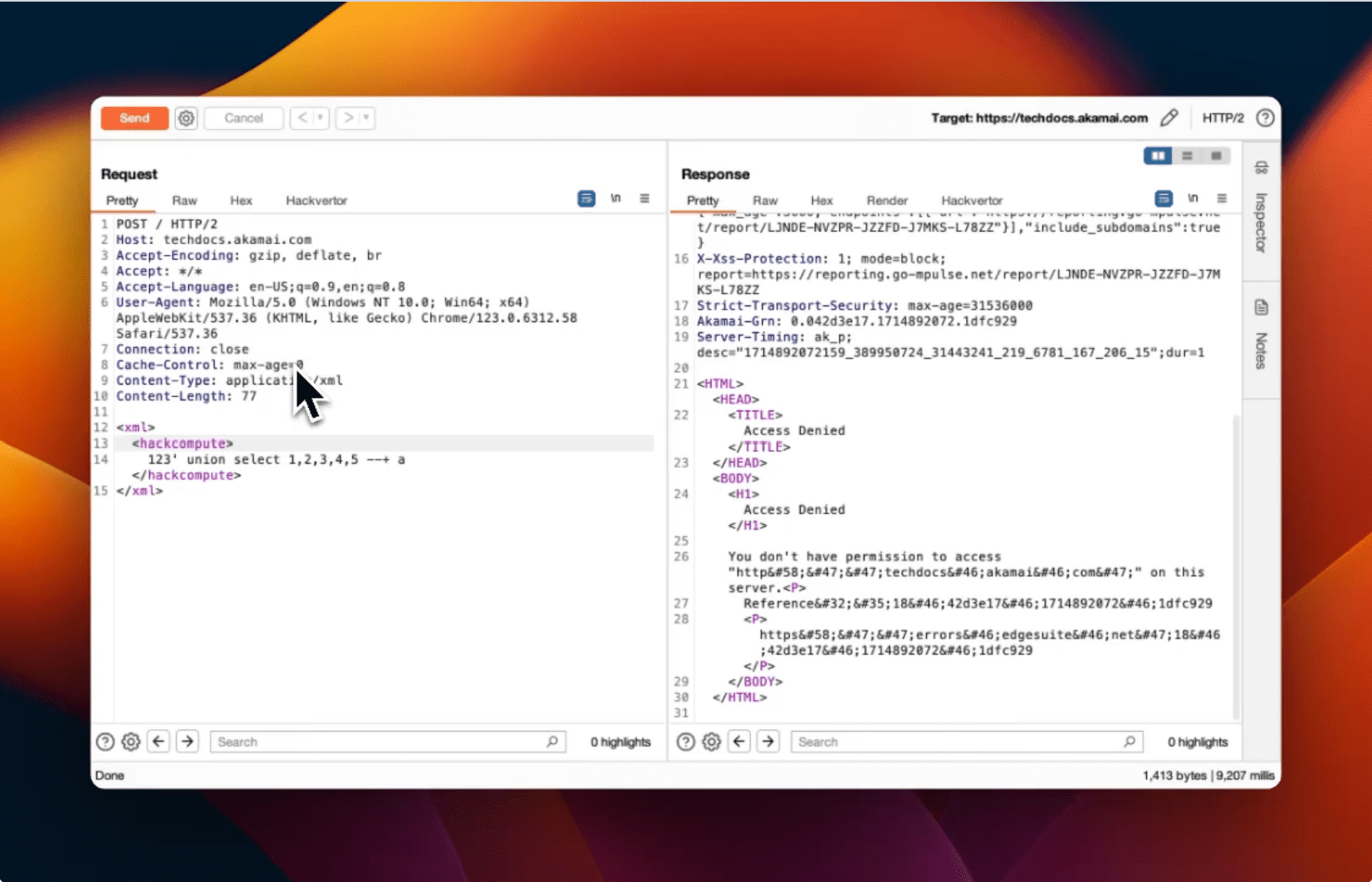
Bypass WAF with nowafpls Burp plugin
To facilitate this bypass technique, Shah introduces a new tool: the nowafpls Burp plugin. This plugin helps security professionals and bug bounty hunters by automatically inserting junk data into HTTP requests within Burp Suite’s repeater tab. It contextually detects the content type (XML, JSON, URLEncoded) and inserts appropriate junk data. Users can choose from preset amounts of junk data or specify a custom amount.
- For XML: Inserts a comment like
<!--a*bytes--> - For JSON: Inserts a junk key-value pair like
"a":"a*bytes" - For URLEncoded: Inserts a junk parameter and value like
a=a*bytes
The nowafpls plugin simplifies the process of padding requests, making it easier to bypass WAFs without manually altering payloads.
With tools like nowafpls and a straightforward approach to WAF bypassing, security professionals and bug bounty hunters are better equipped to navigate and exploit vulnerabilities in heavily protected systems. As WAFs continue to evolve, so too must the strategies and tools used to test and ensure the security of web applications.